Hackers Embedded a Raspberry Pi into a Bank’s Network in Attempted Robbery

A hacker group known as UNC2891—also tracked as LightBasin—attempted to rob a bank using a 4G-enabled Raspberry Pi cleverly hidden inside a branch. According to a report from Group-IB, the attackers connected the single-board computer to the same network switch as an ATM. This gave them a direct path into the bank’s internal network, allowing for lateral movement and remote access.
The breach was discovered during an investigation into suspicious network activity. Researchers say the attackers’ objective was to spoof ATM authorization and carry out fraudulent cash withdrawals.
While the attempt ultimately failed, analysts say the incident highlights a rare and advanced hybrid attack—one that combines both physical access and remote command and control, layered with multiple anti-forensics techniques to avoid detection.
A Familiar Threat Actor
LightBasin has been active since at least 2016 and has consistently targeted financial institutions. In a notable case from 2022, cybersecurity firm Mandiant detailed a Unix rootkit dubbed Caketap, designed to run on Oracle Solaris systems widely used in banking.
The purpose of Caketap, researchers concluded, was to intercept sensitive data such as card verification details and PIN codes from compromised ATM servers. This data could then be used to perform unauthorized transactions.
The malware specifically targeted communication destined for the bank’s Payment Hardware Security Module (HSM)—a tamper-resistant device used to manage cryptographic keys for PINs, magnetic stripes, and EMV chip data.
How the Attack Unfolded
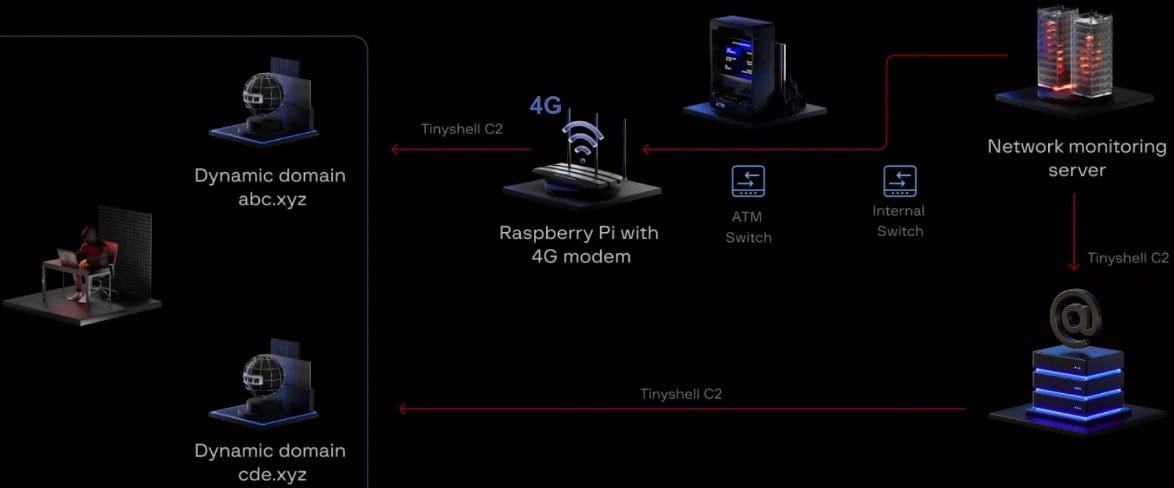
In this latest incident, Group-IB reports that LightBasin operatives gained physical access to an undisclosed bank branch—either directly or by bribing an insider. Once inside, they discreetly installed a Raspberry Pi with a 4G modem on the same network switch as the ATM.
This move allowed the attackers to maintain persistent, remote access to the bank’s internal network, bypassing firewall protections by leveraging the mobile network.
The Raspberry Pi was preloaded with a backdoor tool known as TinyShell, which established an encrypted command-and-control (C2) channel over 4G.
As the attackers moved deeper into the network, they accessed a Network Monitoring Server with broad privileges, then pivoted to a mail server with direct internet access. This allowed them to remain inside the bank’s network even after the physical device was eventually discovered and removed.
Anti-Forensics and Persistence
To maintain stealth, the attackers disguised their lateral movement tools under the name lightdm, mimicking the legitimate Linux display manager. They also used advanced anti-forensics techniques by mounting alternative file systems—tmpfs and ext4—over the /proc/[pid] directories of malicious processes. This effectively hid key metadata from standard forensic tools.
According to researchers, the ultimate goal was once again to deploy the Caketap rootkit on high-value systems—but the plan was cut short when the attack was detected mid-operation.