Over 200,000 WordPress Sites Vulnerable Due to Post SMTP Plugin Flaw

More than 200,000 WordPress websites are running a vulnerable version of the Post SMTP plugin, exposing them to the risk of administrator account takeovers.
Post SMTP is a widely used email delivery plugin, with over 400,000 active installations. Promoted as a more reliable alternative to WordPress’s default wp_mail() function, it enhances email delivery and logging capabilities for website administrators.
High-Severity Flaw Discovered
In May 2025, an anonymous security researcher reported the vulnerability to PatchStack, a WordPress security firm. The flaw has been assigned CVE-2025-24000, with a CVSS score of 8.8, indicating high severity.
Vulnerability Details
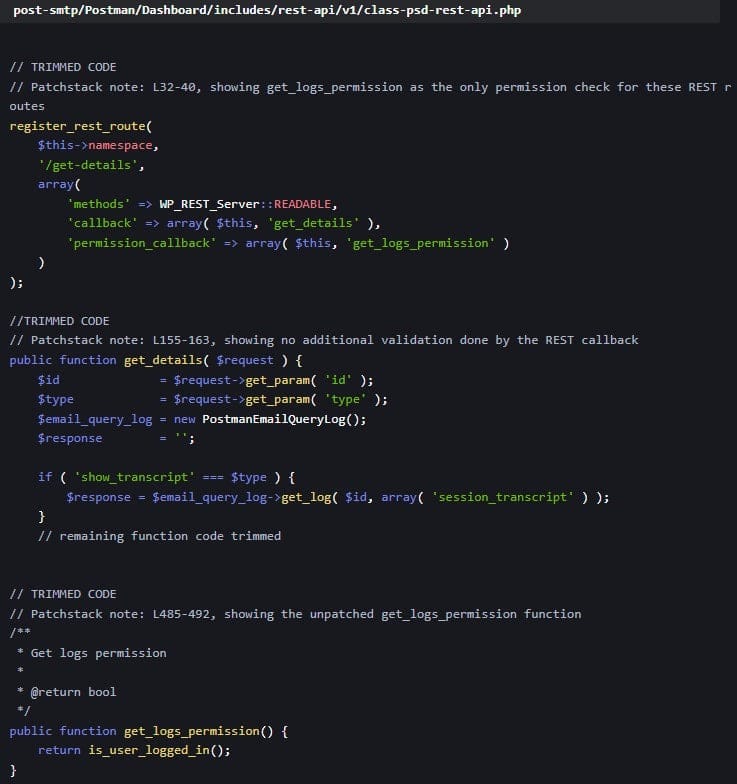
The issue affects all versions of Post SMTP up to 3.2.0 and is rooted in improper access control within the plugin’s REST API endpoints. The plugin verified only whether a user was logged in—without checking their permission level—before granting access to sensitive functions.
This oversight allowed low-privileged users (e.g., Subscribers) to:
- Access email logs, which may contain full message content, including passwords and private correspondence
- Trigger password resets for admin accounts, intercept the reset link via logs, and seize control of the site
Patch Released—but Adoption Is Lagging
The plugin developer was notified on May 26, 2025, and submitted a patch shortly after. The fix—released in Post SMTP version 3.3.0 on June 11, 2025—added proper privilege checks to the get_logs_permission function.
However, WordPress.org telemetry shows that only 48.5% of users have updated to the patched version. This leaves over 200,000 sites exposed to potential exploitation.
Even more concerning: 24.2% of users are still running older 2.x versions, which are vulnerable to additional, unpatched flaws.
Key Takeaways
- Critical Risk: Exploiting this flaw lets attackers escalate from Subscriber to full admin
- Patch Available: Update to Post SMTP 3.3.0 or later immediately
- Widespread Exposure: More than half of installations remain unpatched
Website administrators are strongly urged to update Post SMTP or disable the plugin entirely if it is no longer in use. Leaving outdated versions active leaves websites—and user data—dangerously exposed.