Microsoft Discloses ‘Sploitlight’ Vulnerability Affecting macOS

Microsoft Discloses ‘Sploitlight’ Vulnerability Affecting macOS
Microsoft has disclosed details of a now-patched vulnerability in macOS that could have allowed attackers to bypass Apple’s Transparency, Consent, and Control (TCC) protections and steal sensitive user data—including cached Apple Intelligence content.
TCC is the security framework in macOS responsible for controlling app permissions. It governs what applications can access and how they interact with sensitive data such as contacts, photos, camera input, and location services. When a new app requests access to private user information, TCC ensures that permission prompts appear and unauthorized access is blocked.
The vulnerability, tracked as CVE-2025-31199, was discovered by Microsoft’s threat research team and addressed by Apple in the March 2025 macOS Sequoia 15.4 update.
Exploiting Spotlight Plugins
Microsoft researchers found that despite TCC’s safeguards, attackers could abuse the privileged status of Spotlight plugins—components designed to index local content for faster search—to gain indirect access to protected data. These plugins inherit elevated permissions, and when exploited, could be used to execute malicious code or retrieve sensitive files.
Microsoft dubbed the vulnerability “Sploitlight” and published technical details in a new report. The flaw could have been used to harvest a wide range of personal and system data, including elements stored by Apple Intelligence—Apple’s on-device AI layer that processes user activity, preferences, and cross-device context.
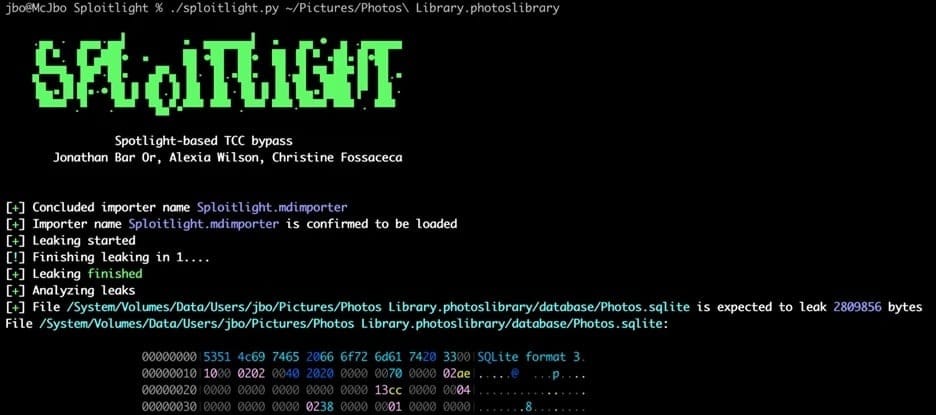
Data potentially exposed includes:
- Photo and video metadata
- GPS and geolocation information
- Face and people recognition data
- Activity and usage logs
- Photo albums and shared libraries
- Search history and Spotlight queries
- Deleted photo and video thumbnails
In Microsoft’s words:
“While this issue resembles previous TCC bypasses—such as HM-Surf and powerdir—the consequences of Sploitlight are more severe. It enables the extraction of sensitive information cached by Apple Intelligence, including precise geolocation, facial recognition data, and user activity logs.”
iCloud Account Risk Amplifies Impact
One particularly concerning aspect of the attack is its ability to leverage iCloud-linked data. Since Apple Intelligence caches context from all devices associated with a user’s iCloud account, attackers exploiting Sploitlight could extract information not only from the local device, but from other linked devices—remotely.
This elevates the threat from a local compromise to a broader cross-device privacy breach, with implications for both personal and enterprise users operating within the Apple ecosystem.
Microsoft’s Disclosure and Apple’s Patch
The flaw was responsibly disclosed to Apple, and a fix was issued in macOS Sequoia 15.4. Microsoft’s report encourages users and IT administrators to apply system updates promptly, particularly in regulated industries where data confidentiality is paramount.
Though no evidence of active exploitation was mentioned in Microsoft’s disclosure, the vulnerability highlights an enduring truth in cybersecurity: even mature permission frameworks can be undermined by overlooked privileged components.