Linux Malware "Koske" Hides in Pictures of Cute Pandas

Analysts from AquaSec have identified a novel strain of Linux malware named Koske, which conceals its payload inside JPEG images of pandas. Believed to be developed using artificial intelligence (AI), Koske is designed to infiltrate Linux systems by embedding malicious code directly into memory via deceptive image files.
Adaptive Behavior Hints at AI Involvement
Described as a "sophisticated Linux threat," Koske exhibits characteristics that suggest the use of large language models (LLMs) or automation frameworks during its development. Its core function is to hijack system resources—both CPU and GPU—for mining a broad array of cryptocurrencies.
While the malware’s exact origin remains uncertain, investigators traced Serbian IP addresses, found Slovak phrases in the script, and identified GitHub repositories hosting the miner infrastructure—indicators that the operation may involve actors from Central or Eastern Europe.
Initial Access and Execution Strategy
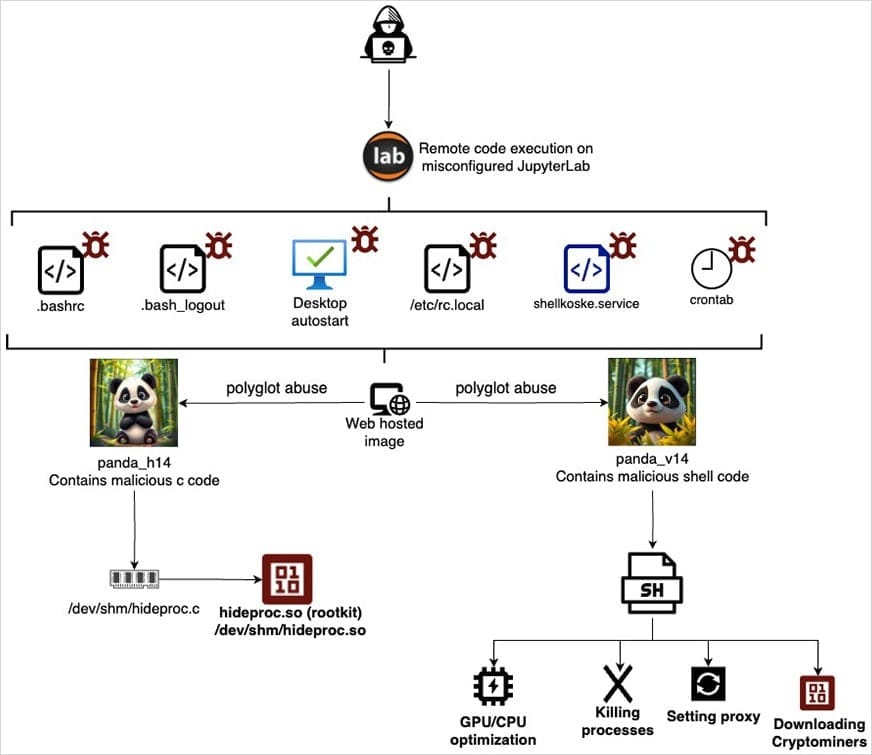
Koske gains entry by exploiting misconfigured JupyterLab instances. Once inside, it uploads two panda-themed JPEG images via legitimate platforms like OVH images, Freeimage, and Postimage. These images act as polyglot files—documents that can be interpreted as multiple formats depending on the context.
