Flipper Developers Deny Existence of “Secret Firmware” for Hacking Cars

The issue of car theft using the Flipper Zero has resurfaced in global headlines. This time, hackers claim to be selling a “secret firmware” for the device that allegedly works against cars from Ford, Audi, Volkswagen, Subaru, Hyundai, Kia, and several other manufacturers. The developers behind Flipper Zero say these claims are false.
Last week, the publication 404 Media reported on the underground trade of modified firmware for Flipper Zero, marketed as a tool for hacking and stealing cars.
Journalists interviewed a hacker known as Daniel, reportedly based in Russia, and his partner, Derrow, who allegedly developed and sold customized “Unleashed” firmware on darknet forums.
Daniel claimed he acquired portions of source code from others and used them to create firmware that could, in theory, be used in auto theft, though he also suggested it was popular among auto repair professionals. According to these hackers, the modified firmware enables a Flipper device to intercept key fob signals and calculate the next unlocking code, effectively creating a “shadow copy” of a car key. Their documentation suggests this attack method could affect nearly 200 car models, including some 2025 editions from Ford, Audi, Volkswagen, Subaru, Hyundai, Kia, Fiat, and Mitsubishi.
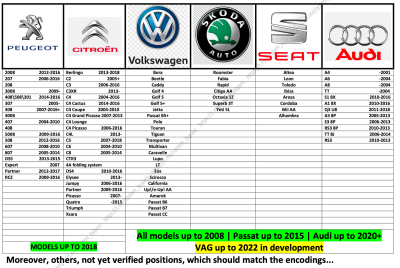
Two versions of the firmware are advertised: a basic package for $600, and an extended version for $1,000 that includes updates and support. Payments are requested in cryptocurrency, and buyers must provide proof of device ownership through photos of the Flipper Zero box and its serial number to activate the firmware. Daniel told reporters he had sold to roughly 150 buyers over two years, while Derrow claimed that “sales are through the roof.”
The article raised concerns that widespread adoption of such tools could fuel a new wave of car thefts. By 2026, the publication warned, the notorious “Kia Boys” trend could evolve into a “Flipper Boys” phenomenon.
In response to the growing coverage, Flipper Zero co-creator Pavel Zhovner published a detailed rebuttal on the project’s official blog.
“In some darknet stores, they started selling so-called ‘private’ firmware for Flipper Zero, claiming that it can be used to hack countless cars. Allegedly, information about new vulnerabilities that allow hacking dynamic protocols like KeeLoq has been leaked. In reality, all these methods were published over 10 years ago. Nothing new. The authors of such firmware simply recycle known vulnerabilities, passing them off as ‘new hacks.’ And, importantly, these vulnerabilities have no relation to actual car thefts because they do not allow starting the engine,” Zhovner wrote.
Zhovner explained that KeeLoq—an encryption system developed in the 1980s—was once widely used in garage doors, alarms, and older car systems. KeeLoq is a rolling code system (each transmission uses a new encrypted signal) secured with a 64-bit manufacturer key.
According to Zhovner, the flaw lies in how carmakers reused the same key across entire model lines. If such a key leaked, criminals could intercept signals from any fob of that brand.
“The authors of ‘hacker’ firmware are simply distributing old keys stolen from various automakers. There is nothing new about this; such vulnerabilities were described in detail back in 2006,” Zhovner noted. “Since then, automakers have moved to modern radio protocols with two-way authentication, where the car and the key exchange signals to verify authenticity.”
Zhovner also recalled that in 2024, when the Canadian government announced plans to ban Flipper Zero and similar devices, the development team had already clarified that the device is not a tool for car theft.
He emphasized that professional thieves typically rely on relay attacks against keyless entry and engine start systems—using specialized transmitters to extend the signal from the legitimate key, fooling the car into believing the fob is nearby.
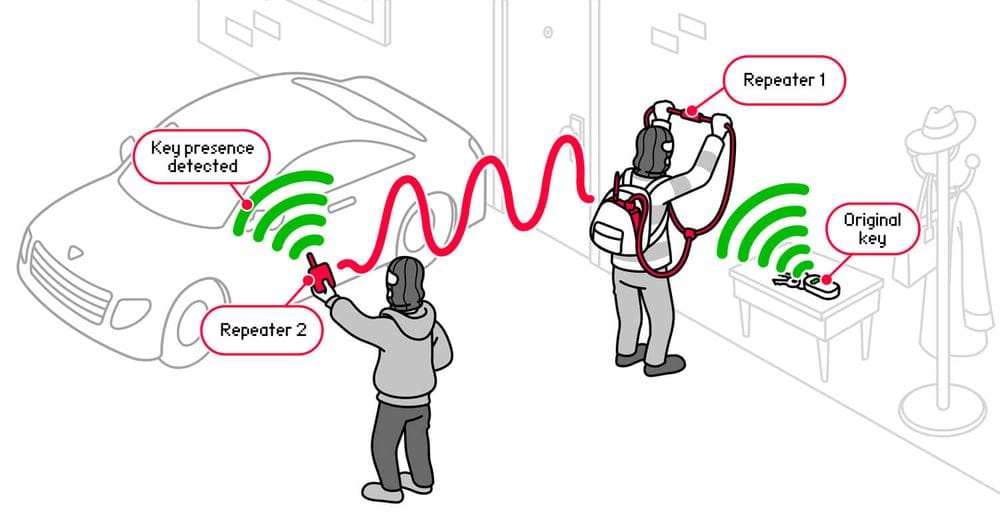
“If your car can be attacked using a Flipper Zero, it can just as easily be hacked with a piece of wire,” Zhovner concluded.




