Cloudflare and Cybersecurity Company Zscaler Affected by the Salesloft Drift Attack

Dozens of major companies have now confirmed they were impacted by the Salesloft Drift compromise. Among the victims are cybersecurity leaders Zscaler and Palo Alto Networks, SaaS providers Workiva, PagerDuty, and Exclaimer, internet giant Cloudflare, and several others.
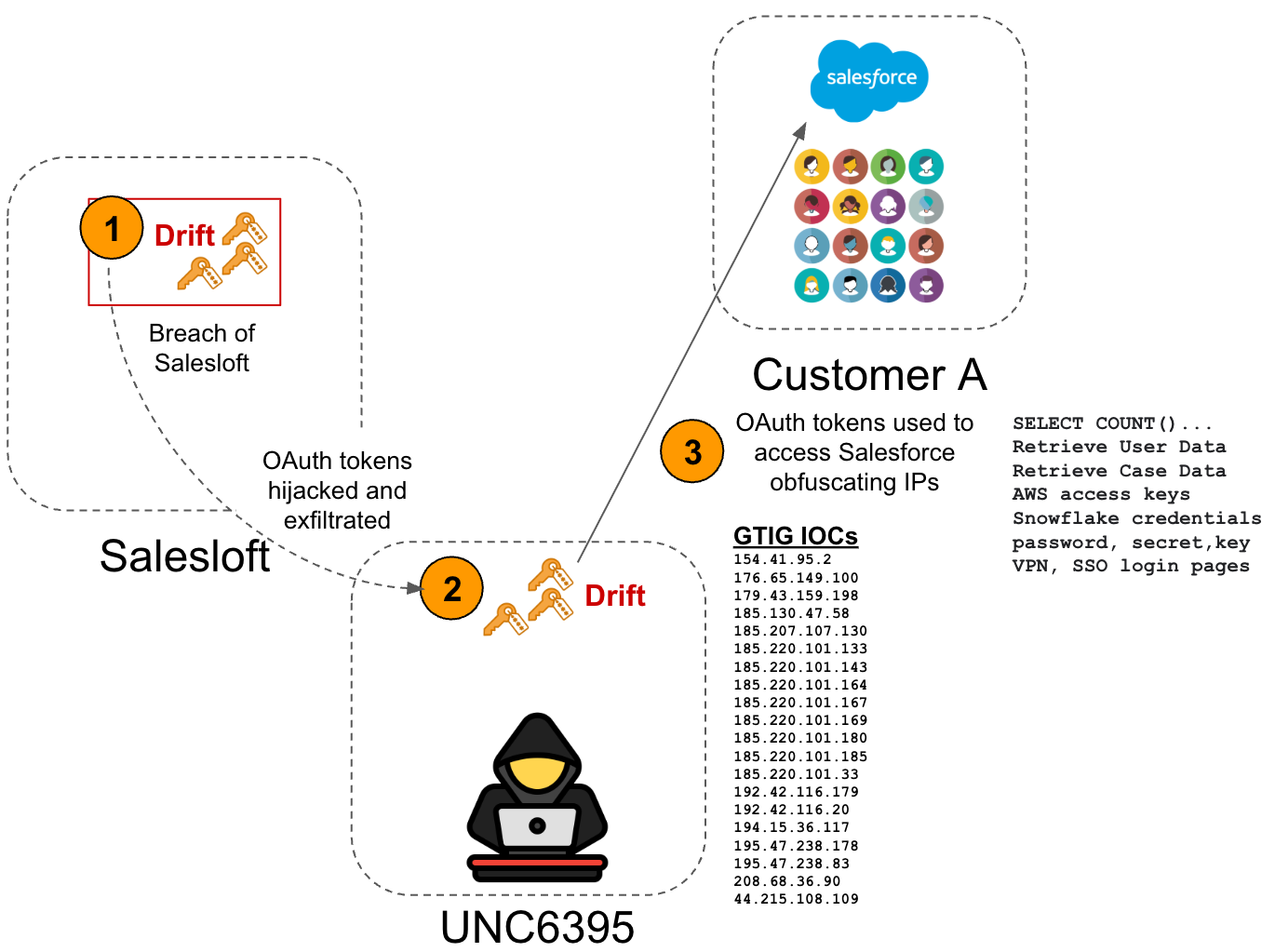
Background on the Attack
Last week, it was revealed that hackers compromised the Salesloft sales automation platform, stealing OAuth and refresh tokens from its Drift AI agent—a third-party integration tool for Salesforce. The campaign ran from August 8 to August 18, 2025, allowing attackers to obtain Salesforce tokens and extract customer data.
