Malware Found in Official Endgame Gear Mouse Software

Gaming hardware manufacturer Endgame Gear has confirmed that malware was embedded in the official configuration tool for its OP1w 4k v2 mouse, which was hosted on the company’s website between June 26 and July 9, 2025.
Discovery and Initial Reports
The first signs of trouble emerged on Reddit, where users noticed anomalies in the installer for the OP1w configuration tool. Several red flags were raised:
- The file size increased from 2.3 MB to 2.8 MB
- The file’s properties identified it as a “Synaptics Pointing Device Driver” rather than “Endgame Gear OP1w 4k v2 Configuration Tool”
- VirusTotal flagged the executable as XRed malware, a known backdoor
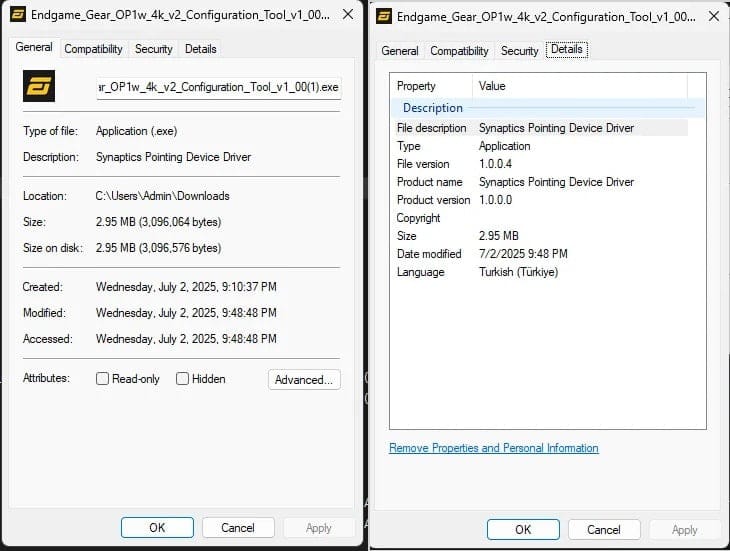
Although the precise capabilities of the malicious payload are still under analysis, Endgame Gear has since verified that the file in question—Endgame_Gear_OP1w_4k_v2_Configuration_Tool_v1_00.exe—was infected.
Scope of the Breach
The infected installer was hosted at:
endgamegear.com/gaming-mice/op1w-4k-v2
Users who downloaded the configuration tool from this specific page during the breach window were likely compromised. In contrast, downloads from the main repository at endgamegear.com/downloads, as well as GitHub and Discord mirrors, remained clean.
As of now, the malicious file has been removed from the site. However, Endgame Gear has not yet disclosed how the breach occurred or whether other systems were affected.
Security Recommendations for Affected Users
Endgame Gear advises anyone who installed the tool from the compromised page to take the following actions immediately:
- Delete all files located in:
C:\ProgramData\Synaptics - Re-download the official tool from the clean source:
https://www.endgamegear.com/downloads
Due to the malware’s keylogging, remote shell, and data exfiltration capabilities, further steps are recommended:
- Run a comprehensive antivirus scan to ensure full removal
- Change all passwords for critical services, including email, banking, cloud storage, and workplace accounts
- Monitor your devices and accounts for any suspicious behavior
Company Response and Future Measures
In response to the incident, Endgame Gear has announced plans to improve its software distribution security:
- Eliminate isolated download pages and centralize all file hosting
- Implement SHA hash verification and digital signing for every downloadable file to verify authenticity and integrity
These steps are aimed at preventing unauthorized tampering and giving users a way to verify legitimate installers.
Background on XRed Malware
The XRed backdoor was previously observed in early 2024, when eSentire reported it being disguised as the Synaptics Pointing Device Driver. At the time, the malware was distributed through trojanized utilities bundled with cheap USB-C hubs sold via third-party Amazon vendors.
This incident reinforces the critical need to download software only from trusted, verifiable sources. Even official websites can be compromised, as shown here. Users should also remain vigilant by scanning new software, verifying digital signatures, and keeping an eye on file behavior after installation.