SAP NetWeaver Vulnerability Exploited to Deploy Linux Malware Auto-Color

Darktrace researchers have uncovered a targeted cyberattack in which threat actors exploited a critical SAP NetWeaver vulnerability (CVE-2025-31324) to deploy the Linux malware Auto-Color into the network of an unnamed U.S.-based chemical company.
The breach was detected in April 2025. Subsequent analysis revealed that Auto-Color has undergone significant evolution in recent months, adopting sophisticated evasion techniques designed to bypass conventional detection systems.
Auto-Color was first identified by Palo Alto Networks in early 2025. At the time, analysts noted the malware’s extensive stealth capabilities, including:
- Use of inconspicuous filenames such as
doorandegg - Concealment of command-and-control (C2) communications
- Custom encryption algorithms to obfuscate its configuration and communication data
The malware also leverages ld.so.preload—a Unix mechanism for preloading shared libraries—to inject itself into processes for stealthy persistence. Notably, Auto-Color adapts its behavior based on user privileges, making it more difficult to detect under limited-access accounts.
Its capabilities include:
- Initiating reverse shells
- Harvesting system information
- Creating and modifying files
- Executing arbitrary programs
- Proxying network traffic
- Activating a self-destruct “kill switch” to erase all traces of its presence
Darktrace emphasized the challenge of analyzing the malware due to its conditional behavior:
"If the command-and-control (C2) server is unavailable, Auto-Color effectively halts and does not engage its full malicious functionality, appearing harmless to analysts," the company stated. "This behavior complicates analysis and makes it difficult to determine which payloads, credential theft mechanisms, or persistence methods are being used."
While the initial attack vector remained unknown during Palo Alto’s initial investigation—then focused on universities and government agencies across North America and Asia—Darktrace has now confirmed that attackers exploited CVE-2025-31324 in SAP NetWeaver to gain access.
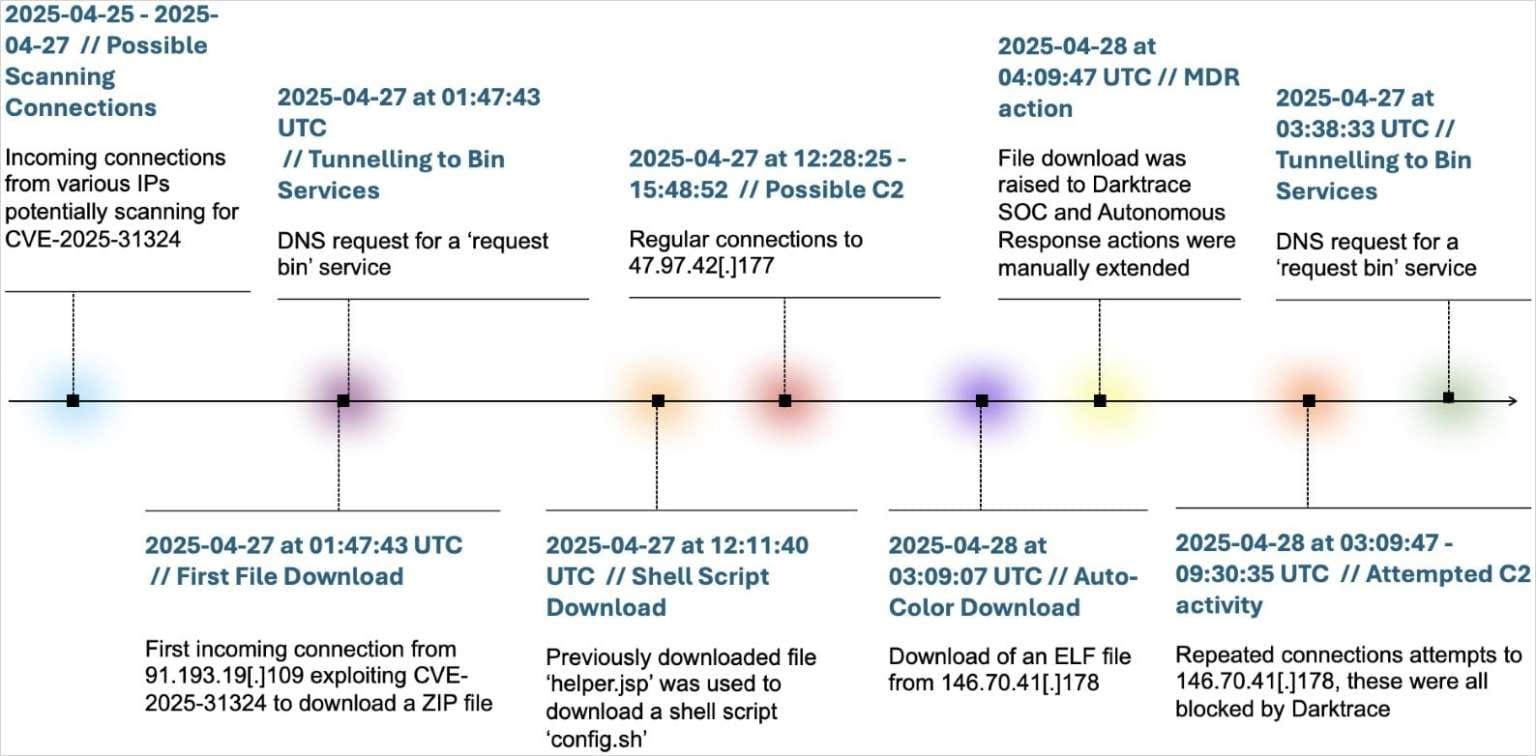
This critical vulnerability allows unauthenticated remote code execution (RCE) via malicious binary uploads to vulnerable NetWeaver instances. SAP released a patch in April 2025, but even then, cybersecurity professionals warned that exploitation had likely already begun.
By May 2025, reports indicated that ransomware operators and suspected Chinese state-sponsored groups had also begun leveraging the flaw. Mandiant later confirmed evidence of zero-day exploitation stretching back to mid-March 2025.