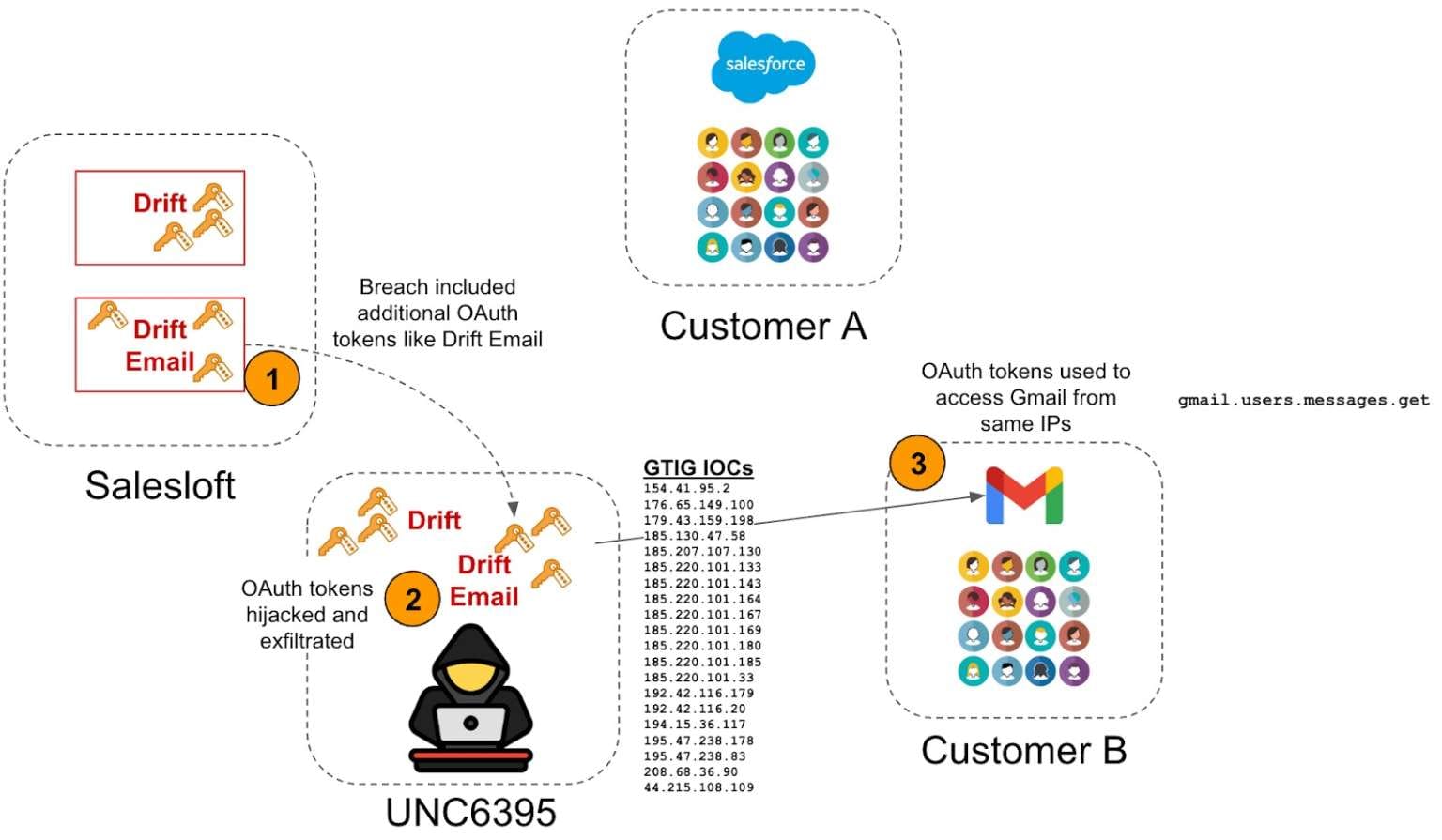
Google later warned that the incident was massive, also affecting Google Workspace data. Analysts recommended that all companies using Drift-Salesforce integrations treat their Salesforce data as compromised.
Zscaler Confirms Data Exposure
Zscaler reported that attackers gained unauthorized access to its Salesforce instance, exposing customer information.
“Unauthorized third parties gained access to the Salesloft Drift credentials of its customers, including Zscaler,” the company stated. “These credentials allowed the threat actors to gain limited access to some Salesforce data of Zscaler.”
Exposed data included:
- Names, email addresses, job titles, and phone numbers
- Regional information
- Zscaler product licensing and commercial data
- Content of some customer support requests
Zscaler emphasized that no products, services, or infrastructure were affected. The company found no evidence of misuse but advised customers to remain alert to potential phishing and social engineering attempts.
Palo Alto Networks Impacted
Palo Alto Networks confirmed it was one of “hundreds of victims” of the attack. Like Zscaler, the breach was limited to Salesforce and did not affect other systems or products.
“We quickly contained the incident and disabled the application in our Salesforce environment,” the company said. “Our investigation confirms that this situation did not impact any Palo Alto Networks products, systems, or services.”
The attackers accessed contact details, account information, and sales records. Support case data included only text comments—no files or attachments. Palo Alto Networks has begun notifying affected customers.
Cloudflare Reports Stolen API Tokens
Cloudflare disclosed that its Salesforce environment, used for internal case management and customer support, was also compromised.
Attackers accessed 104 Cloudflare API tokens. By September 2, Cloudflare had revoked all affected tokens and notified impacted customers. No suspicious use of the tokens has been detected so far.
“Most of the stolen information consists of customer contact details and support case content,” the company explained. “However, some interactions may have contained configuration details and sensitive information, including access tokens.”
Cloudflare urged customers to treat any information shared through its support system—such as logs, tokens, or passwords—as potentially compromised and to reset credentials.
“We believe this incident was not an isolated event,” Cloudflare warned. “Given that hundreds of organizations were impacted, the threat actors are likely to use the information obtained to launch targeted attacks against the customers of affected organizations.”
Growing List of Victims
Other confirmed victims include SaaS platforms Workiva, PagerDuty, and Exclaimer; cybersecurity firms Tanium, SpyCloud, and Astrix Security; and cloud provider Cloudinary. The list continues to expand.
Attribution Dispute
While Google attributes the attacks to UNC6395, the hacking collective ShinyHunters has claimed responsibility in interviews with Bleeping Computer. However, attribution remains unclear.
In recent months, Salesforce-related data leaks linked to ShinyHunters have affected Adidas, Qantas, Allianz Life, LVMH brands (Louis Vuitton, Dior, Tiffany & Co.), Cisco.com, Chanel, and Pandora.




