Millions of Cars Exposed to Bluetooth Attacks via PerfektBlue Vulnerabilities
Critical flaws in OpenSynergy’s BlueSDK put Mercedes-Benz, Volkswagen, Skoda, and others at risk.
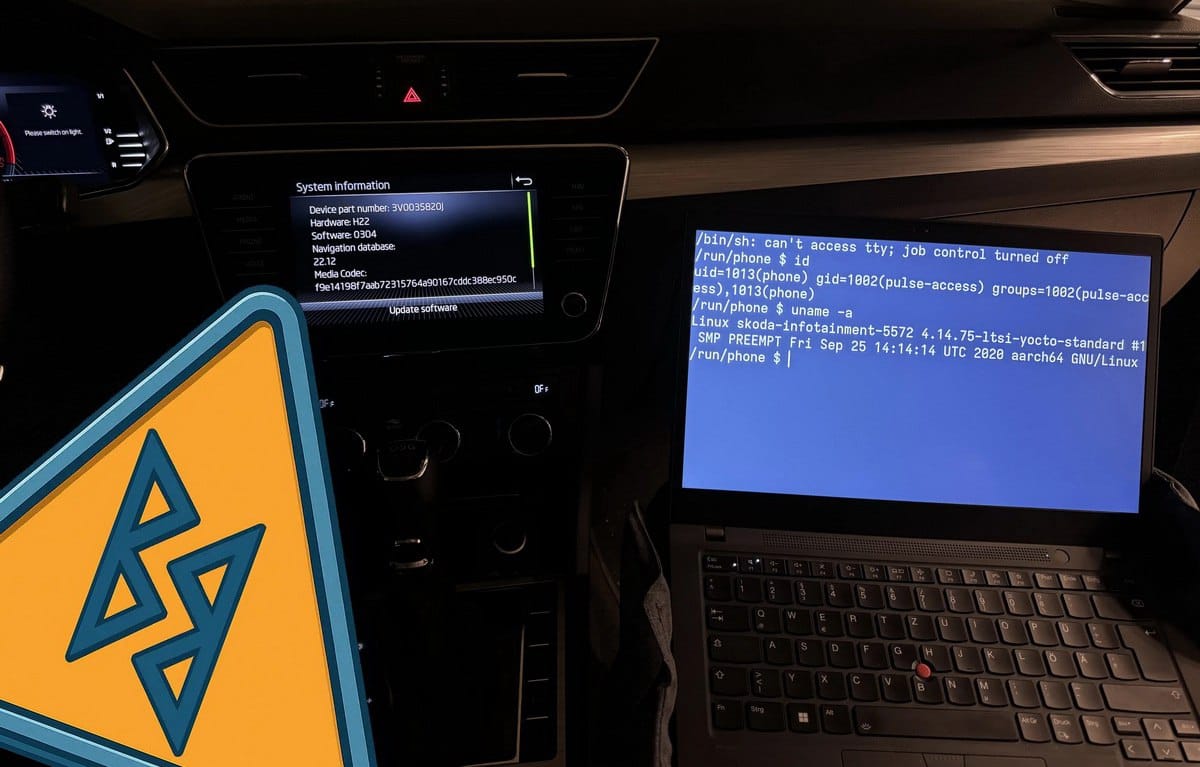
Four newly disclosed vulnerabilities in the BlueSDK Bluetooth stack—developed by OpenSynergy—have exposed millions of vehicles to potential remote attacks. Collectively named PerfektBlue, these flaws enable remote code execution (RCE) and could grant attackers access to sensitive vehicle systems, including infotainment units and potentially more critical components.
The flaws affect vehicles from major automakers such as Mercedes-Benz, Volkswagen, and Skoda. Although OpenSynergy confirmed the vulnerabilities in June 2024 and issued patches in September, most manufacturers have yet to integrate the fixes into their firmware. Alarmingly, at least one major OEM reportedly only became aware of the issue recently.
Who Discovered PerfektBlue?
The vulnerabilities were discovered by PCA Cyber Security, a research team specializing in automotive cybersecurity and frequent participants in Pwn2Own Automotive. The team has identified over 50 security issues in vehicle systems since last year.
The Scope of the Threat
PerfektBlue impacts a wide range of embedded devices across the automotive sector and potentially beyond. Researchers reverse-engineered the compiled BlueSDK binary—as source code was unavailable—and found that attackers could:
- Execute arbitrary code via a malicious Bluetooth connection
- Escalate privileges and move laterally across in-vehicle networks
- Access infotainment features, including GPS data, microphone feeds, phone contacts, and more
Vulnerabilities at a Glance
The flaws have been assigned the following CVEs:
- CVE-2024-45434 — Use-after-free in the AVRCP (Audio/Video Remote Control Profile) media control service
- CVE-2024-45431 — Improper Channel ID (CID) validation in L2CAP (Logical Link Control and Adaptation Protocol)
- CVE-2024-45433 — Incomplete function termination in RFCOMM (Radio Frequency Communication)
- CVE-2024-45432 — Incorrect parameter handling in RFCOMM function calls
How the Attack Works
PerfektBlue enables a "one-click" remote code execution attack. In many cases, attackers only need to trick a user into pairing with a malicious Bluetooth device. Some vehicle infotainment systems don’t even require user confirmation to establish a Bluetooth connection—greatly reducing the barrier to exploitation.
