Spy App Catwatchful Exposes Data of 62,000 Users
A security researcher has uncovered a critical vulnerability in the Android spyware app Catwatchful, marketed as a parental control tool. The flaw exposed sensitive data belonging to over 62,000 users, including plain-text email addresses and passwords.
Although positioned as a monitoring solution, Catwatchful fits the classic definition of stalkerware—a type of spyware designed to covertly track users. The app grants remote access to virtually everything on a victim’s device: messages, call logs, photos, real-time microphone and camera feeds, GPS location, and more.
As is common with spyware, the app operates silently in the background, hiding its icon and activity to avoid detection and removal.
“Yes, you can monitor the target phone without their knowledge using mobile monitoring software. The app is invisible and undetectable on the phone. It operates covertly in stealth mode,” claim the app’s developers.
After signing up, users receive a pre-configured APK (Android Package Kit) linked to their account credentials. Installation, however, requires physical access to the target device. Once installed, the app activates real-time surveillance capabilities.
A Serious Security Oversight
Cybersecurity researcher Eric Daigle found that Catwatchful functions exactly as advertised—remaining invisible while streaming data to a Firebase database accessible through a web control panel.
But Daigle also discovered a major flaw: the app was vulnerable to SQL injection attacks. More alarmingly, the API lacked any authentication, allowing unauthorized access to backend data, including:
- Plain-text login credentials for all 62,050 registered accounts
- Device-to-user binding records
- Surveillance data harvested from 26,000 victim devices
Many compromised devices were traced to countries including Mexico, Colombia, India, Peru, Argentina, Ecuador, and Bolivia. Some infections had been active since as early as 2018. According to Daigle, the exposed data could have been used to hijack any active account.
Developer Unmasked
The vulnerability also led to the identification of Catwatchful's creator: Omar Soca Charcov of Uruguay. His name, phone number, email address, and other personal details were among the exposed records.
Following Daigle’s disclosure, Google updated Play Protect—its built-in Android malware detection service—to flag Catwatchful if it’s found on a user’s device. The app’s hosting provider suspended the account associated with the exposed API, but the developer quickly migrated to a new hosting provider and continued operations.
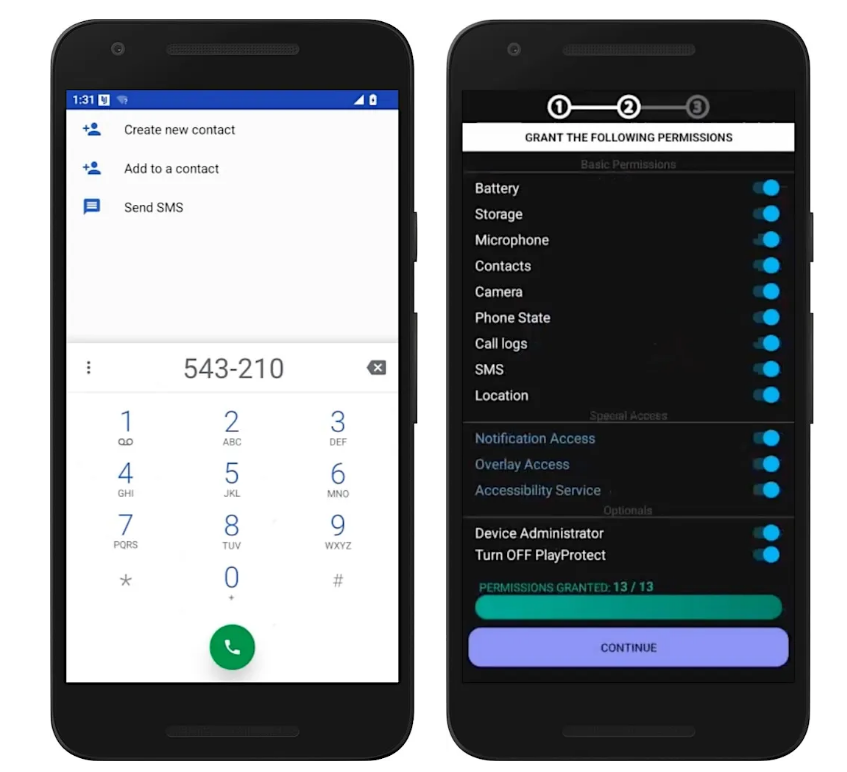
Despite the app’s marketing claims of being undetectable, Android users can manually check for its presence. Dialing #543210# and hitting the call button triggers a hidden command that forces the app to reveal itself—an undocumented “backdoor” likely built for removal purposes.
Final Thoughts
This case highlights the paradox of spyware apps like Catwatchful: while designed to violate others’ privacy, they often fail to secure their own systems. Worse, by exposing user credentials and surveillance data, they put both the watcher and the watched at risk.
As regulators and security platforms increase scrutiny on stalkerware, incidents like this underscore the need for stronger enforcement and user awareness. If an app claims to offer invisible control over another person’s device, chances are it’s not just unethical—it’s dangerously insecure.