F6 Helps Disrupt Infrastructure of Hack Group NyashTeam

Cyber threat analysts at F6 have uncovered and helped dismantle a large domain network operated by NyashTeam, a Malware-as-a-Service (MaaS) group that provides malicious tools and hosting infrastructure to cybercriminals. The group’s services have facilitated attacks in over 50 countries, including Russia, and have now been significantly disrupted following domain takedown efforts.
Background: Malware Marketplace
Active since at least 2022, NyashTeam offers a suite of low-cost malware products and infrastructure-as-a-service to a Russian-speaking clientele. The group distributes popular malware variants—DCRat and WebRat—via Telegram bots and dedicated websites, while also offering domain registration, hosting, and customer support through plugins and user guides.
F6 reports that over 110 .ru domains linked to NyashTeam were blocked in July 2025, following a coordinated takedown operation. Four additional domains in non-.ru zones remain under suspension review.
Low-Cost Subscriptions Fuel Demand
NyashTeam's appeal lies in its affordability and ease of access:
- DCRat – A remote access trojan (RAT) offering full control over infected devices — ₽349/month
- WebRat – A stealer that extracts browser-stored passwords, cookies, and autofill data — ₽1,199/month
- Web hosting – ₽999 for two months of infrastructure hosting
Payments are accepted via Russian payment services and various cryptocurrencies, further anonymizing the transactions.
Distribution: YouTube and GitHub Abuse
The malware is typically propagated through social engineering on trusted platforms:
- YouTube: Fake or hijacked accounts promote "game cheats," "cracks," and other pirated tools. Download links redirect to malware-laden file-sharing platforms.
- GitHub: Malicious repositories disguise payloads as cracked utilities or game hacks to lure unsuspecting developers and gamers.
These vectors allow wide-scale distribution with minimal technical effort, especially among younger or less security-conscious users.
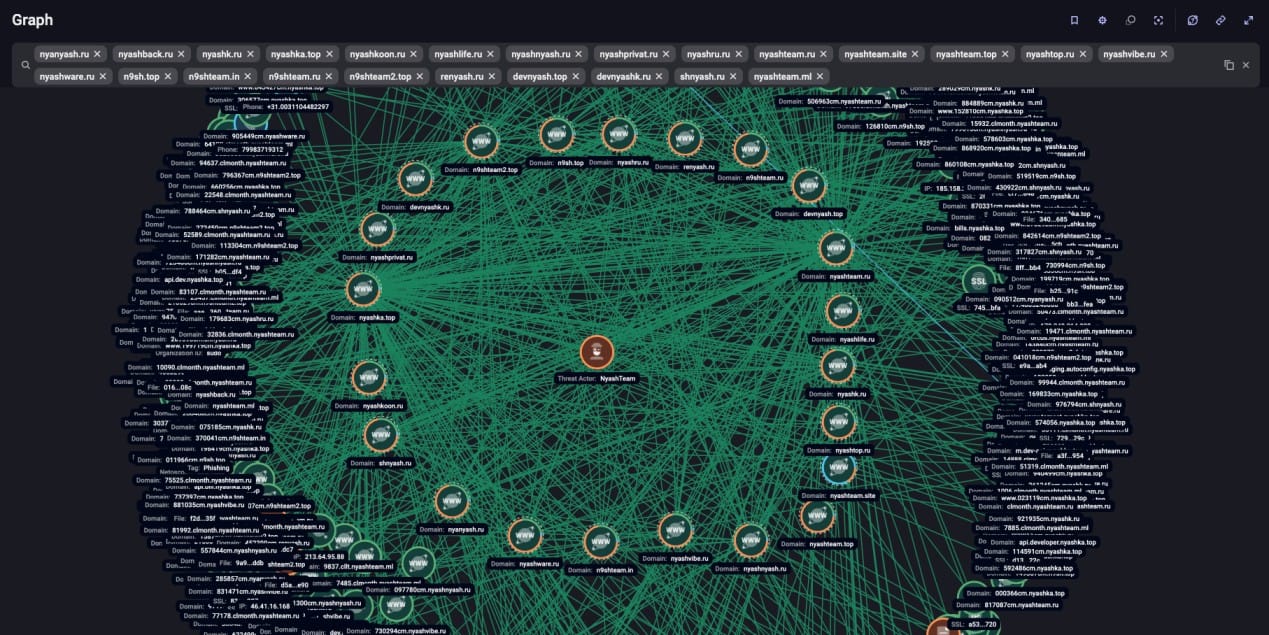
Domain Infrastructure: Hundreds Registered
Since 2022, NyashTeam has registered over 350 second-level domains, with a spike in activity during December 2024 and early 2025. Most were registered under the .ru TLD, using naming conventions tied to their brand and tools:
nyashteam[.]runyanyash[.]ruwebrat[.]rudcrat[.]sitenyashback[.]runyashka[.]top
The infrastructure supported both malware command-and-control (C2) and MaaS service delivery.
Targeted Attacks and Response
In 2024, NyashTeam affiliates used DCRat in phishing campaigns targeting Russian firms in logistics, energy, geology, and IT. These targeted intrusions were often disguised as routine business communications.
In response, F6’s CERT division submitted malicious domain data to the .RU/.РФ Domain Coordination Center, leading to the takedown of more than 110 domains. Additionally, a Telegram channel distributing WebRat’s source code and four hacker tutorial videos were successfully removed.
Expert Insight
"The NyashTeam case proves that the infrastructure behind Malware-as-a-Service groups can be identified and neutralized," said Vladislav Kugan, Threat Intelligence Analyst at F6.
"Disrupting domain operations has already degraded their service delivery and made it harder for affiliates to distribute malware."
Key Takeaways
✔ MaaS distribution: NyashTeam sells DCRat and WebRat via Telegram and dedicated domains
✔ Cheap pricing: Malware packages start at ₽349/month
✔ Exploiting trusted platforms: Malware spread via fake GitHub repos and YouTube videos
✔ Significant takedown: 110+ .ru domains blocked as of July 21, 2025
✔ Russian targets: Attacks focused on domestic infrastructure and corporate networks
Final Recommendation
Avoid downloading “cracks,” “cheats,” or pirated tools from unverified sources. Organizations should monitor for domain activity related to NyashTeam’s infrastructure and update threat intelligence feeds accordingly.




