Atomic Stealer for macOS Now Includes a Persistent Backdoor

Security researchers have uncovered a new, more dangerous version of the Atomic Stealer (also known as AMOS) targeting macOS systems. This latest variant comes equipped with a built-in backdoor, giving attackers persistent, long-term access to compromised machines—even after reboot.
Backdoor Discovery and Global Reach
MacPaw’s threat intelligence team analyzed the backdoor following a tip from independent security researcher g0njxa. According to their report, the new component:
- Executes arbitrary commands remotely
- Survives reboots via persistence mechanisms
- Maintains indefinite control over infected systems
“AMOS campaigns now target over 120 countries,” the researchers warn. “The most affected regions include the U.S., France, Italy, the U.K., and Canada. The backdoored Atomic variant grants full access to thousands of Macs worldwide.”
What Is Atomic Stealer?
First identified in April 2023, Atomic Stealer is a Malware-as-a-Service (MaaS) operation sold via Telegram for $1,000 per month. Its primary functions include:
- Exfiltrating local files from macOS systems
- Stealing credentials from browsers
- Harvesting data from cryptocurrency wallets
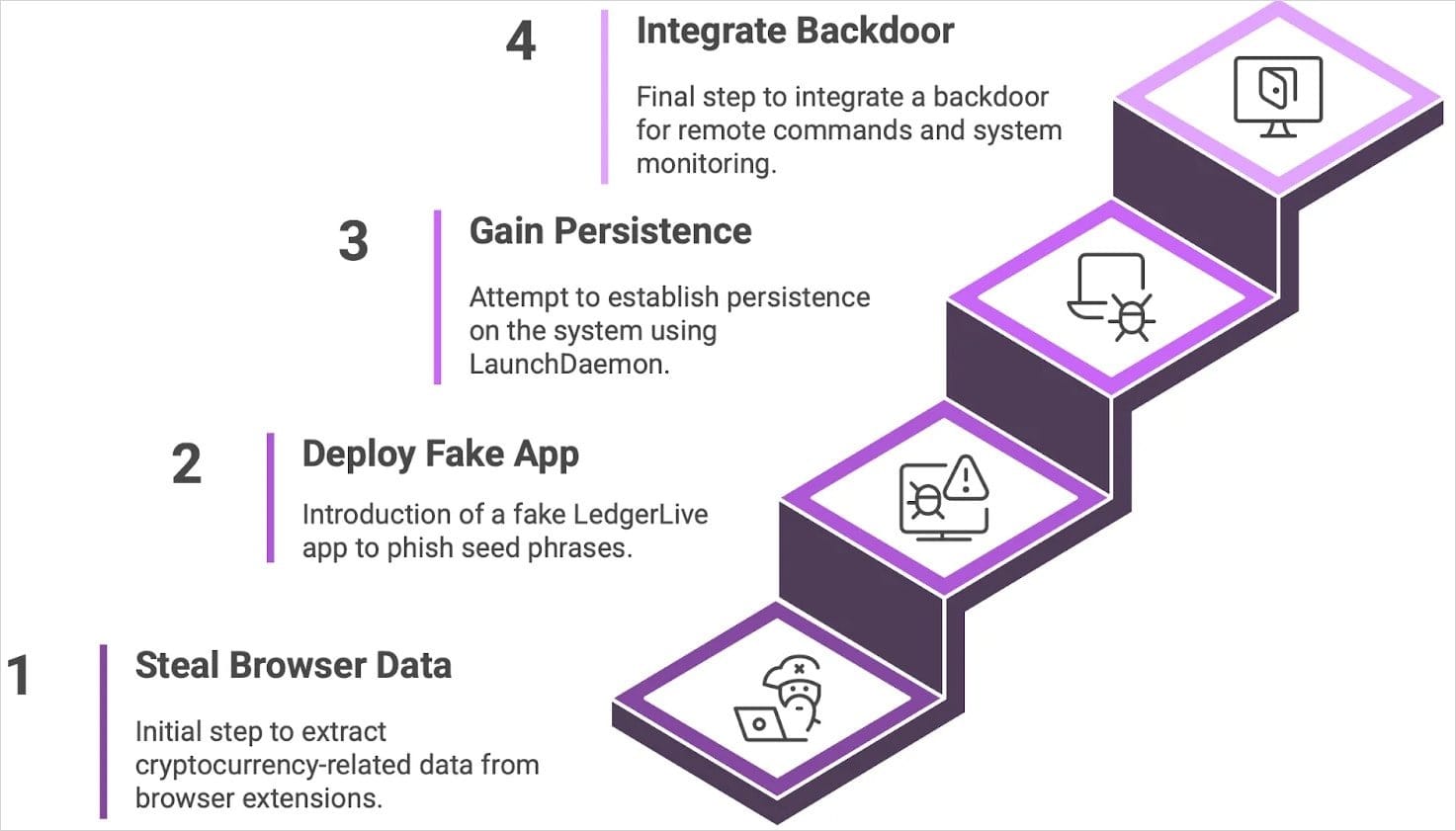
Notable Campaigns
- November 2023: Featured in the ClearFake malware campaign
- September 2024: Used by the Marko Polo hacking group in a large-scale attack on Apple computers
Evolving Tactics: From Piracy Sites to Phishing Lures
According to Moonlock analysts, Atomic’s operators have shifted away from distributing the malware through fake pirated software sites. The latest campaigns now rely on:
- Cryptocurrency-themed phishing emails
- Fake job interview invitations targeting professionals

How the New Backdoor Works
The updated malware architecture includes:
- A persistent backdoor
- LaunchDaemon-based startup to survive reboots
- Unique victim IDs for tracking
- A new command-and-control (C2) infrastructure
Infection Chain Breakdown
- The main payload, a hidden binary named
.helper, is stored in the victim’s home directory. - A hidden wrapper script
.agentcontinuously executes.helperunder the user’s context. - Persistence is established via an AppleScript-created LaunchDaemon (
com.finder.helper). - During infection, the malware prompts the user for their password to escalate privileges.
- The PLIST file is altered and ownership is changed to
root:wheelto ensure execution on reboot.
Backdoor Capabilities
Once active, the backdoor allows attackers to:
- Execute remote shell commands
- Log keystrokes
- Deploy additional malware payloads
- Move laterally across networks
Evasion Techniques
To avoid detection, Atomic employs several stealth features:
- Detects sandbox or virtualized environments via
system_profiler - Obfuscates key strings to evade static analysis
This new variant significantly raises the threat level of Atomic Stealer, extending its impact from data theft to full system compromise. Security teams are urged to monitor for signs of compromise and ensure macOS systems are hardened against persistence techniques like LaunchDaemons and credential theft.




