Citizen Lab: VPN Apps from Google Play Use the Same Hardcoded Password

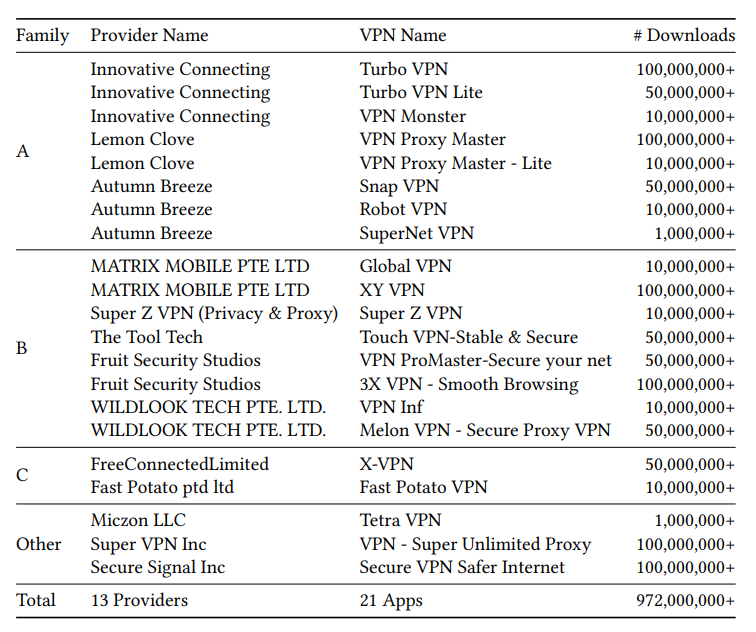
Researchers at Citizen Lab have revealed that more than 20 VPN applications available on Google Play contain serious security flaws that compromise user privacy and could allow attackers to decrypt transmitted data. Collectively, these apps have been downloaded nearly 1 billion times (972 million installations).
Interconnected Providers
Although these VPN providers publicly claim to be independent, Citizen Lab found clear signs of interconnection, with overlapping infrastructure, shared code, and deliberate attempts to obscure their true affiliations.
The new report builds on earlier findings that linked three Singapore-based providers—Innovative Connecting, Autumn Breeze, and Lemon Clove—to a Chinese national. Analysts have now uncovered deeper overlaps between their applications, as well as ties to additional VPN developers.
Shared Code and Hardcoded Passwords
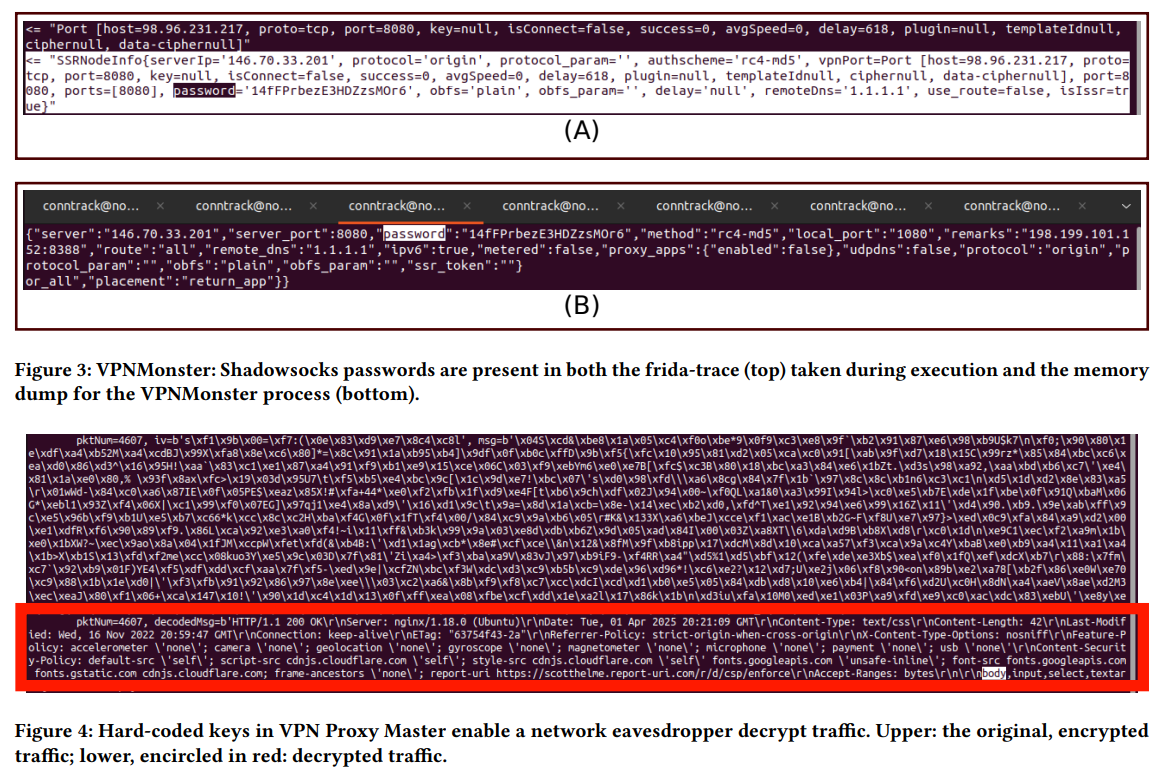
Citizen Lab found that eight VPN applications developed by Innovative Connecting, Autumn Breeze, and Lemon Clove use nearly identical code, dependencies, and—critically—the same hardcoded password. This flaw could allow attackers to decrypt all of a user’s network traffic. Together, these apps account for more than 330 million installations on Google Play.
The apps in question include:
- Turbo VPN
- Turbo VPN Lite
- VPN Monster
- VPN Proxy Master
- VPN Proxy Master – Lite
- Snap VPN
- Robot VPN
- SuperNet VPN
All eight support both IPsec and Shadowsocks protocols and employ anti-analysis techniques to evade automated security checks.
Shadowsocks Weaknesses
All three providers were previously connected to Qihoo 360, a Chinese cybersecurity company sanctioned by the U.S. in 2020. Their VPN services rely heavily on Shadowsocks, a proxy protocol originally designed to bypass China’s “Great Firewall.”
