.es Domains Become 19 Times More Popular Among Phishers

Cybersecurity researchers at Cofense report a dramatic rise in phishing campaigns leveraging .es domains, which are officially reserved for Spanish-language websites or entities based in Spain. The use of these domains by cybercriminals has surged 19-fold since the beginning of 2025, making .es the third most exploited top-level domain (TLD)—surpassed only by .com and .ru.
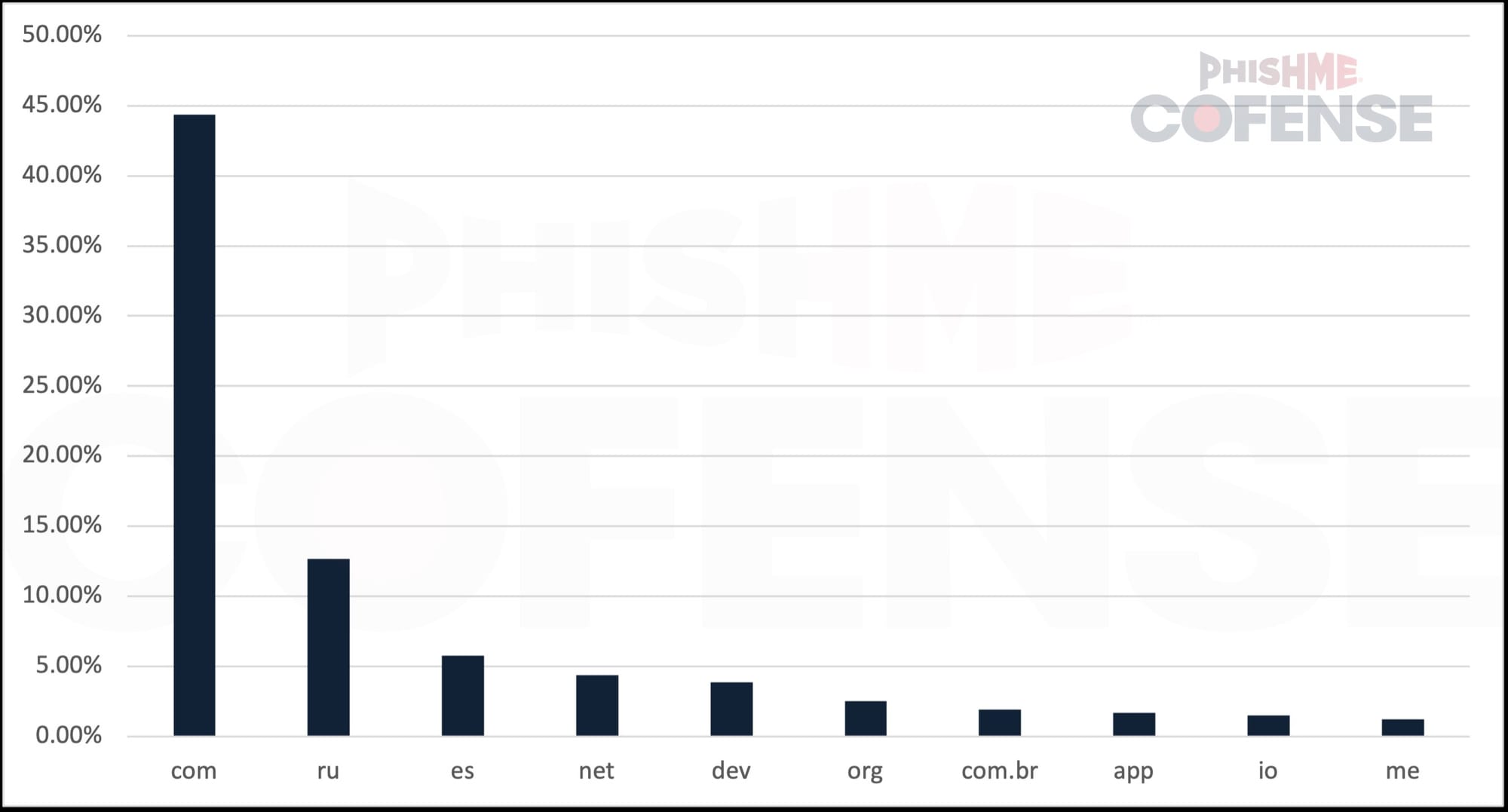
Sharp Rise in Abuse Since Early 2025
The abuse of .es domains began escalating in January 2025. By May 2025, Cofense had identified:
- 447 primary .es domains
- 1,373 subdomains
All of which were actively hosting malicious content.
Attack Breakdown
The vast majority of these attacks are aimed at credential theft:
- 99% of malicious
.espages were phishing sites designed to steal usernames and passwords. - 1% delivered remote access trojans (RATs), including:
- ConnectWise RAT
- Dark Crystal RAT
- XWorm
Attack Methods
Email Lures
Roughly 95% of phishing attempts impersonated Microsoft, using deceptive messages related to HR notifications, shared documents, or security alerts. These emails were notably more sophisticated than typical phishing spam, featuring polished branding and realistic pretexts.
Automated Domain Generation
Most malicious .es domains were not created manually but generated via automated scripts—often producing randomized, meaningless strings such as:
ag7sr[.]fjlabpkgcuo[.]esgymi8[.]fwpzza[.]esmd6h60[.]hukqpeny[.]esshmkd[.]jlaancyfaw[.]es
These types of domains are commonly used in phishing-as-a-service (PhaaS) operations, allowing attackers to quickly rotate links and evade detection.
Why the .es Domain?
Cofense researchers have yet to determine why .es has become a preferred choice. While .com and .ru remain consistent go-to domains for phishing, other TLDs typically fluctuate by region and quarter. The widespread use of .es appears to be part of a broader tactic—not limited to a single threat group.
“If only one threat actor or hacking group were abusing .es domains, the impersonated brands would likely reflect their specific preferences. But since we see no deviation from typical phishing patterns, this suggests .es abuse is becoming a widespread tactic—not limited to a few specialized groups.” — Cofense
Cloudflare’s Role
Another key trend: nearly 99% of malicious .es domains rely on Cloudflare, often using Cloudflare Turnstile CAPTCHA to make phishing pages appear more legitimate and delay detection.
“Cloudflare recently simplified web deployment via CLI and [.pages.dev],” researchers note. “But it’s unclear if this attracted attackers, or if lax abuse reporting policies played a role.”
Key Takeaways
- .es domains now rank third among the most abused TLDs for phishing.
- Most attacks are highly automated, using randomized domains and Microsoft impersonation.
- Cloudflare infrastructure is heavily used—possibly due to ease of setup or insufficient abuse controls.
- Organizations should implement URL filtering, train users on phishing awareness, and verify any Microsoft-related login requests.




