Over 29,000 Exchange Servers Still Vulnerable to Critical Flaw

More than 29,000 Microsoft Exchange servers remain unpatched against CVE-2025-53786, a severe security flaw that could allow attackers to move laterally into Microsoft cloud environments and potentially achieve full domain compromise.
How the Vulnerability Works
The flaw allows attackers with administrative access to on-premises Exchange servers to escalate privileges in connected cloud environments by forging or manipulating trusted tokens and API requests. The attack leaves minimal forensic traces, making detection extremely difficult.
Affected Systems
The vulnerability impacts hybrid configurations of:
- Exchange Server 2016
- Exchange Server 2019
- Microsoft Exchange Server Subscription Edition
Root Cause
The issue stems from architectural changes introduced in April 2025 under Microsoft’s Secure Future Initiative. This shift replaced the older shared identity model between on-premises Exchange and Exchange Online with a dedicated hybrid application.
However, researchers later discovered the new design could still be abused for post-exploitation privilege escalation. At Black Hat, experts from Outsider Security demonstrated how the flaw could be weaponized.
“Initially, I didn’t consider this a vulnerability because the protocol was designed with these features in mind—it simply lacked critical security controls,” said Dirk-Jan Mollema of Outsider Security.
Exploitation Risk
Although Microsoft has not observed active exploitation, the flaw is tagged as “Exploitation More Likely”, meaning public proof-of-concept code is expected soon.
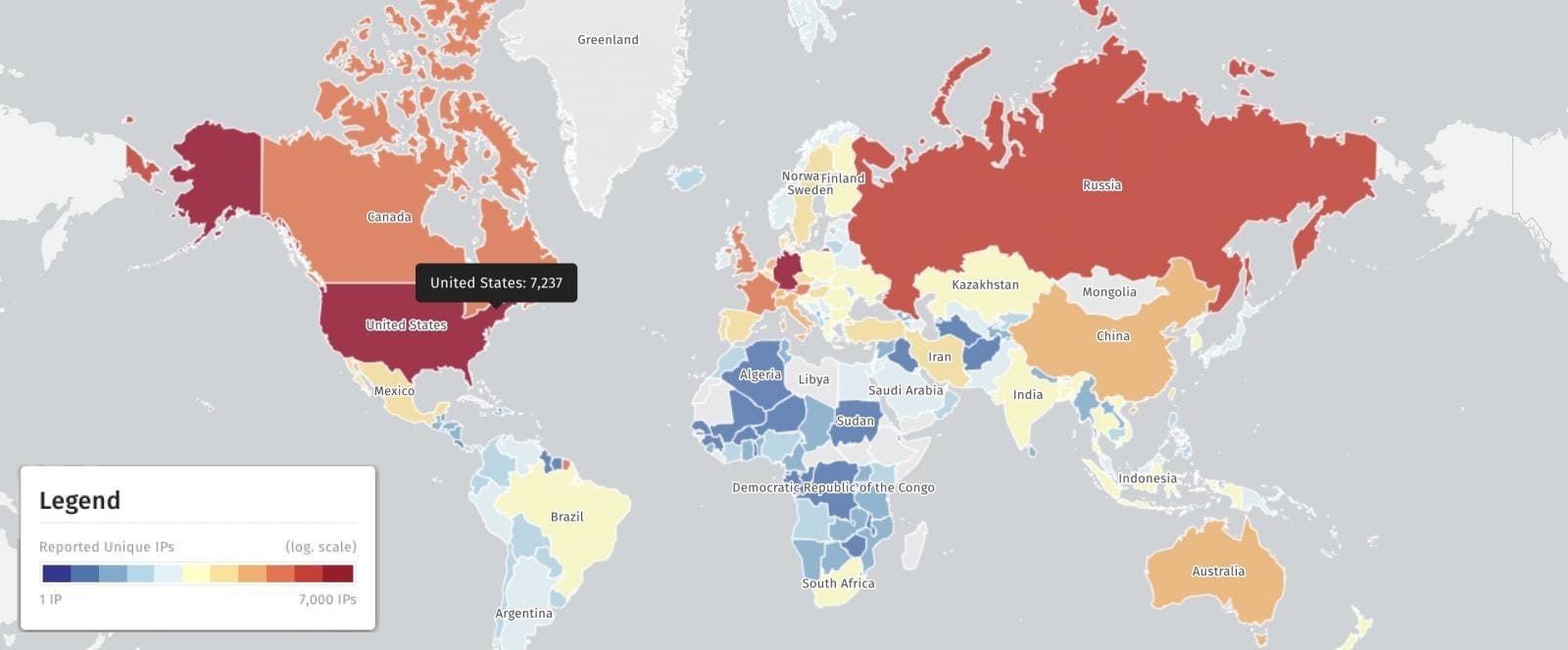
According to Shadowserver, 29,098 unpatched Exchange servers remain exposed online, including:
- 7,200+ in the United States
- 6,700+ in Germany
- 2,500+ in Russia
Urgent Mitigation Required
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an emergency directive, requiring all federal agencies—including the Departments of Treasury and Energy—to patch immediately.
CISA warns that failing to address CVE-2025-53786 could result in “full compromise of hybrid cloud and on-premises domains.”
How to Protect Your Systems
Organizations that applied Microsoft’s April 2025 hotfix and followed its configuration guidance should already be protected. Those that have not must:
- Apply the latest hotfix
- Manually deploy a dedicated Exchange hybrid application (per Microsoft’s instructions)
“Patching alone isn’t enough—admins must manually migrate to a dedicated service principal,” Mollema stressed. “The urgency depends on how critical it is to isolate on-premises Exchange resources from cloud resources. The old hybrid configuration granted full access to Exchange Online and SharePoint.”
Key Takeaway
This is a post-compromise vulnerability—attackers must first gain admin access to on-premises Exchange before exploiting it. Patching and proper configuration are essential to prevent escalation into cloud environments.