Vulnerabilities Found in Airoha Bluetooth Chipsets Used in Dozens of Audio Devices

Security researchers have uncovered multiple vulnerabilities in Airoha Bluetooth chipsets, widely used in audio devices from brands like Sony, Bose, Jabra, JBL, and more. These flaws open the door to eavesdropping, unauthorized commands, and potential data theft.
Researchers at ERNW identified three key vulnerabilities in Airoha’s system-on-chip (SoC) modules, which are especially prevalent in True Wireless Stereo (TWS) earbuds.
At least 29 devices have been confirmed affected, including wireless microphones, headphones, headsets, and speakers from well-known brands such as Beyerdynamic, Marshall, MoerLabs, Teufel, and EarisMax. While the vulnerabilities require an attacker to be within Bluetooth range, they could allow unauthorized access to media playback, call data, or even initiate calls.
The vulnerabilities are tracked as follows:
- CVE-2025-20700 (CVSS 6.7): Missing authentication for GATT (Generic Attribute Profile) services
- CVE-2025-20701 (CVSS 6.7): Lack of authentication for Bluetooth BR/EDR
- CVE-2025-20702 (CVSS 7.5): Flaws in a custom protocol that could enable more severe exploits
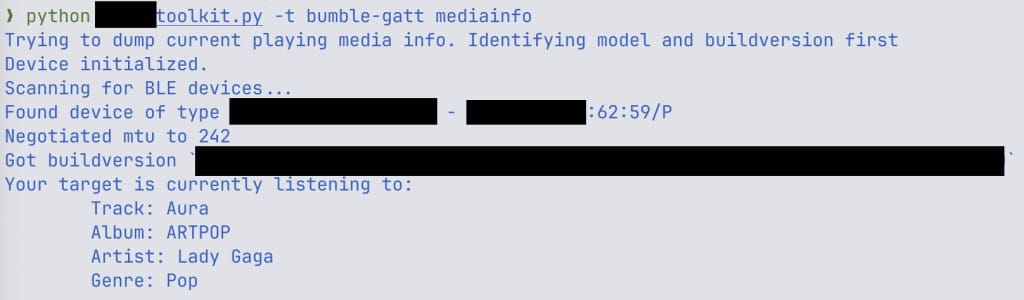
At the TROOPERS security conference, researchers demonstrated a proof-of-concept (PoC) that allowed them to capture live media streams from compromised earbuds. They also described scenarios in which an attacker could intercept Bluetooth connections or abuse the Hands-Free Profile (HFP) to issue commands to a connected smartphone.
“The available commands depend on the mobile OS, but all major platforms support at least initiating and accepting calls,” the researchers said. They demonstrated this by extracting Bluetooth pairing keys from memory and successfully making a call to a number of their choosing.
Depending on device configuration, an attacker could also access a user’s call history and contacts. More disturbingly, they could initiate a call and listen in on conversations within range of the microphone.
In theory, an attacker could even overwrite firmware to achieve remote code execution—potentially turning the device into a carrier for a worm-like exploit capable of infecting other gadgets.
While such attacks are technically challenging and require a high degree of skill, the implications are significant.
Airoha has released an updated SDK (Software Development Kit) addressing all three issues. Device makers have begun rolling out patches, but as reported by German tech outlet Heise, many devices still run firmware dated May 27, 2025, or earlier—predating the SDK release on June 4, 2025.




