Phishers Use the Symbol «ん» to Deceive Users

Cybercriminals are exploiting the Unicode character «ん» from the Japanese hiragana script to disguise phishing links as legitimate. In certain systems and fonts, this character can resemble a forward slash, tricking users into believing a malicious URL is authentic.
Homoglyph Tricks in Action
This technique is part of a broader category of homographic attacks, where scammers exploit homoglyphs—characters that look nearly identical but carry different meanings. Classic examples include:
- The Latin uppercase "I" vs. lowercase "l".
- The Cyrillic "О" (U+041E) vs. the Latin "O" (U+004F).
In this case, attackers are leveraging the hiragana symbol «ん» (U+3093). Depending on font rendering, it can resemble "/n" or "/~", making URLs appear more convincing.
Booking.com Phishing Campaign
The campaign was first identified by cybersecurity researcher JAMESWT, who shared findings on X. Attackers impersonated Booking.com emails, embedding links that appeared legitimate but redirected users elsewhere.
- Displayed URL:
https://admin.booking.com/hotel/hoteladmin/... - Actual destination:
https://account.booking.comんdetailんrestric-access.www-account-booking[.]com/en/
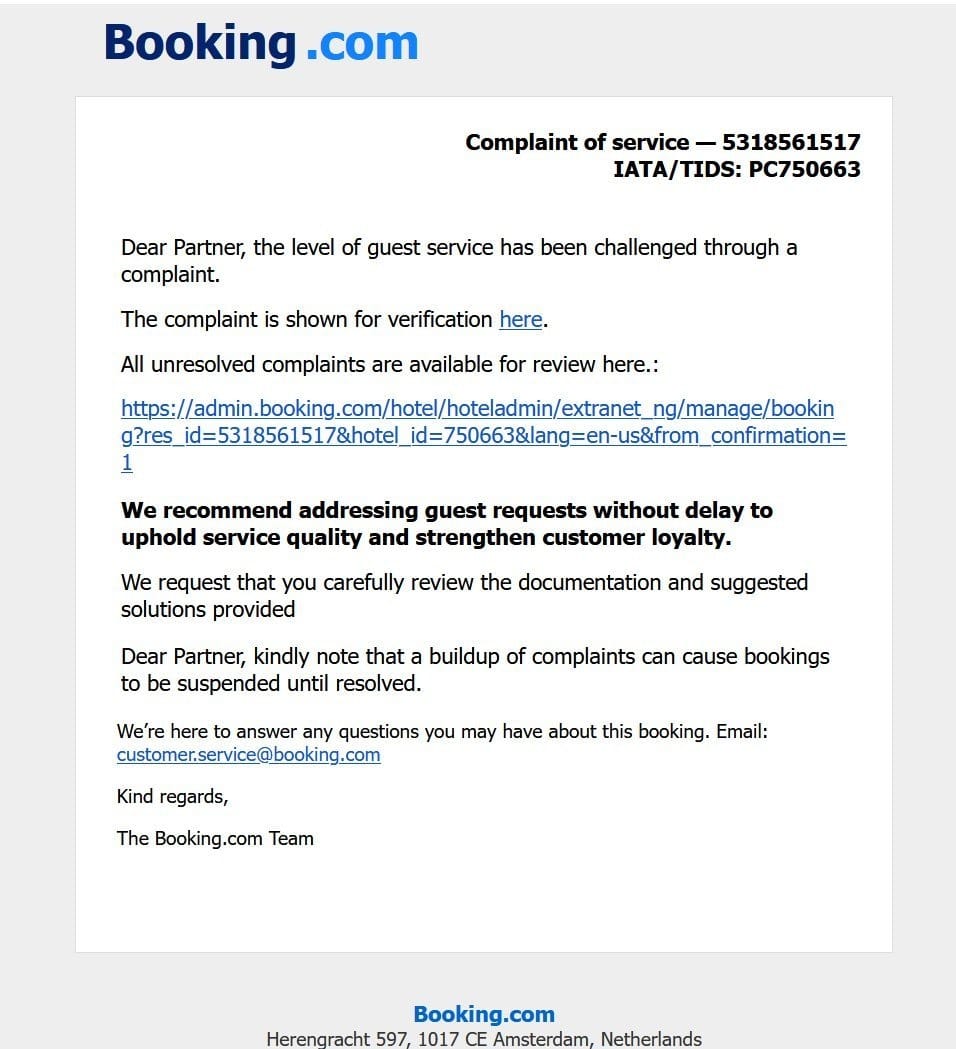
At a glance, the extra «ん» characters created the illusion of subdirectories, but in reality the malicious domain was www-account-booking[.]com.
