Malware ‘XORIndex’ Found in 67 Malicious npm Packages Linked to North Korean Hackers

North Korean hackers have uploaded 67 malicious packages to the npm registry, spreading a new malware loader dubbed XORIndex. According to cybersecurity firm Socket, these packages were downloaded over 17,000 times before being discovered and taken down.
The operation is part of an ongoing campaign known as Contagious Interview, which specifically targets software developers through fake job offers and trojanized developer tools.
Campaign Expands with New Loader
Socket reports that this is a continuation of a broader malware distribution effort that began in April 2025. In the previous wave, the same threat actors planted 35 malicious npm packages containing infostealers and backdoors.
The Contagious Interview campaign itself has been active since at least December 2022, with a consistent focus on luring developers through social engineering. Victims are often tricked into installing malicious software after being approached with fake employment opportunities.
Once compromised, developers’ systems are infected with a range of malware designed to exfiltrate sensitive corporate data or steal cryptocurrency.
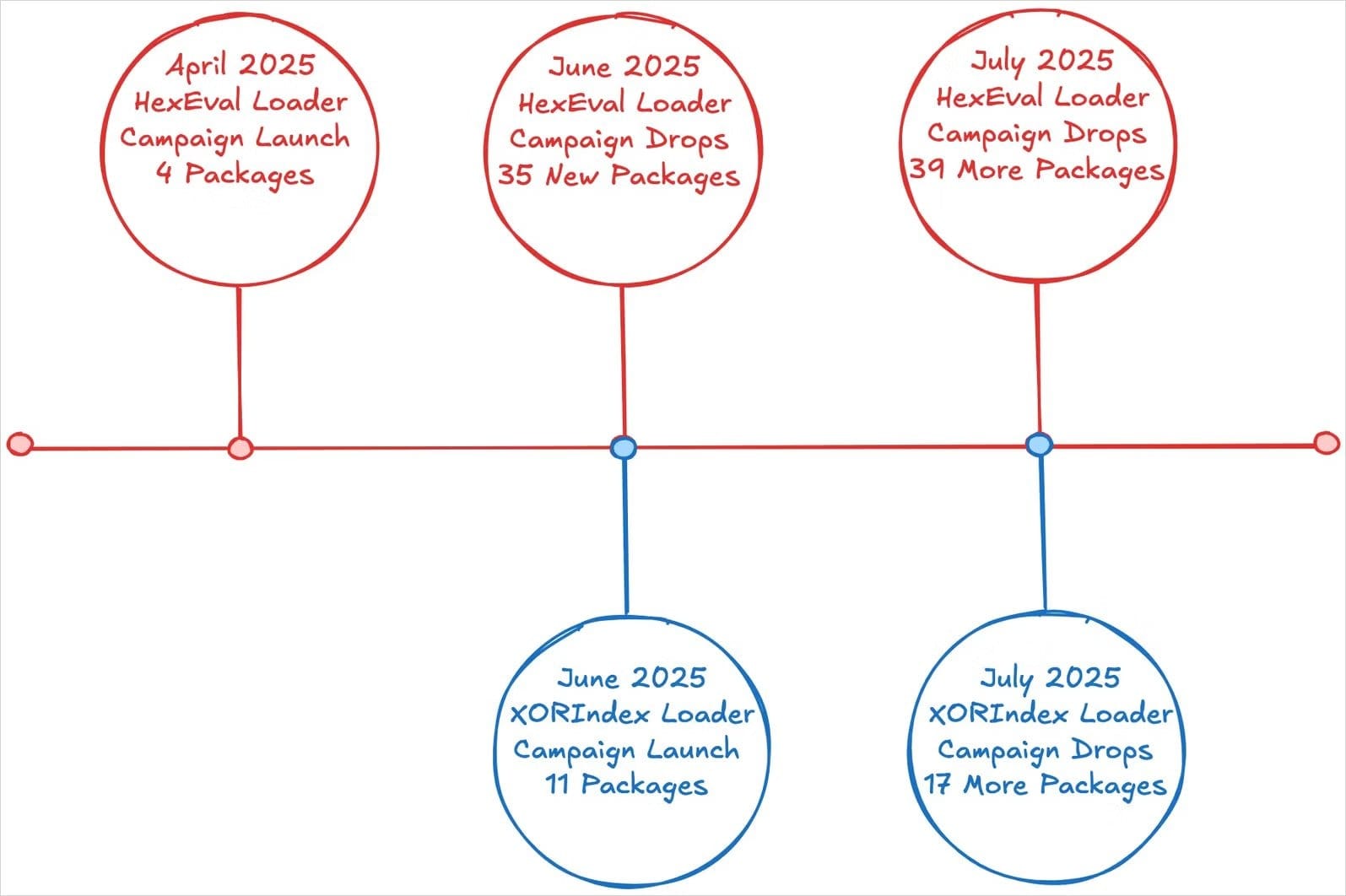
Fake Packages Mimicked Legitimate Tools
The 67 malicious packages impersonated well-known libraries and tools used in front-end development. Some examples include:
vite-meta-pluginvite-postcss-toolsvite-logging-toolvite-proc-logpretty-chalkpostcss-preloaderjs-prettierflowframefigwrapmidd-jsandmiddy-js
These names were chosen to closely resemble legitimate and popular packages, increasing the likelihood of accidental installation by unsuspecting developers.
How XORIndex Works
Once installed, the malicious packages trigger a postinstall script that deploys XORIndex, a newly observed malware loader believed to be used in conjunction with the previously known HexEval Loader.
XORIndex first gathers host and environment data to profile the infected machine, then sends the information to a hardcoded command-and-control (C2) server hosted on Vercel’s cloud infrastructure.
The C2 server responds by sending back one or more JavaScript payloads, which are executed on the victim’s system via eval(). These payloads often include BeaverTail and InvisibleFerret, two backdoors previously linked to North Korean threat actors behind the Contagious Interview campaign.
Once installed, these backdoors allow for remote access, data theft, and the delivery of additional malware.
Ongoing Threat and Evasion Tactics
Security researchers note that the attackers are highly persistent, regularly reusing or modifying existing tools to stay ahead of detection. When malicious packages are removed from npm, they reappear shortly afterward under new names and accounts.
“Defenders should expect new iterations of these loaders in fresh packages, often with minor changes to bypass detection,” researchers warned.
Key Takeaways:
- 67 malicious npm packages were used to distribute the XORIndex malware, with over 17,000 downloads.
- Part of the broader Contagious Interview campaign, active since 2022, targeting developers with fake job offers.
- The malware uses postinstall scripts to deploy a loader that communicates with C2 infrastructure hosted on Vercel.
- Delivers BeaverTail and InvisibleFerret backdoors, linked to North Korean hacking groups.
- Attackers are constantly evolving their tactics, making supply chain attacks on open-source ecosystems a persistent threat.




