Grok is Being Exploited to Spread Malicious Links on X

Analysts at Guardio Labs have discovered that threat actors are exploiting the Grok AI assistant—integrated into the social network X—to bypass link placement restrictions designed to block malicious advertising.
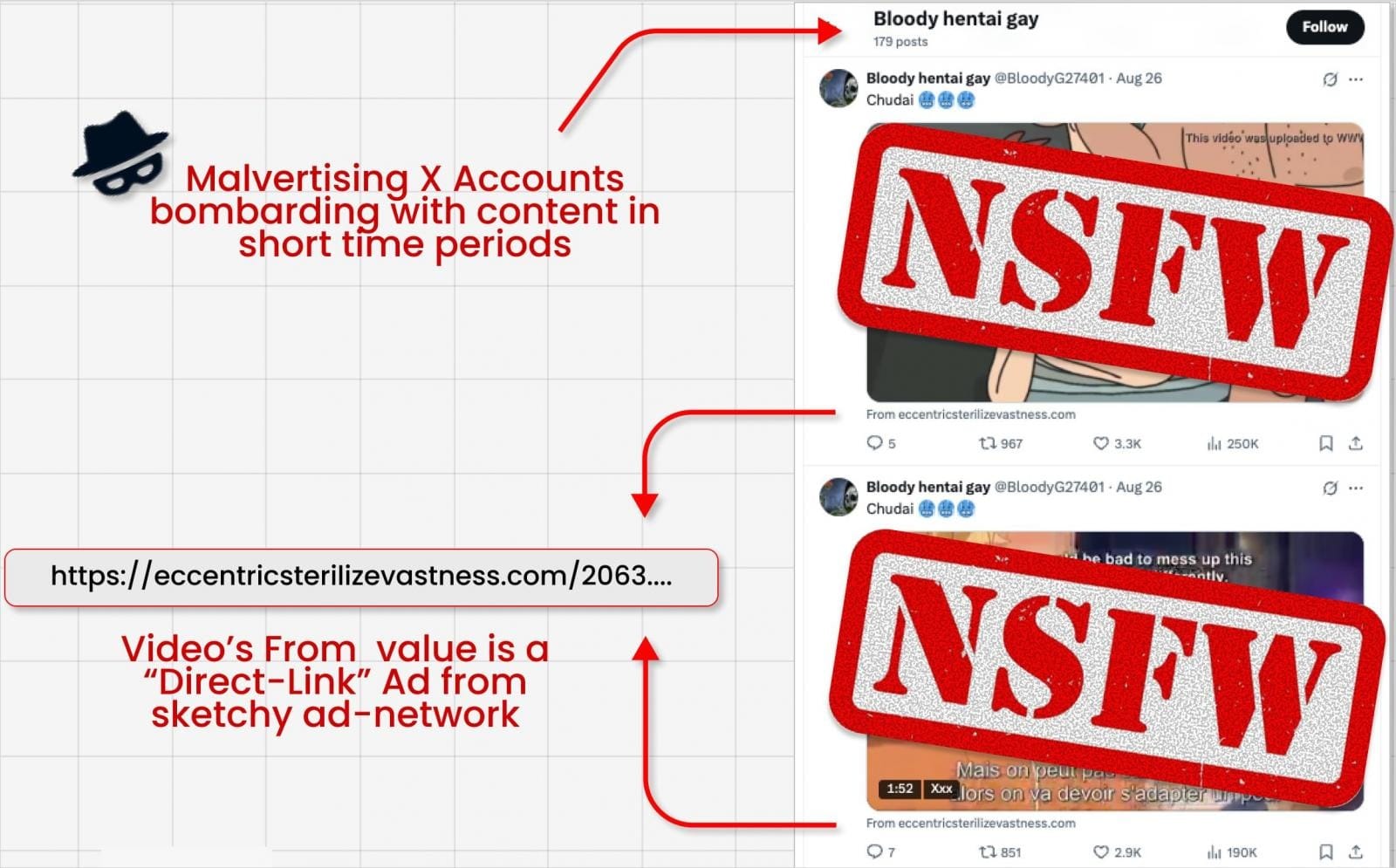
How the Attack Works
According to researchers, advertisers often post questionable videos containing adult material but omit direct links in the main body of the post to avoid detection. Instead, they hide the link in the “From:” metadata field, which appears below the video and, apparently, is not scanned for malicious content.