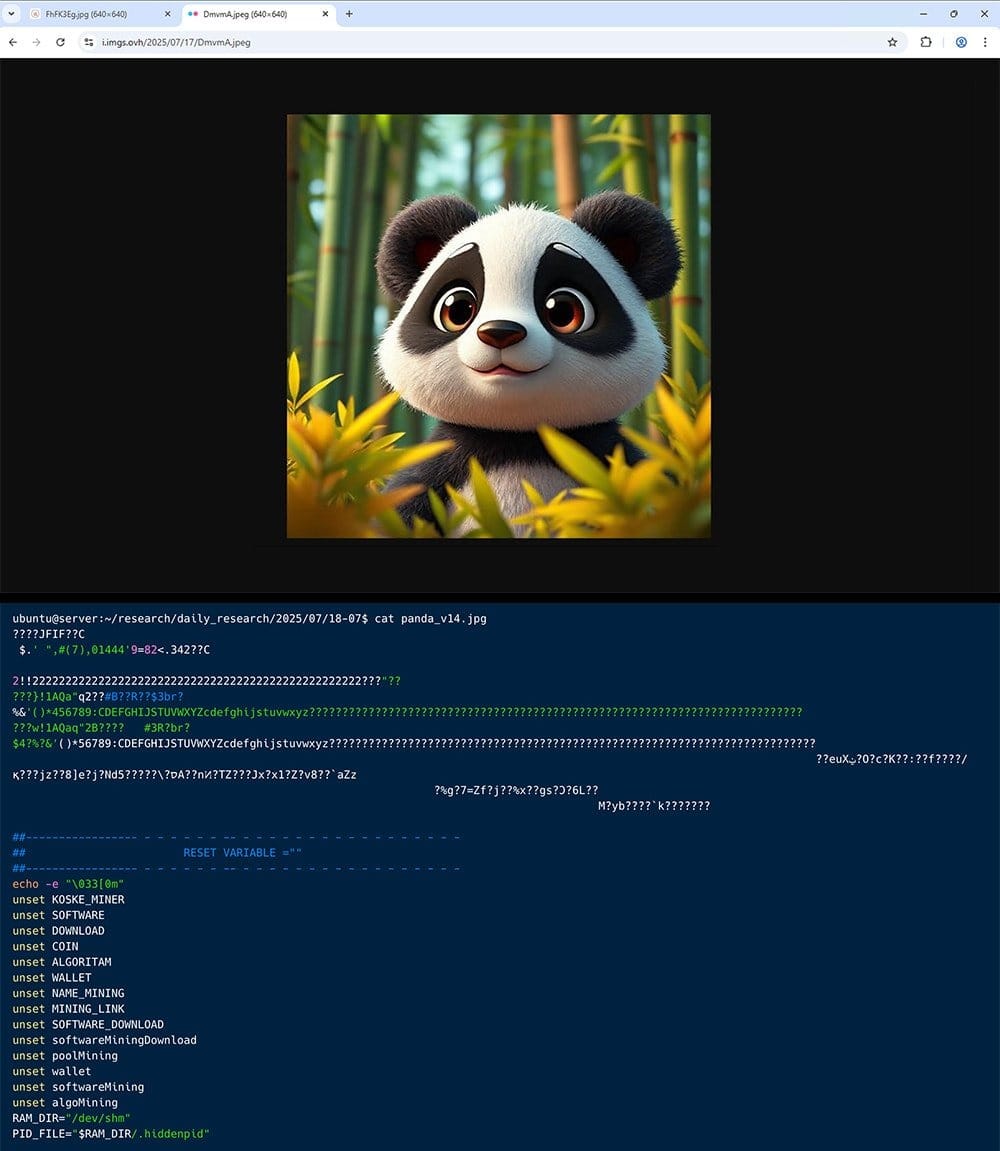
Unlike traditional steganography (which hides data within images), Koske’s images are crafted to be dual-purpose:
- They display as normal JPEGs when opened conventionally
- They execute malicious code when interpreted by a shell or script processor
Each panda image includes:
- A valid JPEG header
- Appended shell scripts and C code
This technique allows the malware to remain inconspicuous to users and basic scanning tools.
Dual Payload Structure and Persistence Tactics
Each image file delivers a distinct payload, which runs in tandem:
- C-Based Payload:
- Compiled and executed in memory
- Acts as a rootkit using a shared object (.so)
- Provides deep system access
- Shell Script Payload:
- Runs in memory using native Linux utilities
- Maintains persistence while minimizing artifacts
To reinforce access and evade network restrictions, the shell script:
- Overwrites
/etc/resolv.confwith Cloudflare and Google DNS - Locks the file with
chattr +i(making it immutable) - Flushes iptables rules
- Clears proxy environment variables
- Launches a module that brute-forces usable proxies via
curl,wget, and raw TCP requests
These actions showcase a level of environmental awareness and adaptability uncommon in typical malware strains.
Smart Mining With Failover Capability
Koske evaluates the infected system’s hardware profile before selecting a compatible miner. It supports at least 18 cryptocurrencies—including Monero, Ravencoin, Zano, Nexa, and Tari.
If the preferred mining pool or currency is unavailable, Koske automatically fails over to a backup option pulled from an internal list. This redundancy reinforces the theory that Koske was built with AI-assisted decision logic and advanced automation in mind.
Key Takeaways
- Koske hides in panda JPEGs using polyglot file techniques—not steganography.
- AI-assisted development is likely, based on adaptability and automation patterns.
- Delivers dual payloads: a C-based rootkit and a stealthy shell script.
- Employs advanced persistence: DNS hijacking, proxy brute-forcing, and system cleanup.
- Mines over 18 cryptocurrencies, with auto-fallback if the default fails.
Koske represents a new class of AI-augmented malware capable of adapting to diverse environments and evading detection. For Linux administrators and security professionals, this is a reminder: even a cute panda can carry a serious threat.