McDonald’s Recruiting AI Bot Exposed Millions of Applicants’ Data Due to Password “123456”

Renowned cybersecurity experts Sam Curry and Ian Carroll have uncovered a massive data exposure involving Olivia, the AI-powered chatbot McDonald’s uses to screen job applicants. The researchers found that a database tied to the bot contained over 64 million records, all exposed due to the use of the password “123456.”
The discovery began when Curry and Carroll noticed complaints on Reddit about Olivia’s “inappropriate” and often nonsensical responses. Olivia, built by Paradox.ai—a company specializing in AI-driven recruiting tools—is used to guide applicants through job assessments, collect resumes, and gather contact information. However, its poor comprehension and awkward interactions have earned it a notorious reputation on social media.
“I thought it was pretty unique and dystopian compared to a normal hiring process. That’s why I wanted to dig deeper,” said Carroll. “I started applying for a job, and within 30 minutes, we had full access to nearly every application ever submitted to McDonald’s over many years.”
Curry and Carroll initially tested Olivia for prompt injection vulnerabilities, but found nothing of concern. Shifting tactics, they attempted to register as a McDonald’s franchisee to gain backend access. Instead, they discovered an overlooked login portal for Paradox.ai employees on McHire.com.
Carroll tried two common credential combinations—“admin/admin” and then “123456/123456.” Incredibly, the second attempt granted full administrative access.
“This is more common than you’d think,” Carroll said. “Even worse, the login page lacked multi-factor authentication.”
Once inside, the researchers accessed a test McDonald’s restaurant account and noticed that all listed employees were developers from Paradox.ai based in Vietnam. They also came across fake job postings tied to this non-existent location. After applying to one of the dummy listings, they were able to view their own application inside the backend system.
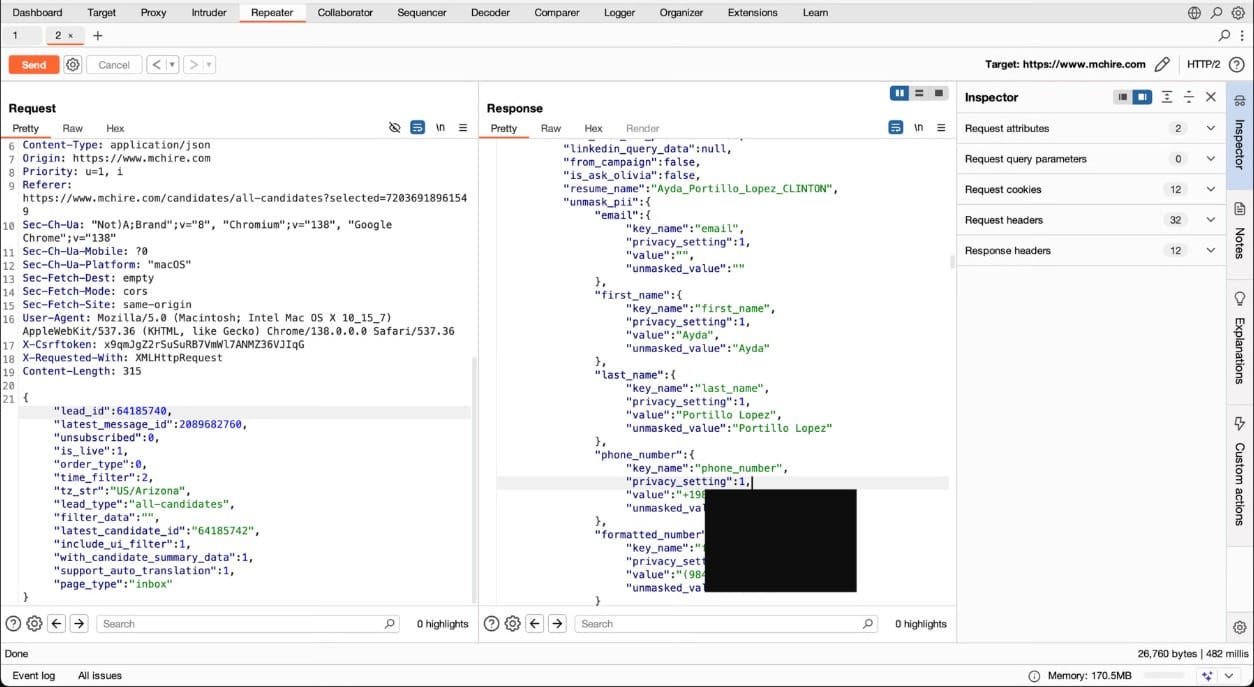
The deeper issue surfaced when they examined the application ID system. Each application was tied to a unique numeric ID—over 64 million in total. By simply decrementing the ID value, the researchers could access other applicants’ data, including names, email addresses, and phone numbers.
While they refrained from mass scraping to avoid violating privacy laws or ethical boundaries, they confirmed the vulnerability by viewing a few legitimate records.
Though the leaked data wasn’t deeply sensitive (e.g., no Social Security numbers or bank info), Curry stressed the high phishing risk:
“This isn’t just personal data—it’s information about people actively seeking jobs at McDonald’s. If someone wanted to run a payroll scam or fake offer campaign, this would be perfect.”
In response, Paradox.ai stated that the account accessed by the researchers—using the “123456” password—had been inactive since 2019 and should have been deactivated. The company emphasized that only seven records were accessed, five of which contained real applicant information.
Paradox also announced plans to launch a bug bounty program to improve security and detect vulnerabilities more proactively.
McDonald’s, for its part, was quick to distance itself from the breach, telling Wired:
“We are disappointed by this unacceptable vulnerability in a third-party provider’s system. Upon learning of the issue, we demanded Paradox.ai resolve it immediately, and it was fixed the same day. We take cybersecurity seriously and will continue holding third-party vendors to our data protection standards.”




