Android Backdoor Disguised as Antivirus Targets Russian Businesses

Researchers at Dr. Web have uncovered a sophisticated Android backdoor targeting Russian business representatives. The malware offers extensive surveillance and data theft capabilities, including:
- Recording conversations
- Streaming live camera footage
- Stealing data from messengers and browsers
- Keylogging
Malware Evolution and Targeting
Dubbed Android.Backdoor.916.origin, the Kotlin-based malware first appeared in January 2025. Multiple variants have been observed (details listed in IoCs), suggesting its use in targeted attacks rather than mass-distribution campaigns.
Distribution and Disguise
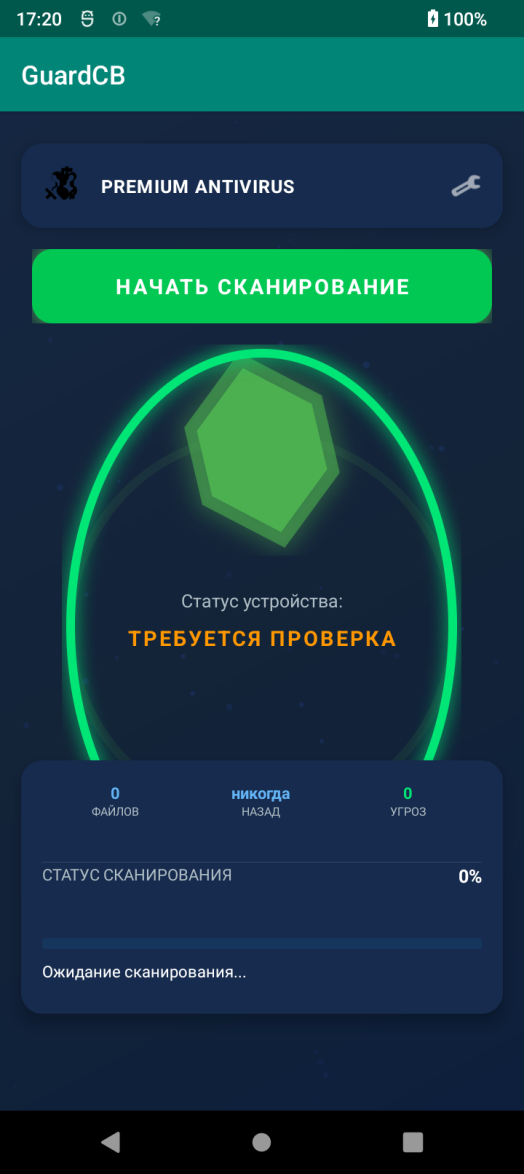
The malware is delivered via malicious APK files shared over messaging platforms, posing as an antivirus app called GuardCB.
- The icon mimics the Russian Central Bank’s emblem on a shield.
- The interface is Russian-only, reinforcing its local targeting.
Other versions impersonate Russian law enforcement, using filenames such as:
- SECURITY_FSB
- “ФСБ” (FSB)
Fake Antivirus Behavior
Once launched, the app simulates a device scan, displaying a pre-set “threat detection” rate of up to 30%. The number of “detected threats” is randomized between 1 and 3.

Invasive Permissions
On startup, the malware requests:
- Microphone and camera access
- SMS, contacts, and call log access
- Device administrator rights
- Accessibility Services (for keylogging and anti-removal features)
Spying Capabilities
The backdoor connects to its command-and-control (C2) servers and can:
- Exfiltrate SMS, contacts, call logs, and location data
- Stream microphone and camera feeds in real time
- Record the screen
- Steal images from device storage
- Execute shell commands
Messenger & Browser Data Theft
It specifically targets data from:
- Telegram
- Google Chrome
- Yandex Browser / Yandex Start
- Gmail
Self-Protection Mechanism
If instructed by operators, the malware uses Accessibility Services to block uninstallation attempts, ensuring persistence on the infected device.
C2 Infrastructure
The malware is configured to use multiple C2 servers (up to 15 hosting providers), although this feature is currently inactive.
Mitigation
Dr. Web has notified domain registrars of the malicious infrastructure.
Recommended defenses include:
- Avoid sideloading APKs from untrusted sources.
- Closely monitor app permission requests—especially for Accessibility Services.
- Use reputable mobile security software to detect and block threats.




