HTTP/2 Vulnerability "MadeYouReset" Can Be Used for Large-Scale DDoS Attacks

A newly disclosed vulnerability in several HTTP/2 implementations, dubbed MadeYouReset, can be exploited to launch powerful distributed denial-of-service (DDoS) attacks.
Scope of the Vulnerability
Researchers from Imperva, Deepness Lab, and Tel Aviv University confirmed that the flaw has been assigned the primary identifier CVE-2025-8671. However, the issue is broad in scope, with vendors issuing their own advisories and CVEs:
- Apache Tomcat (CVE-2025-48989)
- F5 BIG-IP (CVE-2025-54500)
- Netty (CVE-2025-55163)
- Vert.x and Varnish (vendor advisories pending)
In addition, products from Mozilla, Wind River, Zephyr Project, Google, IBM, and Microsoft are also reported as affected, exposing a wide ecosystem of systems to risk.
How MadeYouReset Works
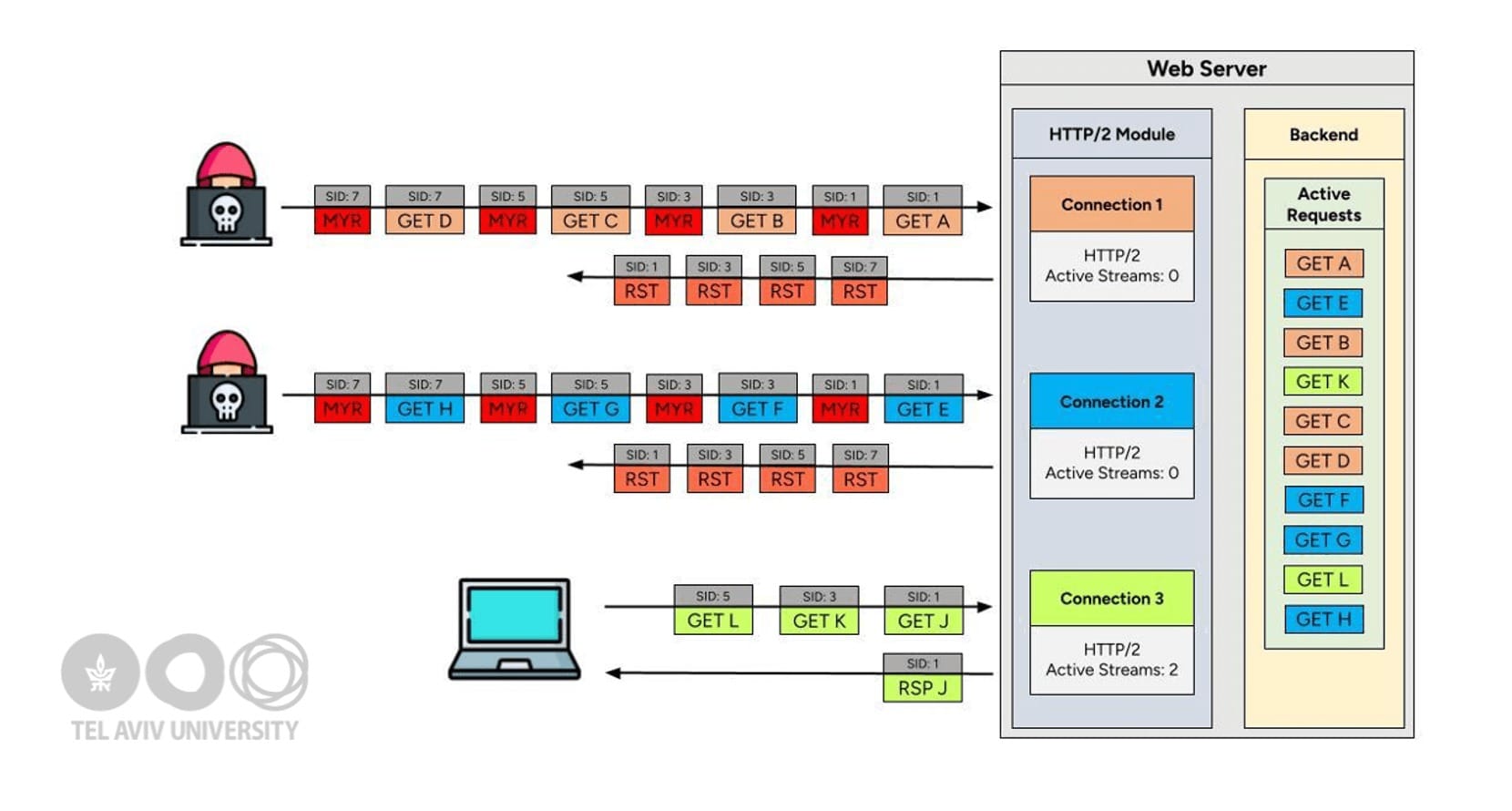
At the protocol level, HTTP/2 limits each client TCP connection to 100 concurrent requests, a safeguard intended to blunt denial-of-service attempts. MadeYouReset bypasses this restriction.
According to Imperva researchers:
“MadeYouReset bypasses the standard server limit of 100 concurrent HTTP/2 requests per client TCP connection. With this flaw, attackers can send thousands of requests, leading to denial-of-service conditions for legitimate users—and in some cases, server crashes or memory exhaustion.”
The attack is conceptually related to the Rapid Reset and Continuation Flood vulnerabilities, both exploited in 2023 zero-day DDoS campaigns that set records for requests per second (RPS). Like those attacks, MadeYouReset abuses the RST_STREAM frame (used both to cancel client requests and to signal stream errors).
The attack sequence unfolds as follows:
- The attacker begins a valid HTTP/2 stream.
- An error is intentionally triggered, forcing the server to reset the stream via RST_STREAM.
- The backend continues to compute a response even though the stream was canceled.
- By repeating this with specially crafted frames, attackers create massive overhead without ever sending their own RST_STREAM frames.
This technique allows adversaries to bypass existing protections against Rapid Reset, while blending in with what appears to be normal traffic.
Detection and Mitigation
One of the challenges with MadeYouReset is its stealth: traffic generated during an attack often resembles legitimate client behavior, complicating detection efforts.
Experts recommend several defensive measures:
- Stricter protocol validation to reject malformed frames.
- Enhanced stream state tracking to block invalid transitions.
- Connection-level rate limiting to throttle abusive clients.
- Anomaly detection and behavioral monitoring to identify suspicious patterns.
As Imperva researchers summarize:
“MadeYouReset serves as a reminder that even well-formed traffic can be turned into a weapon if it isn’t scrutinized closely enough.”




