Lenovo Webcams Could Be Weaponized in BadUSB-Style Attacks

Security researchers at Eclypsium have demonstrated a novel attack dubbed “BadCam” at DEF CON 33, revealing vulnerabilities in certain Lenovo webcam models that can be remotely repurposed as BadUSB attack tools.
Key Details of the BadCam Attack (CVE-2025-4371)
- First real-world demonstration of remotely hijacking Linux-based USB peripherals for malicious purposes.
- Enables stealthy keystroke injection and payload delivery, independent of the host operating system.
- Unlike traditional BadUSB attacks—which require physical device tampering—this exploit works remotely, with no need to disconnect or replace the hardware.
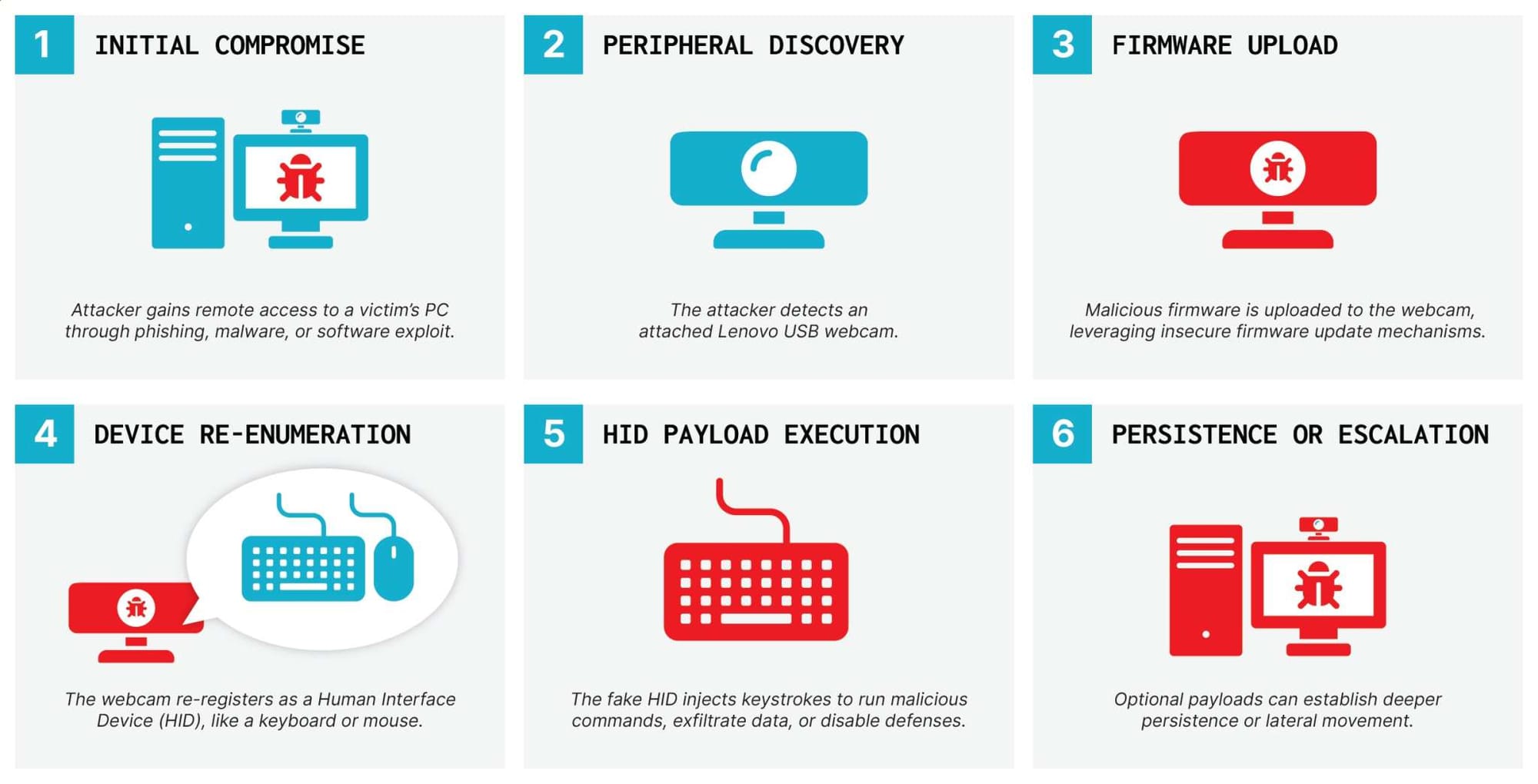
How BadCam Works
- Initial Compromise – The attacker first gains remote code execution on the host system.
- Firmware Flashing – The webcam’s firmware is reflashed to emulate malicious HID devices (e.g., keyboards) or additional USB peripherals.
- Persistence – The compromised webcam retains normal functionality while executing hidden attacks:
- Keystroke injection (e.g., launching backdoors)
- Malware deployment
- Lateral movement to other systems when the camera is reconnected
Affected Devices
- Lenovo 510 FHD Webcam
- Lenovo Performance FHD Webcam
Both models run SigmaStar firmware with critical flaws:
- No firmware validation or signature checks
- Linux OS with USB Gadget support, enabling full device takeover
Exploitation Chain
The attack can be paired with a separate Linux kernel flaw (CVE-2024-53104) to deploy malicious firmware onto connected webcams.
Once compromised, cameras persist across OS reinstalls and can reinfect systems upon reconnection.
Vendor Response
Lenovo and SigmaStar released patched firmware (v4.8.0) in April 2025, along with a jointly developed tool to detect and remediate affected devices.
Broader Implications
- Enterprise Risk – Many organizations trust peripherals without realizing they run full operating systems capable of executing remote commands.
- Supply Chain Threat – Other Linux-based USB devices—such as printers, docking stations, and external storage—may share similar vulnerabilities.
Eclypsium’s Warning
“This attack highlights an invisible but critical threat vector: unsigned or poorly secured firmware in peripherals can compromise not just the host, but any future systems the device connects to—evading traditional defenses.”
Recommendations
- Update firmware for Lenovo webcams and other USB peripherals.
- Monitor USB devices for unusual or unauthorized behavior.
- Restrict peripheral permissions in high-security environments.
Key Takeaway: BadCam represents a paradigm shift—malicious peripherals no longer require physical tampering to pose a significant security risk.