Victims who clicked were redirected to www-account-booking[.]com/c.php?a=0, which delivered a malicious MSI installer from a CDN link (https://updatessoftware.b-cdn[.]net/john/pr/04.08/IYTDTGTF[.]msi).
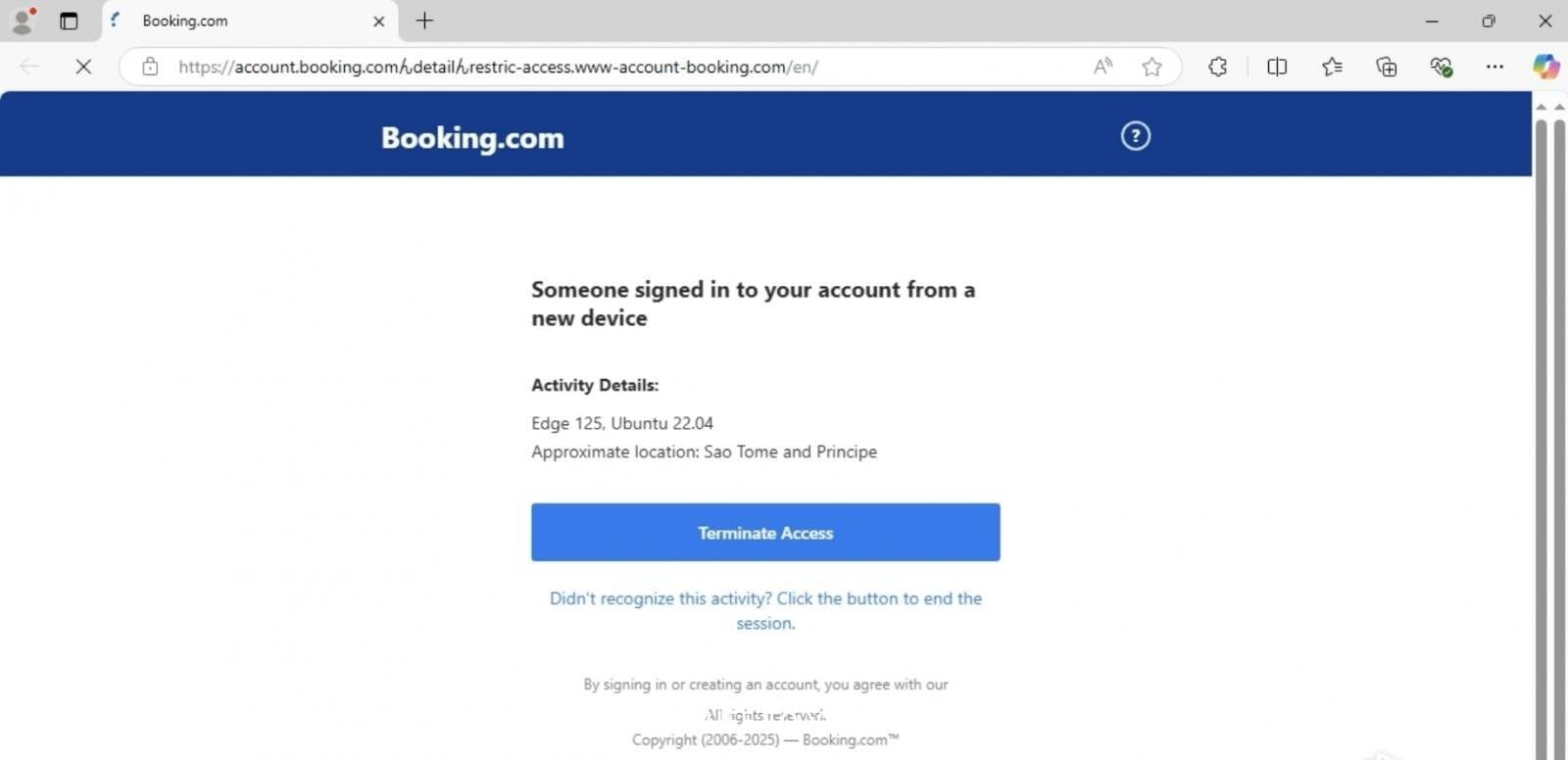
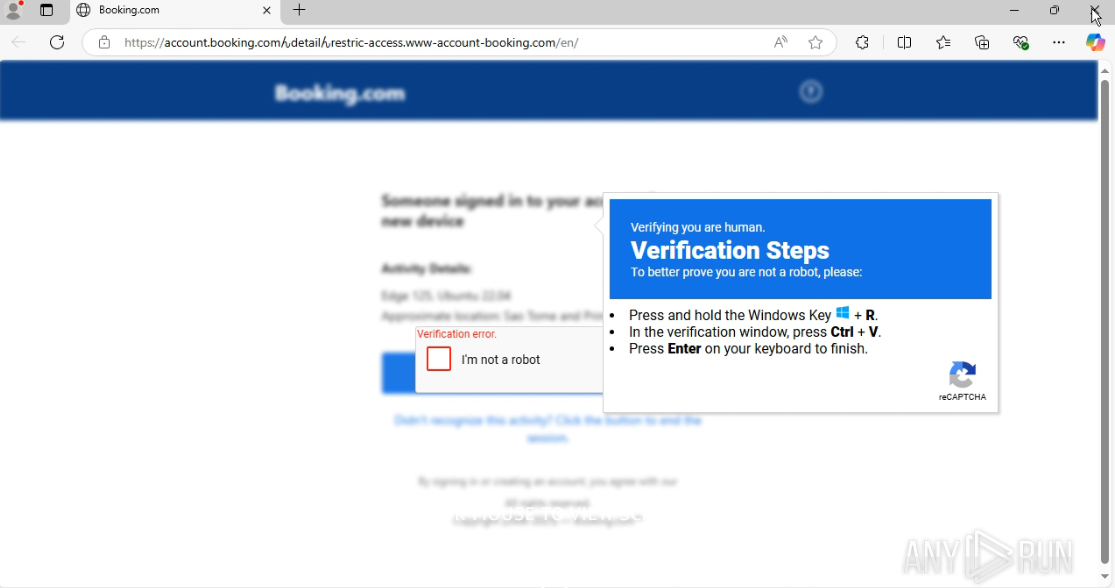
According to Bleeping Computer, the installer deployed additional payloads, including infostealers and remote access trojans (RATs), often detected in sandbox environments such as any.run. The method combines social engineering with a ClickFix-style attack, further pressuring victims to proceed.
Other Cases: Intuit Spoofing
Journalists also report a parallel campaign targeting Intuit users. Here, attackers registered domains starting with “Lntuit”—a subtle swap that, in certain fonts, closely resembles "intuit." Emails using these fake domains mimicked official Intuit messages, aiming to harvest login credentials.
How to Stay Safe
Researchers stress the importance of:
- Hovering over links before clicking, to preview the true destination.
- Double-checking domain names in the browser’s address bar, not just the displayed text.
- Remaining aware that Unicode characters can create deceptive visual similarities, fooling even cautious users.
Homoglyph-based phishing is not new, but the use of characters like «ん» highlights how attackers continually adapt, finding fresh ways to exploit the smallest visual details.




