iCloud Calendar Is Being Exploited to Send Phishing Emails from Apple’s Servers

Invitations sent through iCloud Calendar are being weaponized to deliver phishing emails disguised as purchase notifications—sent directly from Apple’s own mail servers. This tactic significantly increases the chances of bypassing spam filters.
A Familiar Scam with a New Twist
According to Bleeping Computer, a reader recently shared a malicious email that appeared to be a $599 PayPal receipt. The email included a phone number, supposedly for disputing the payment.
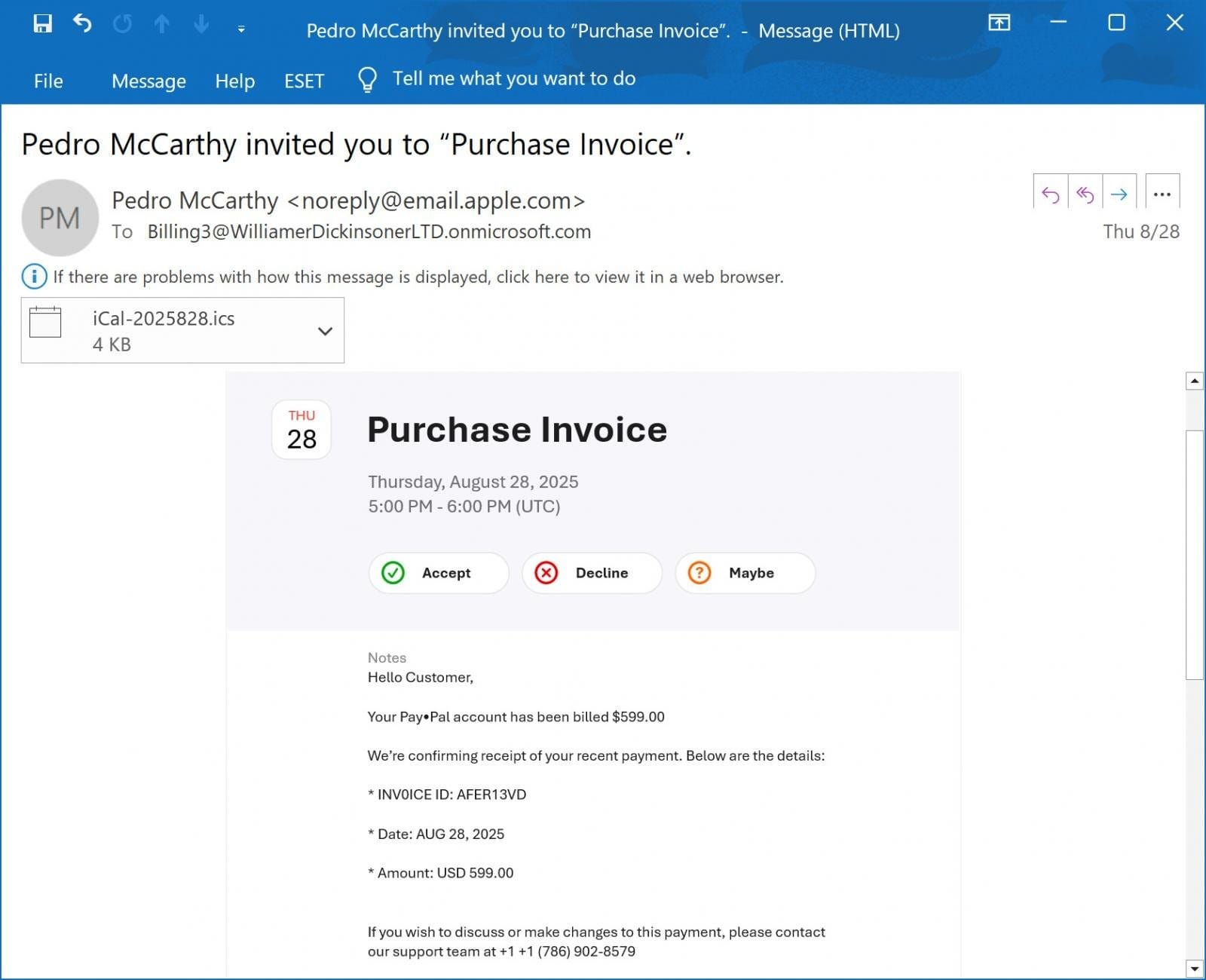
The goal is classic phishing: scare the victim into believing their PayPal account has been hacked and push them to call a fake “support” line. Once on the call, scammers escalate the fear, claiming the account is compromised. They then persuade the victim to allow remote access “to issue a refund” or convince them to download software. In reality, the attackers use this access to steal funds, install malware, or harvest sensitive data.
What makes this case unusual is the source of the email. The message came from [email protected] and successfully passed SPF, DMARC, and DKIM authentication checks—proof that it was legitimately sent from Apple’s servers.
How Attackers Abuse iCloud Calendar
The fraudulent email was not a traditional message but an iCloud Calendar invitation. The attackers inserted their phishing text into the “Notes” field of an event, then invited a Microsoft 365 account under their control.
When iCloud Calendar events invite external participants, Apple automatically sends the invitation from [email protected] on behalf of the organizer. This mechanism allowed the malicious email to originate from Apple’s infrastructure and appear trustworthy.
The specific invitation observed by Bleeping Computer was addressed to a Microsoft 365 account—[email protected].
Linking to Earlier Campaigns
Researchers say this attack resembles a campaign first spotted in spring 2025. In both cases, the invitation was sent to a Microsoft 365 address that functioned as a mailing list, forwarding the phishing message to all group members.
Normally, such forwarding would break SPF authentication. However, Microsoft 365 uses Sender Rewriting Scheme (SRS), which rewrites the return path to a Microsoft-associated address. This adjustment ensures the email still passes security checks—even though the original content is malicious.
Why It Works
On its own, the phishing content was unremarkable. What makes this scheme effective is the abuse of a trusted platform. Because the invitation originates from Apple’s servers, spam filters are more likely to treat it as safe.
Apple’s Response
Bleeping Computer reporters have notified Apple of the abuse. As of now, the company has not publicly responded.