Steam Serves Gamers Viruses with a Side of "Early Access"
This marks the third malware-laced game to appear on Steam in just six months.
A hacker group operating under the alias EncryptHub, also known as Larva-208, has embedded malicious software into a Steam-distributed game—turning a survival crafting title into a silent delivery mechanism for spyware.
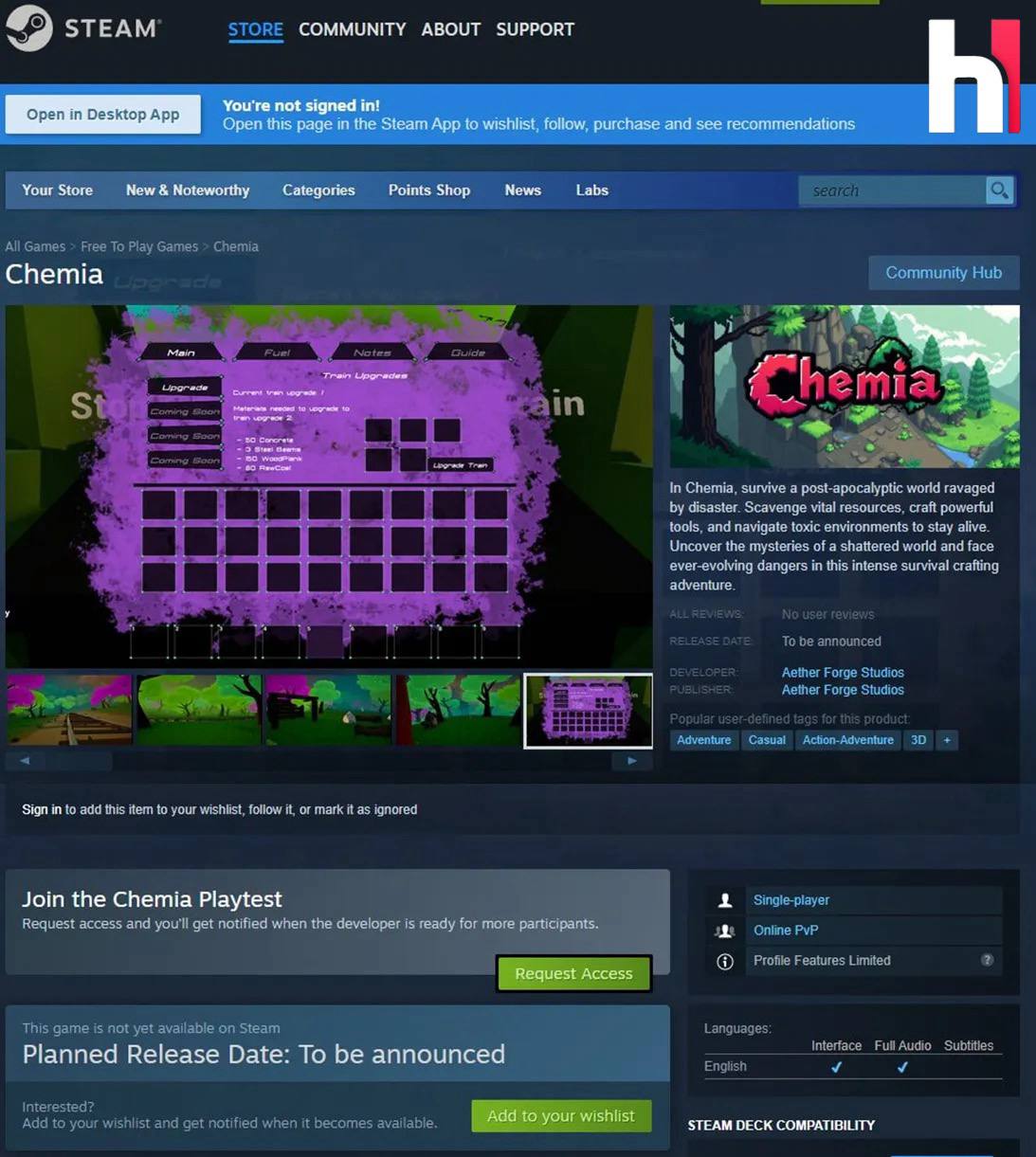
The Target: Chemia by Aether Forge Studios
The attack centered on Chemia, an early-access survival game with no official release date. A few days ago, attackers injected malware directly into the game files—undetected by players and without affecting gameplay performance.

According to cybersecurity firm Prodaft, the breach occurred on July 22, when a file named CVKRUTNP.exe—a variant of the HijackLoader—was added to Chemia’s installation package. This file is executed at game launch, allowing the malware to persist and deliver the next stage of the attack: Vidar spyware (v9d9d.exe), a well-known stealer of sensitive data. The malware receives commands from a remote server whose address is distributed via a Telegram channel.
Three hours later, the attackers added another payload: a library named cclib.dll. This module triggers a PowerShell script (worker.ps1), which connects to soft-gets[.]com to download the primary payload—Fickle Stealer. This spyware is capable of harvesting passwords, browser autofill data, cookies, and cryptocurrency wallets stored on the infected device.
Recycled Malware, New Vector
This isn’t EncryptHub’s first outing. The group has previously deployed this exact malware combination in large-scale social engineering campaigns targeting over 600 organizations worldwide. Notably, the group has a dual persona—while exploiting zero-day Windows vulnerabilities, they have also reported critical flaws to Microsoft under responsible disclosure.
In this case, the deception is simple yet effective. As Prodaft notes, clicking Steam’s Playtest button—typically reserved for demos and pre-release builds—doesn’t launch a harmless preview. Instead, it triggers a full-fledged Trojan, cleverly disguised as part of the game. Since Chemia installs and runs normally, users are unlikely to suspect foul play.
Researchers emphasize the stealth of the attack: the malicious code doesn’t degrade performance or interfere with gameplay. That level of invisibility makes the infection particularly dangerous. It remains unclear how EncryptHub gained access to the game’s Steam build—though an insider threat has not been ruled out. Neither Valve nor Aether Forge Studios have issued official statements despite multiple media inquiries.
Game Still Live, Risk Still Present
At the time of writing, Chemia is still available for download on Steam. It’s unknown whether the malicious components have been removed. Until Valve or the developer confirms a clean version, users are strongly advised not to install the game.
A Pattern Emerges
This is the third known case of malware infiltrating early-access titles on Steam in 2025:
- PirateFi (February)
- Sniper: Phantom’s Resolution (March)
- Chemia (July)
All three cases involved early-access games, suggesting that these projects may face fewer security audits or more lenient publishing processes.
Key Takeaways:
- A malicious version of Chemia included HijackLoader, Vidar, and Fickle Stealer spyware.
- The malware executes silently upon launch, using PowerShell and UI automation for stealth.
- Users trusted the Playtest system, unaware they were running active malware.
- Valve and the developers have not responded to inquiries; the game remains live on Steam.
- Gamers should be cautious with early-access titles, especially free or unverified games.