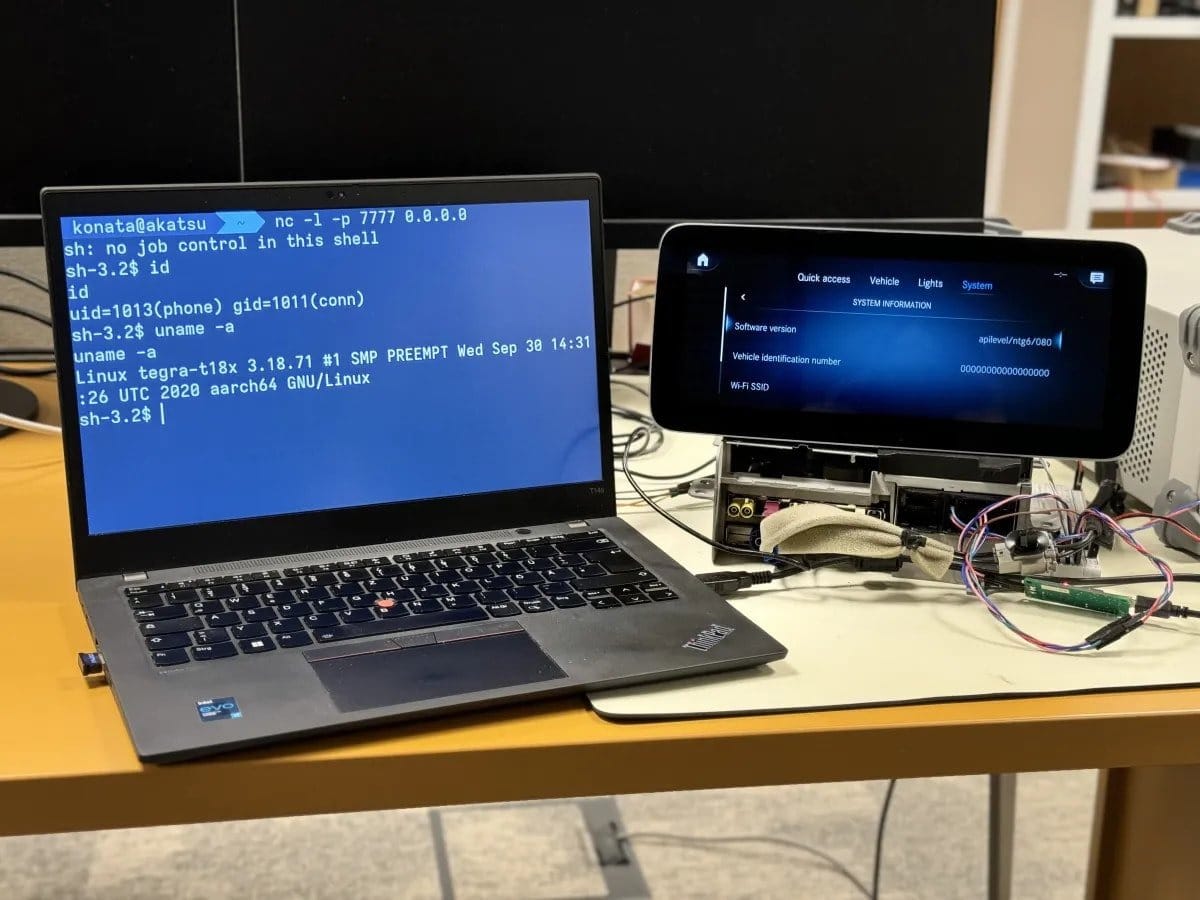
Confirmed Affected Vehicles
Researchers confirmed successful exploitation on the following systems:
- Volkswagen ID.4 — ICAS3 infotainment system
- Mercedes-Benz — NTG6 system
- Skoda Superb — MIB3 infotainment system
Once connected, attackers were able to:
✔ Establish a reverse shell over TCP/IP (used for inter-component communication)
✔ Eavesdrop on in-cabin conversations
✔ Track GPS location
✔ Access personal data, including synced phone contacts
✔ Attempt lateral movement toward other subsystems
Automakers' Response
Volkswagen acknowledged the flaws but downplayed their severity, stating that successful exploitation would require:
- The attacker to be within 5–7 meters of the vehicle
- The ignition to be on
- The infotainment system to be in pairing mode
- The user to manually approve the Bluetooth connection
The company emphasized that critical driving systems (e.g., steering, brakes, engine) remain isolated from infotainment components.
Mercedes-Benz did not respond to multiple requests for comment. Another major OEM was recently confirmed to be vulnerable but has not yet been formally notified.
OpenSynergy’s Role and Industry Impact
As the developer of BlueSDK, OpenSynergy plays a central role in the Bluetooth stack ecosystem across automotive and other industries. However, due to extensive rebranding and customization of BlueSDK by OEMs, identifying all affected products remains challenging.
What Happens Next
A full technical breakdown of the PerfektBlue vulnerabilities is scheduled for release in November 2025. In the meantime, researchers and cybersecurity experts are urging automakers to urgently apply the available patches.
Recommendations for Drivers
To minimize the risk of exploitation:
- Avoid pairing with unknown Bluetooth devices
- Disable Bluetooth when not in use
- Check for firmware updates from your vehicle manufacturer regularly
As vehicles become increasingly connected, Bluetooth vulnerabilities like PerfektBlue highlight the critical need for prompt patching, secure architecture, and proactive security research