Researchers emphasize that Shadowsocks was not designed for privacy protection. It uses symmetric encryption and outdated ciphers, making it vulnerable to multiple types of attacks. The inclusion of hardcoded passwords, combined with flaws in the protocol’s interaction with operating system connection tracking, makes these apps susceptible to connection hijacking and traffic manipulation.
Wider Network of Linked Apps
Citizen Lab also identified five additional providers—Matrix Mobile PTE LTD, ForeRaya Technology Limited, Wildlook Tech PTE LTD, Hong Kong Silence Technology Limited, and Yolo Mobile Technology Limited—that appear to be connected to the original trio. Their VPN apps, which total more than 380 million downloads, share the same obfuscation techniques, protocol choices, and even backend IP infrastructure.
Two more companies, Fast Potato Pte. Ltd and Free Connected Limited, distribute VPN clients built on the same proprietary protocol implementation, further expanding the ecosystem of vulnerable services.
Risks to Users
Across the board, researchers found that these VPN apps:
- Contain weak or obfuscated encryption keys
- Use the same hardcoded Shadowsocks password
- Secretly collect user location data
- Remain vulnerable to connection-injection and packet-injection attacks
Using the shared password, Citizen Lab confirmed that all three original providers rely on a centralized infrastructure, reinforcing the conclusion that the apps are not truly independent.
Takeaway
“The security issues we have uncovered impact users, providers, and app stores alike,” Citizen Lab concluded. “At the very least, privacy-conscious VPN users should avoid using Shadowsocks—including apps from these developers—since Shadowsocks was designed not for privacy protection, but for circumventing censorship.”




