Malware Downloaded Over 19 Million Times Removed from Google Play Store

Security researchers have uncovered a massive malware campaign on the Google Play Store, where 77 malicious Android applications—collectively downloaded more than 19 million times—were distributing multiple malware families.
According to specialists at Zscaler, the surge included adware apps as well as more dangerous threats such as Joker, Harly, and banking trojans like Anatsa.
“We identified a sharp increase in the number of malicious adware applications on the Google Play Store, alongside threats like Joker, Harly, and banking trojans such as Anatsa,” the researchers reported. “At the same time, there has been a noticeable decrease in activity from malware families like Facestealer and Coper.”
The campaign was discovered during an investigation into a new wave of Anatsa (Tea Bot) infections targeting Android devices.
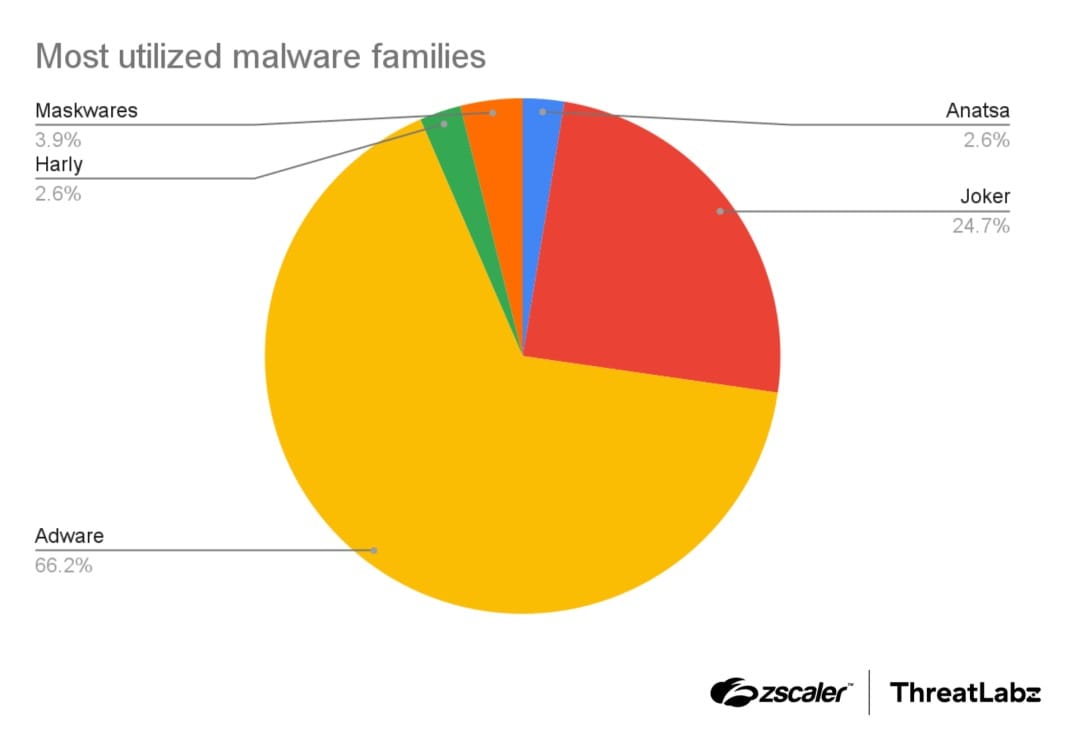
Joker: Still a Major Threat
While more than two-thirds (66%) of the malicious apps contained adware, Joker remained the most prevalent threat, appearing in nearly 25% of the infected applications. Once installed, Joker can:
- Read and send SMS messages
- Take screenshots
- Make calls
- Steal contact lists and device information
- Subscribe victims to premium services
Maskware and Harly Variants
Researchers also identified “maskware”—apps disguised as legitimate utilities such as file managers, photo editors, or games. These apps function as advertised but secretly harvest credentials, banking data, geolocation, and SMS content.
A Joker variant known as Harly was also spotted. Its malicious payload is buried deep within seemingly legitimate apps, making detection more difficult. In March, analysts at Human Security warned that Harly was being distributed through popular categories like games, wallpapers, and flashlight apps.
Anatsa Banking Trojan Evolves
The latest version of Anatsa shows significant expansion, now capable of targeting 831 banking and cryptocurrency applications, up from 650 previously. The malware can:
- Download phishing pages and keylogger modules from its command-and-control (C2) server
- Target users in Germany and South Korea
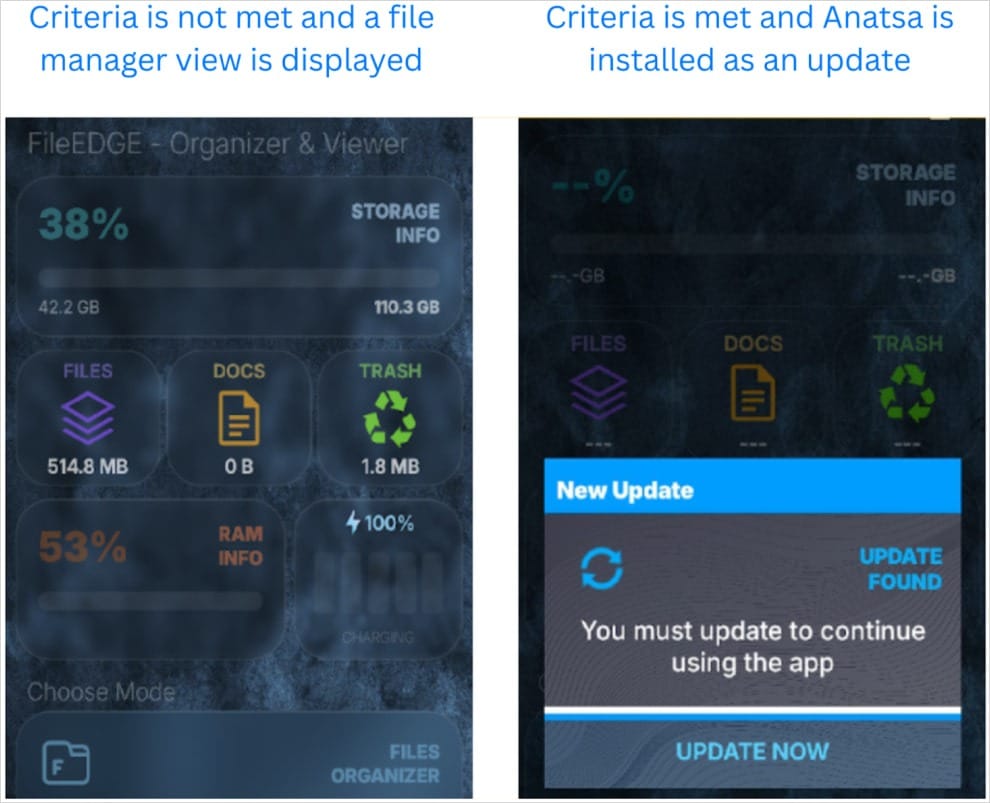
- Spread through apps like “Document Reader – File Manager”, which download Anatsa after installation to bypass Google’s checks
To avoid detection, the attackers shifted from dynamically loading DEX code to unpacking malware directly from JSON files, which are later deleted. Anatsa also employs corrupted APK archives, DES string encryption during execution, and emulator detection techniques. Package names and hashes are rotated regularly to complicate analysis.
Google’s Response
Zscaler confirmed that Google has now removed all 77 malicious applications from the Play Store.




