GPUHammer: Rowhammer Attack Adapted for Nvidia GPUs

Nvidia is urging users to enable System-Level Error-Correcting Code (ECC) after researchers demonstrated that GDDR6 memory in its GPUs is vulnerable to a variant of the infamous Rowhammer attack.
“The risk of a successful Rowhammer exploit depends on the DRAM model, platform, architectural specifics, and system settings,” the company stated.
What Is Rowhammer?
First identified in 2014 by researchers at Carnegie Mellon University, Rowhammer is a hardware-based vulnerability that exploits the electrical layout of DRAM. By rapidly and repeatedly accessing (“hammering”) specific memory rows, attackers can induce bit flips in adjacent rows.
These memory cells store data as electrical charges—representing binary 1s and 0s. When a row is hammered, electrical interference can cause nearby rows to leak charge, flipping bits from 0 to 1 or vice versa.
These seemingly random flips can be weaponized to steal sensitive data, escalate privileges, or even corrupt AI model outputs.
GPUHammer: Rowhammer on Nvidia GPUs
A new study by researchers at the University of Toronto has demonstrated that Rowhammer can be adapted to target GDDR6 memory on Nvidia’s RTX A6000 GPU—coining the exploit GPUHammer.
Key Findings:
- While GDDR6 is more resilient than DDR4 (due to higher latency and faster refresh cycles), it is still vulnerable.
- On the Nvidia RTX A6000 (48GB GDDR6), researchers observed bit flips across all four tested DRAM banks.
- The minimum number of activations (TRH) required to induce a flip was ~12,000—similar to traditional DDR4-based Rowhammer attacks.
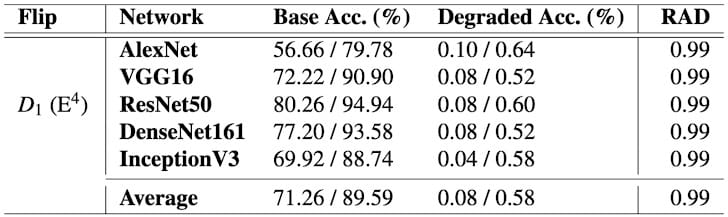
- In one experiment, a single bit flip reduced an AI model’s classification accuracy from 80% to 0.1%.
Nvidia’s Recommendations
In its security advisory, Nvidia confirmed that GPUHammer was only successful when System-Level ECC was disabled. The company strongly advises enabling ECC on all supported platforms, particularly in data centers, AI workloads, and mission-critical environments.
Recommended ECC-Enabled GPU Models:
Data Center GPUs
- Ampere: A100, A40, A30, A16, A10, A2, A800
- Ada: L40S, L40, L4
- Hopper: H100, H200, GH200, H20, H800
- Blackwell: GB200, B200, B100
- Turing: T1000, T600, T400, T4
- Volta: Tesla V100, Tesla V100S
Workstation GPUs
- Ampere RTX: A6000, A5000, A4500, A4000, A2000, A1000, A400
- Ada RTX: 6000, 5000, 4500, 4000, 4000 SFF, 2000
- Blackwell RTX PRO
- Turing RTX: 8000, 6000, 5000, 4000
- Volta: Quadro GV100
Embedded & Industrial GPUs
- Jetson AGX Orin Industrial
- IGX Orin
Note: Newer GPUs such as the Blackwell RTX 50 Series and Blackwell/Hopper data center models come with built-in ECC protection, requiring no manual configuration.
Performance Impact of ECC
While enabling ECC enhances security, it can introduce modest performance trade-offs:
- Up to 10% reduction in AI model performance
- Up to 6.5% decrease in available memory
Conclusion
GPUHammer is a highly targeted and technically demanding attack, but its implications—especially for AI research and data integrity—are serious. With ECC available on most modern Nvidia hardware, enabling it is a critical defense against emerging memory-based threats.
Stay secure—hardware-level vulnerabilities are evolving faster than ever.




