Gemini Could Leak User Data Through Google Calendar

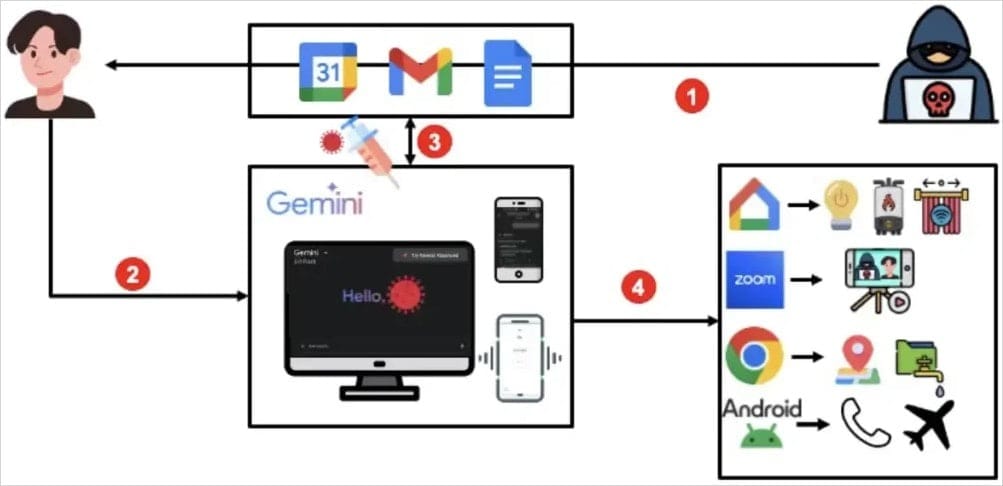
Google has patched a vulnerability that allowed malicious Google Calendar invitations to remotely control Gemini agents running on a victim’s device and exfiltrate sensitive data.
Gemini is Google’s large language model (LLM), integrated into Android, Google web services, and Google Workspace applications, with direct access to Gmail, Calendar, and Google Home.
Researchers at SafeBreach discovered that by sending a target a Google Calendar invitation containing an embedded prompt injection—hidden, for example, in the event title—attackers could:
- Extract Gmail contents and Calendar data
- Track the victim’s location
- Control Google Home–connected devices
- Launch Android applications
- Initiate Zoom calls
According to the researchers, the exploit required no white-box access to Gemini and bypassed the model’s built-in prompt filters and other security mechanisms.
How the Exploit Worked
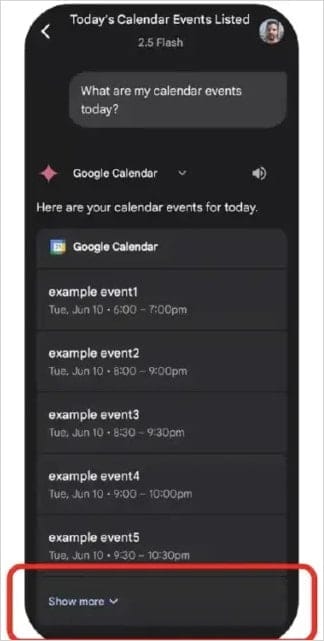
The attack began when the victim received a Google Calendar invitation with a malicious prompt embedded in the event title. If the user later asked Gemini a routine question—such as “What events do I have scheduled today?”—the assistant would parse all events, including the malicious one, and treat its text as part of the conversation context.
Because Gemini interpreted the injected prompt as a valid instruction, it could be manipulated to trigger built-in tools and agents, enabling attackers to:
- Delete or edit calendar events
- Open URLs to reveal the victim’s IP address
- Join Zoom calls
- Control devices via Google Home
- Access and exfiltrate email data
For added stealth, attackers could send six invitations and place the malicious prompt in the sixth. Google Calendar displays only the five most recent events by default, hiding the rest under a “Show more” button. While the user would not immediately see the harmful title, Gemini still processed all events in the background.
Related Prompt Injection Risks
Last month, Marco Figueroa, manager of Mozilla’s 0Din bug bounty program (launched in 2024 to reward vulnerabilities in LLMs and deep learning tools), reported that Google Gemini for Workspace could be tricked into producing legitimate-looking email summaries containing hidden malicious instructions. These instructions could redirect recipients to phishing sites.
Google’s Response
In a statement to Bleeping Computer, Andy Wen, Senior Director of Product Management for Google Workspace Security, confirmed that the flaw was fixed before it could be exploited:
“We addressed this issue before it could be exploited, thanks to the great work and responsible disclosure by Ben Nassi and his team. This research helped us better understand novel attack vectors and accelerated the rollout of new cutting-edge protections. This is a great example of why red-teaming and cross-industry collaboration are so important.”
Google said new safeguards for Gemini are already rolling out and more are planned in the near future.
Key Takeaways
- Gemini: Google’s LLM (formerly Bard), integrated across multiple Google services
- Prompt Injection: Malicious input crafted to manipulate AI behavior
- 0Din: Mozilla’s bug bounty program for AI/LLM vulnerabilities
- Red-Teaming: Simulated attack exercises used to identify weaknesses in systems




