Critical Zero-Day Vulnerabilities in Microsoft SharePoint Actively Exploited

Two new critical zero-day vulnerabilities in Microsoft SharePoint—CVE-2025-53770 and CVE-2025-53771—have been actively exploited since late last week, with at least 85 servers compromised worldwide.
Background: From ToolShell to Active Exploitation
In May 2025, researchers at Viettel Cyber Security chained two SharePoint flaws—CVE-2025-49706 and CVE-2025-49704—to create a remote code execution (RCE) attack dubbed ToolShell, which they demonstrated at the Pwn2Own Berlin competition.
Although Microsoft released patches for these flaws in July, attackers have since bypassed the fixes using new exploits. These newly discovered vulnerabilities, assigned CVE-2025-53770 (CVSS 9.8; patch bypass for CVE-2025-49704) and CVE-2025-53771 (CVSS 6.3; patch bypass for CVE-2025-49706), are now being used in real-world attacks targeting on-premises SharePoint servers.
Note: Microsoft 365’s SharePoint Online is not affected.
Microsoft’s Response
In an official blog post, Microsoft confirmed the active exploitation of these vulnerabilities:
“Microsoft is aware of active attacks targeting on-premises SharePoint Server users, exploiting vulnerabilities that were partially mitigated in the July security updates.”
To address the new issues, Microsoft has released update KB5002768 for SharePoint Subscription Edition. Patches for SharePoint 2019 and 2016 are still pending.
Interim Mitigation Measures
For administrators unable to apply the update immediately, Microsoft recommends:
- Applying the latest SharePoint updates
- Enabling AMSI (Antimalware Scan Interface) integration
- Deploying Microsoft Defender on all servers
Additionally, Microsoft advises replacing ASP.NET keys after enabling AMSI or installing updates, which may prevent attackers from executing payloads—even post-compromise.
Indicators of Compromise
Administrators should inspect their servers for the following suspicious file:
makefileCopyEditC:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx
The presence of this file suggests that the server has already been breached.
Discovery Timeline and Exploit Mechanics
The first signs of the attacks were detected by Eye Security, a Dutch cybersecurity firm. On July 18, 2025, an EDR (Endpoint Detection and Response) system at one of their clients flagged suspicious activity linked to a malicious .aspx file.
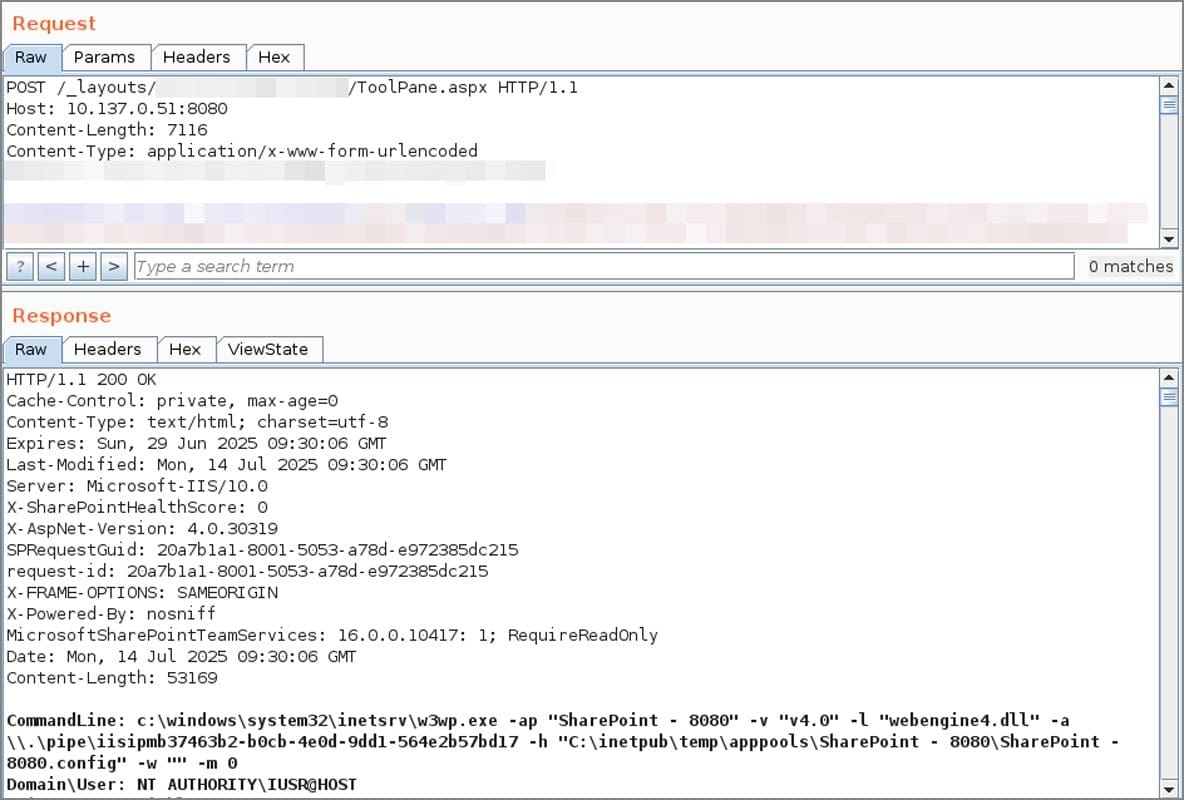
Further investigation of IIS logs revealed a POST request to:
bashCopyEdit/_layouts/15/ToolPane.aspx
with a referrer pointing to:
bashCopyEdit/_layouts/SignOut.aspx
Eye Security confirmed the ToolShell exploit was in use, referencing previous technical disclosures by CODE WHITE GmbH and Soroush Dalili.
How the Exploit Works: ViewState Forgery
The root of the attack lies in ViewState manipulation, a feature in ASP.NET (the framework underlying SharePoint) used to preserve UI state between page loads.
If ViewState protection is misconfigured or if the server’s ValidationKey is leaked, attackers can forge ViewState data to inject and execute malicious code during deserialization—a classic remote code execution technique.

Scope of the Attack
According to Eye Security:
- At least 54 organizations have been affected globally
- Over 85 SharePoint servers have been compromised
Affected Organizations Include:
- A private university in California
- A commercial energy provider (California)
- A government healthcare agency
- A commercial AI technology developer
- A fintech firm based in New York
- A government agency in Florida
Google TAG Confirms the Threat
Google’s Threat Analysis Group (TAG) has also issued an alert:
“Google TAG has observed attackers using these vulnerabilities to deploy web shells and steal cryptographic secrets from victim servers. This provides persistent unauthorized access and poses a significant risk to affected organizations.”
Final Thoughts
The exploitation of CVE-2025-53770 and CVE-2025-53771 underscores an uncomfortable truth: even patched systems can be vulnerable if adversaries are determined and the original fix is incomplete. This incident is yet another reminder of the importance of:
- Applying patches quickly
- Validating server hardening
- Monitoring logs and endpoint behavior
- Performing key rotations after potential compromise
For organizations running on-premises SharePoint, now is the time to act—not wait.




