NX Falls Victim to Supply Chain Attack: Hackers Steal Thousands of Secrets

The maintainers of NX have disclosed a major supply chain attack, dubbed s1ngularity, which occurred on August 26, 2025. The compromise of a developer’s token allowed attackers to publish malicious versions of the popular npm package and related tools, enabling them to steal user data on a large scale.
NX and Its Impact
NX is a widely used open-source build platform designed to manage code in large projects. Marketed as an “AI-first build platform that brings together everything from your editor to your CI,” the project sees more than 4 million weekly downloads.
In an official announcement, the maintainers confirmed:
“Malicious versions of the nx package, as well as some auxiliary plugins, were published to npm. They contained code that scans the file system, collects credentials, and sends them to GitHub in the form of a repository from the user’s account.”
Root Cause of the Breach
The developers traced the compromise to a vulnerable GitHub Actions workflow added on August 21, 2025. The flaw allowed executable code injection through a specially crafted pull request header. Although the workflow was rolled back shortly after discovery, the attacker exploited an outdated branch that still contained the vulnerable configuration.
The pull_request_target trigger, unlike the standard pull_request, executed with elevated privileges—including a GITHUB_TOKEN with read/write permissions. This token was then used to run publish.yml, which publishes NX packages to npm.
As a result, attackers stole the npm token by redirecting it to a webhook[.]site endpoint they controlled.
“As part of a bash injection, the pull request validation workflow ran publish.yml with this malicious commit and sent our npm token to an unfamiliar webhook,” the NX team explained.
Affected Packages
The following malicious versions were published (now removed from npm):
- nx 21.5.0, 20.9.0, 20.10.0, 21.6.0, 20.11.0, 21.7.0, 21.8.0, 20.12.0
- @nx/devkit 21.5.0, 20.9.0
- @nx/enterprise-cloud 3.2.0
- @nx/eslint 21.5.0
- @nx/js 21.5.0, 20.9.0
- @nx/key 3.2.0
- @nx/node 21.5.0, 20.9.0
- @nx/workspace 21.5.0, 20.9.0
The malicious versions contained a postinstall script that activated after installation, scanning the system for text files, collecting credentials, and uploading the information (encoded in Base64) to public GitHub repositories named s1ngularity-repository.
The script also modified .zshrc and .bashrc files, adding the command sudo shutdown -h 0, which prompted users for their password and immediately powered down their machines.
User Guidance
Although GitHub has begun removing the compromised repositories, NX maintainers advise all affected users to:
- Assume credentials are compromised.
- Change passwords immediately.
- Rotate GitHub and npm tokens.
- Remove malicious packages.
- Inspect .zshrc and .bashrc files for unauthorized commands.
The NX team says it has since rotated tokens, audited GitHub and npm activity, and updated publishing rights to require two-factor authentication.
Wider Findings
Cybersecurity company Wiz reported that 90% of the stolen GitHub tokens remain valid, along with dozens of cloud credentials and npm tokens. Many infections reportedly originated from the NX extension for Visual Studio Code.
Meanwhile, researchers at StepSecurity highlighted that this incident marks the first known case of attackers exploiting AI command-line tools—including Claude, Google Gemini, and Amazon Q—to bypass security controls.
“They forced the AI tools to recursively scan the file system and record discovered sensitive file paths in /tmp/inventory.txt, effectively using legitimate tools as accomplices in the attack,” StepSecurity explained.Repositories containing stolen data remained publicly accessible for about eight hours before GitHub intervened.
GitGuardian later identified 1,346 repositories containing the string s1ngularity-repository. New repositories continue to appear, suggesting that developers are still using infected packages. Attackers are also using stolen tokens to make private repositories public and rename them according to the pattern s1ngularity-repository-#5characters#.
Scale of the Breach
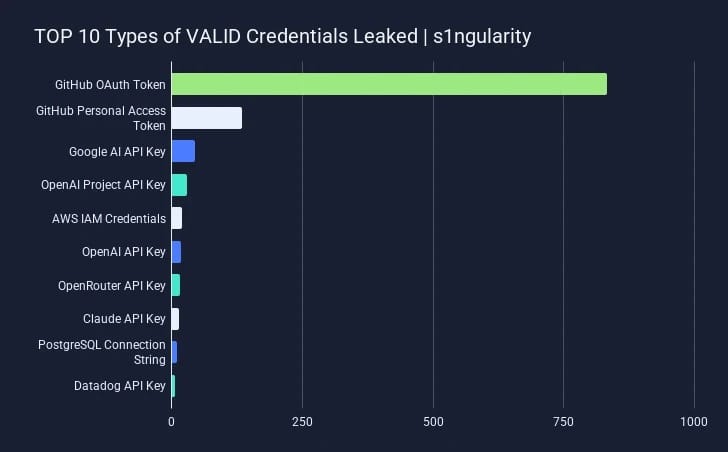
Researchers estimate that at least 2,349 secrets were stolen, most of them GitHub OAuth keys and Personal Access Tokens (PATs). Other compromised credentials include API keys and secrets for Google AI, OpenAI, AWS, OpenRouter, Anthropic Claude, PostgreSQL, and Datadog.
It was also noted that 85% of infected systems were running macOS.