eSIM Vulnerabilities Allow Card Cloning and User Surveillance

Researchers from AG Security Research have uncovered serious vulnerabilities in eSIM technology, affecting billions of devices worldwide. The flaw lies in the eUICC software package developed by Kigen, a key player in the embedded SIM ecosystem.
The Rise of eSIM—and Its Security Risks
Embedded SIM cards (eSIMs) are rapidly replacing physical SIM cards in smartphones and IoT devices. At the heart of this system is the eUICC (embedded Universal Integrated Circuit Card), which allows devices to remotely install SIM profiles and switch between mobile network operators.
According to Kigen, by December 2020, more than 2 billion eSIMs were in use globally, particularly across IoT deployments.
The Flaw in GSMA TS.48 Test Profile
A security advisory issued by Kigen last week confirmed that a vulnerability affects the GSMA TS.48 Generic Test Profile (versions 6.0 and earlier)—a specification used in eSIM compliance testing.
Researchers found that some mobile operators deploy test profiles for Kigen’s eUICC that use default, hardcoded secret keys to protect eSIM data. If an attacker gains physical access to a target device, they can extract this key and use it to sign and deploy malicious Java Card applets. These applets can then attack the Java Card Virtual Machine (VM) on the eUICC chip.
The updated GSMA TS.48 v7.0 addresses the flaw by restricting test profile usage and disabling remote applet installation. Older versions have now been deprecated.
Exploitation Risks: Cloning, Backdoors, and Surveillance
While exploitation requires physical access to the device and access to publicly known keys, the consequences are significant. A successful attack could allow:
- Installation of malicious Java Card applets
- Extraction of Kigen’s eUICC identification certificate
- Uploading of arbitrary, unencrypted carrier profiles
- Undetected profile modifications across devices
In effect, attackers could clone eSIMs, manipulate mobile connectivity, or covertly surveil users.
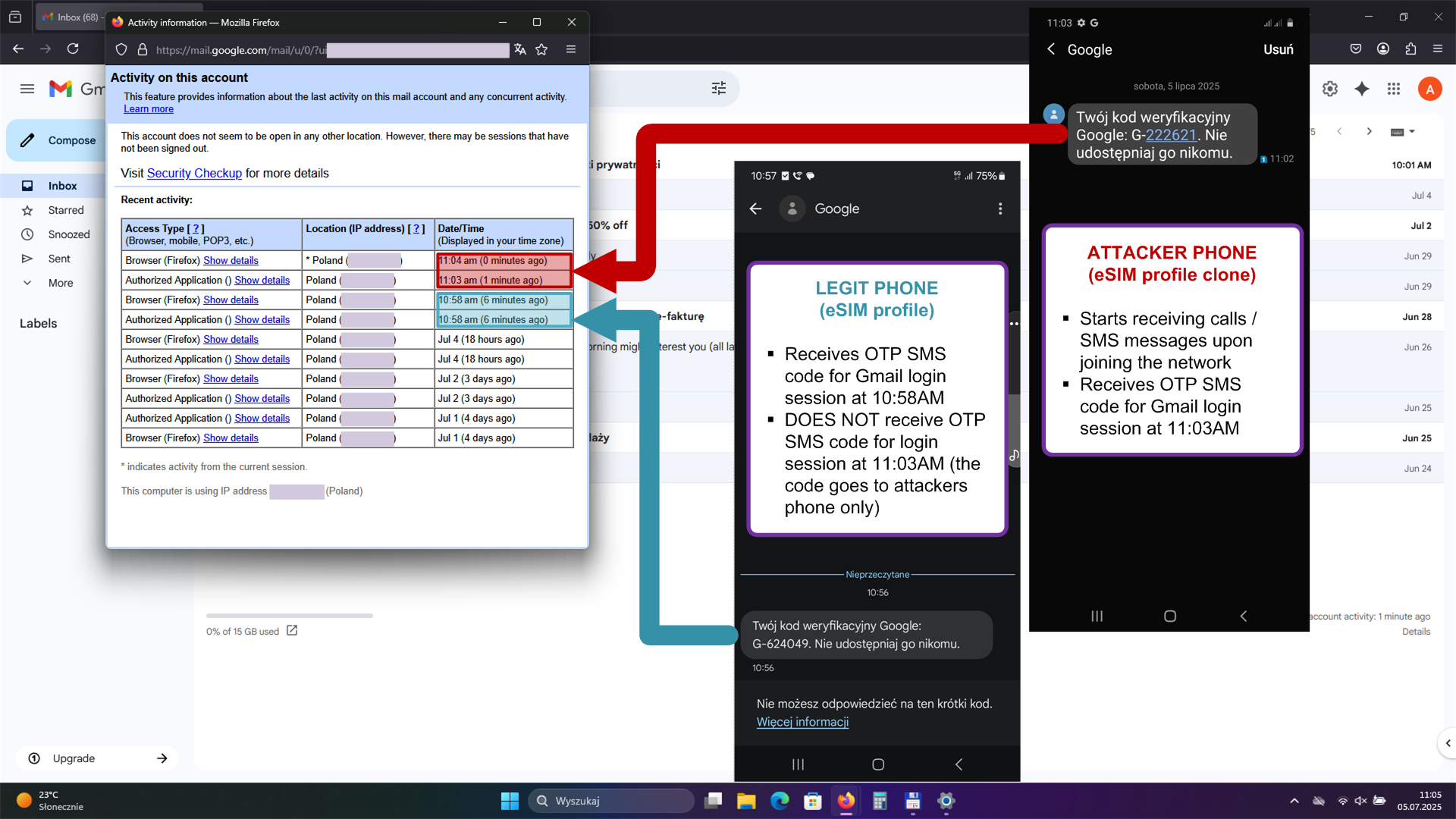
Linked to Previous Java Card Vulnerabilities
AG Security Research notes this study builds on a 2019 analysis of Oracle Java Card, which exposed multiple flaws enabling the deployment of persistent backdoors. One such flaw also affected Gemalto SIM cards, another Java Card-based product.
These earlier vulnerabilities allowed attackers to:
- Compromise the Java Card VM’s memory protection
- Gain full access to card memory
- Bypass applet firewalls
- Execute unauthorized native code
Although Oracle dismissed the issues at the time, AG Security Research now confirms these were genuine security vulnerabilities with real-world implications.
APT Groups Could Weaponize These Flaws
Despite requiring technical expertise and physical access, researchers warn that Advanced Persistent Threat (APT) groups could realistically exploit these flaws to:
- Clone eSIMs
- Install persistent backdoors
- Intercept and monitor all communications on the device
While this particular research focuses on Kigen’s implementation, other eUICC vendors may also be at risk due to the shared Java Card architecture.
A Fundamental Architectural Flaw?
Security researchers emphasize the broader risk:
“A loaded profile could potentially be modified in a way that the operator loses control—no remote management, no ability to disable or revoke it. The operator might receive completely false status reports while all activity is being monitored. In our view, the ability to compromise any operator’s eSIM profiles by hacking just one eUICC or stealing a single GSMA eUICC certificate is a serious architectural flaw in the eSIM ecosystem as a whole.”
$30,000 Bug Bounty
For exposing these critical vulnerabilities, AG Security Research received a $30,000 reward through Kigen’s bug bounty program.
Final Word
This report shines a spotlight on critical, low-level vulnerabilities in modern eSIM infrastructure. The findings underscore the need for stronger protections against SIM cloning, persistent malware, and unauthorized surveillance—especially as eSIM adoption becomes ubiquitous in both personal and industrial devices.
Stay informed—secure-by-design must start at the chip level.