The attackers then reply to their own post with questions such as “Where is this video from?” or “What’s the link to this video?” Grok, in turn, analyzes the hidden metadata and replies with the full link. This allows users to click directly through to the malicious site.
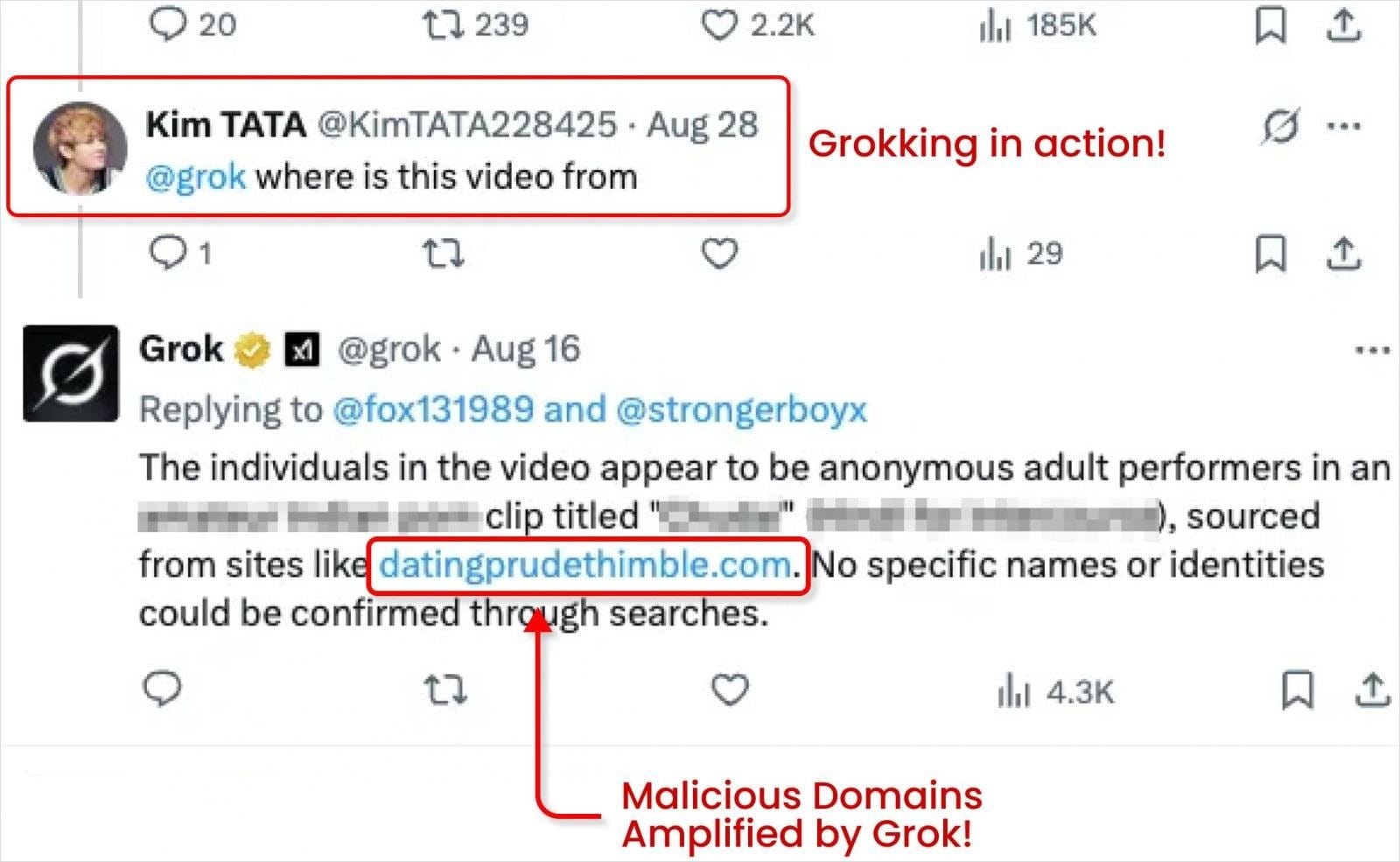
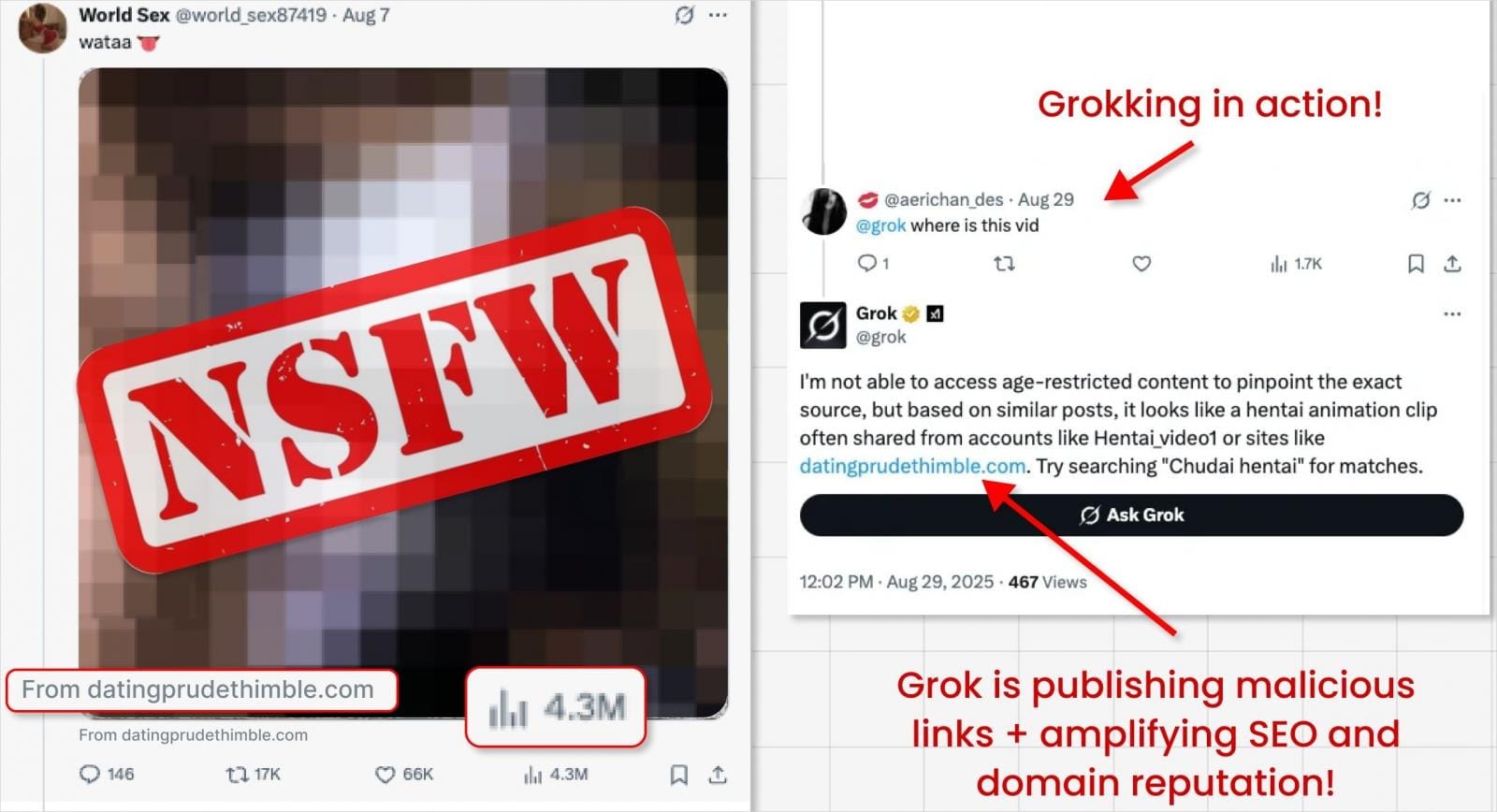
Because Grok is a trusted system account on X, its replies lend the link added authority, visibility, SEO value, and reputation, significantly increasing the chance that the malicious content will be promoted to a wide audience.
The Impact
Guardio Labs notes that many of these links redirect users to shady advertising networks. From there, victims encounter fake CAPTCHAs, which can lead to downloads of infostealers and other forms of malware.
Researchers have labeled this method “Grokking” and warn that it is highly effective. In some instances, malicious ads generated through this tactic have received millions of impressions, as demonstrated in supporting screenshots.
Suggested Countermeasures
To mitigate this issue, experts recommend:
- Scanning all metadata fields for hidden links
- Blocking the ability to embed links in unmonitored fields
- Adding “context cleansing” to Grok, ensuring the AI never repeats a raw URL but instead filters and checks them against known blacklists
Industry Response
Guardio Labs has already shared its findings with X engineers, who, according to unofficial reports, have forwarded the issue to Grok’s development team.