PyPI Combats Attacks Based on Domain Reclaiming

The developers of the Python Package Index (PyPI) have announced new measures to combat domain reclaiming attacks—an overlooked threat that allows malicious actors to hijack user accounts through password resets.
As the official repository for Python packages, PyPI is a critical resource for software developers, project maintainers, and companies relying on Python libraries, tools, and frameworks.
How Domain Reclaiming Works
PyPI accounts are linked to email addresses. If the domain hosting such an email account expires, attackers can register it, set up a mail server, and issue a password reset request. This effectively grants them control of the maintainer’s account and, by extension, the associated Python project.
The danger lies in the supply chain. A compromised project can distribute malicious versions of popular packages, which may then be automatically installed via pip in countless environments.
Past Example: ctx and phppass
In 2022, the ctx and phppass packages were compromised in a similar way. A security researcher intentionally modified them to steal environment variables, including credentials and AWS keys.
The stunt drew heavy criticism. In most bug bounty scenarios, researchers demonstrate exploits with minimal disruption—for example, printing a harmless message like “you’ve been hacked!” or collecting non-sensitive details such as IP addresses and hostnames. But stealing cloud credentials crossed an ethical line, as it risked serious security consequences.
PyPI’s New Safeguards
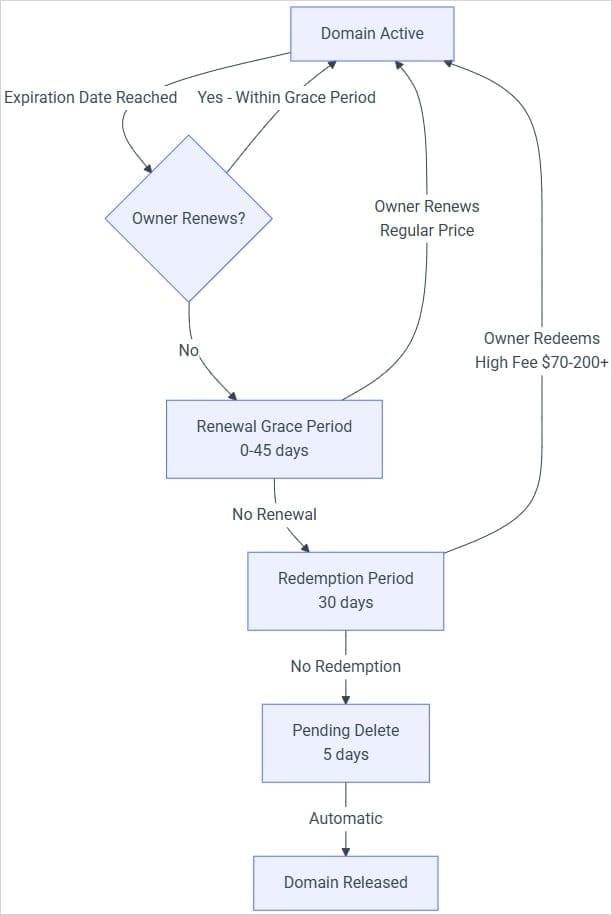
To close this gap, PyPI will now verify whether the domains tied to registered email addresses remain active. Expired domains will automatically cause the associated email addresses to be marked as unverified.
For these checks, PyPI relies on the Domainr Status API, which identifies whether a domain is active, in a grace period, redemption period, or pending deletion.
Once an email address is marked unverified, it can no longer be used for password resets or account recovery. This means that even if an attacker successfully registers an expired domain, they cannot use it to hijack a maintainer’s account.
Why It Matters
By tightening control over email domain validity, PyPI is reducing the risk of supply chain compromise—an attack path that can ripple far beyond a single project. This step not only strengthens PyPI’s ecosystem but also protects the millions of developers and organizations that depend on Python packages every day.




