Dozens of Docker Hub Images Still Infected with xz Utils Backdoor

Security analysts at Binarly have identified at least 35 Docker Hub images still infected with the backdoor that compromised xz Utils last year. Researchers warn this poses a serious supply chain risk to users, organizations, and their data.
Supply Chain Risk in CI/CD Pipelines
Many CI/CD pipelines, developers, and production systems pull images directly from Docker Hub, using them as base layers for their own containers. If these images are compromised, every dependent build inherits the vulnerability—or even the malicious code—without the maintainer’s knowledge.
Recap: The xz Utils Backdoor (CVE-2024-3094)
Discovered accidentally in 2024, the xz Utils backdoor shocked the open-source community.
- CVSS score: 10.0 (critical)
- Impact: liblzma, a core component in most Linux distributions (Debian, Fedora, OpenSUSE, Red Hat) and macOS applications.
- Attack method: Threat actors spent years infiltrating the xz Utils maintainer team (Lasse Collin) before planting the backdoor.
- Payload: The malware hijacked OpenSSH’s RSA decryption function (
RSA_public_decrypt), enabling root-level remote code execution if the attackers possessed a specific private key.
Current Threat: Lingering Infected Images
Binarly’s research found 35+ publicly available Docker images still containing the compromised xz Utils versions. Some derivative images were also built on these infected bases, creating a cascade of contamination across the Docker ecosystem.
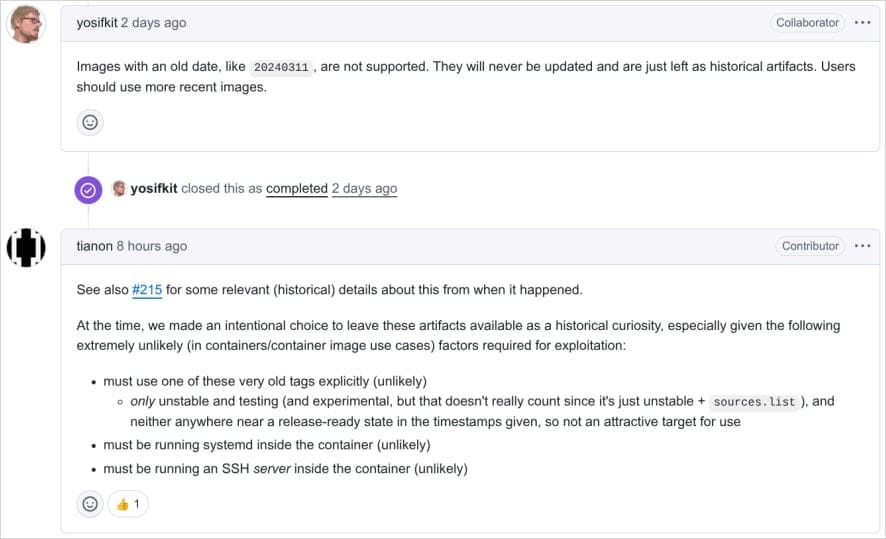
Debian’s Controversial Decision
Debian has intentionally kept infected 64-bit images in Docker Hub as “historical artifacts,” arguing exploitation is unlikely because:
- The container must be running sshd.
- Attackers require network access to the container’s SSH service.
- They must possess the specific private key that triggers the backdoor.
Binarly criticized this approach, warning that public availability still risks accidental downloads or automated inclusion in CI/CD pipelines.
Key Recommendations
- Verify xz Utils version — ensure it is 5.6.2+ (latest stable: 5.8.1).
- Avoid outdated base images — use only updated, trusted sources.
- Implement binary-level monitoring in CI/CD pipelines, not just version checks.
Broader Implications
The xz Utils incident demonstrates how even short-lived malware can persist in official container images, silently spreading through Docker ecosystems and automated build systems. This underscores the urgent need for continuous binary analysis and strict supply chain governance.
Actionable Takeaway:
- Audit all Docker images for xz Utils versions 5.4.x–5.6.1.
- Replace compromised base layers immediately.
- Enforce supply chain controls to block future threats.




