Hacked npm Packages Downloaded More Than 2.6 Billion Times Weekly

Researchers are warning of what may be the largest supply chain attack in history. Attackers injected malware into several of the most widely used npm packages—collectively downloaded more than 2.6 billion times each week. The breach was made possible when hackers compromised a maintainer’s account through a phishing attack.
How the Attack Happened
On the evening of September 8, 2025, maintainer Josh Junon, known online as Qix, reported that his accounts had been hijacked. He explained that he received a phishing email from support@npmjs[.]help, a domain registered just three days earlier. The website was crafted to look like the legitimate npmjs.com domain.
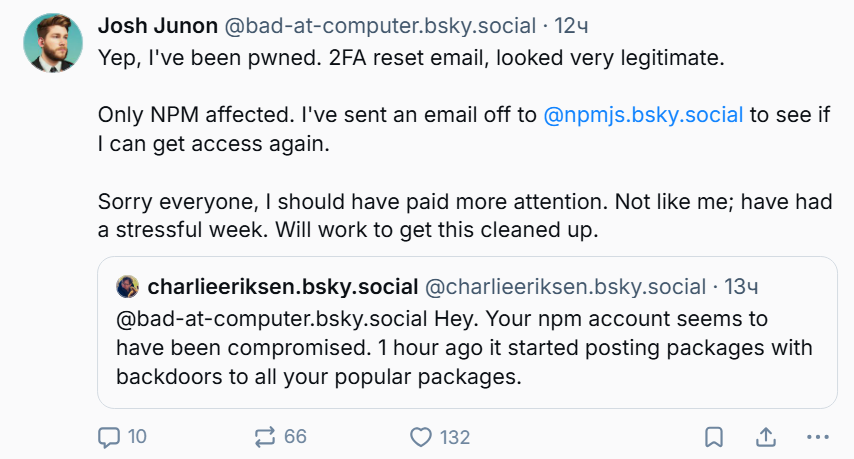
The email, also sent to other maintainers, threatened that accounts would be blocked by September 10 unless recipients updated their two-factor authentication (2FA) credentials:
“As part of our ongoing commitment to account security, we are asking all users to update their two-factor authentication (2FA) credentials. Our records indicate that it has been more than 12 months since your last 2FA update… Accounts with outdated 2FA credentials will be temporarily locked after September 10, 2025.”

Analysis by Bleeping Computer shows the phishing site contained a login form that sent all entered credentials to:https://websocket-api2[.]publicvm[.]com/images/jpg-to-png.php?name=[name]&pass=[password].
Junon later apologized publicly:
“I should have been more careful. It’s totally unlike me. I’ve had a hectic week. I’ll work to fix all of this.”
The npm team has since begun removing the malicious package versions uploaded by the attackers.
Scale of the Breach
The compromised packages maintained by Qix account for more than 2.6 billion downloads weekly. They include direct-use libraries as well as critical dependencies:
- [email protected] – 299.99M
- [email protected]@6.2.2 – 371.41M
- [email protected] – 357.6M
- [email protected] – 287.1M
- [email protected] – 261.17M
- [email protected] – 243.64M
- [email protected] – 193.5M
- [email protected] – 197.99M
(and others, each with millions of downloads).
“By compromising Qix, the attackers gained the ability to distribute malicious versions of packages on which countless applications, libraries, and frameworks indirectly depend,” researchers from Socket warned. “Given the scale, this was clearly a targeted attack designed for maximum coverage.”
The Malware
According to Aikido Security, attackers injected about 280 lines of malicious code into the index.js files of affected packages. The malware acts as an interceptor, capable of:
- Monitoring network traffic and application APIs
- Injecting itself into browsers to track cryptocurrency wallets
- Replacing recipient wallet addresses for Ethereum, Bitcoin, Solana, Tron, Litecoin, and Bitcoin Cash
- Intercepting JavaScript functions such as
fetch,XMLHttpRequest, and wallet APIs (window.ethereum, Solana, etc.)
In short, it manipulated what users saw, interfered with API calls, and altered transactions before they were signed—redirecting funds to attacker-controlled wallets.
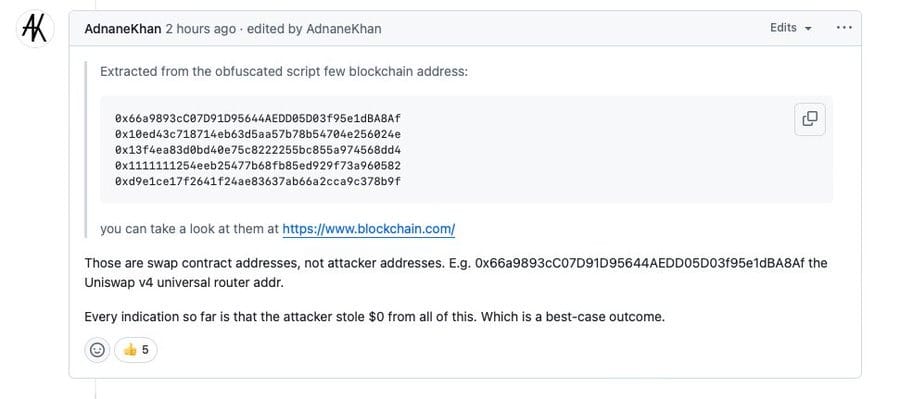
Limited Damage—But Major Risk
Despite the scale, early analysis suggests the attackers’ execution was flawed. Security Alliance (SEAL) and VXUnderground researchers note the malware sometimes substituted addresses belonging not to the attackers but to Uniswap and other swap contracts—meaning stolen funds were effectively lost. Estimated attacker gains range from a few cents to about $50.
Even so, the incident triggered urgent warnings. Charles Guillemet, CTO of Ledger, advised:
“Infected packages have already been downloaded over a billion times, which could compromise the entire JavaScript ecosystem. If you use a hardware wallet, check every transaction carefully before signing. If you don’t, avoid on-chain transactions for now until we fully understand the scope.”