Akamai Experts Detail Two New Methods to Disrupt Cryptojacking Botnets

Researchers at Akamai have outlined two novel techniques that can be used to disable cryptocurrency-mining botnets.
The methods exploit design flaws in common mining algorithms to halt cryptojacking operations.
"We developed two techniques that abuse mining technologies and pool policies, allowing us to degrade the efficiency of mining botnets—even to the point of complete shutdown—forcing attackers to make radical infrastructure changes or abandon their campaigns altogether," the experts explain.
The approach leverages the Stratum mining protocol, effectively blocking the attacker’s mining proxy or wallet, rendering their operation useless.
1. The "Bad Shares" Technique
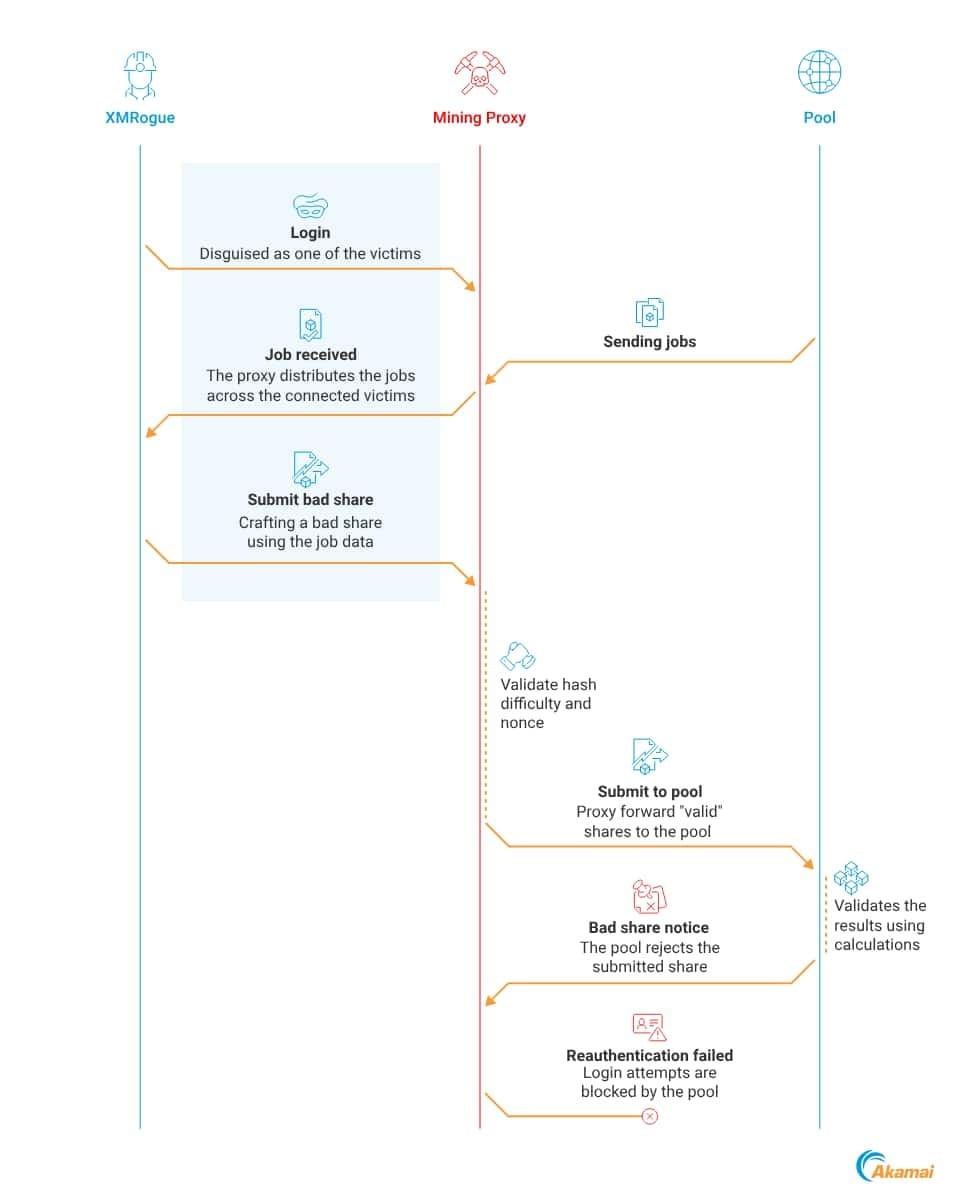
The first method, dubbed Bad Shares, involves getting a mining proxy banned from the network, which stops operations and reduces the victim’s CPU load from 100% to 0%.
While mining proxies act as intermediaries—hiding the attacker’s mining pool and wallet addresses—they can become a single point of failure if compromised.
"The idea is simple: by connecting to a malicious proxy as a miner, we can submit invalid job results—'bad shares'—that bypass checks and reach the pool," Akamai explains. "A series of these bad submissions will trigger a proxy ban, effectively shutting down the entire botnet."
This attack requires XMRogue, a tool developed by the researchers to impersonate a miner, connect to the proxy, submit bad shares, and force a ban.
2. Direct Pool Exploitation
The second method targets victims connected directly to a public mining pool (without a proxy). It exploits a common pool policy that temporarily bans a wallet address for one hour if it uses over 1,000 workers.
By flooding the pool with over 1,000 login requests using the attacker’s wallet, the pool will automatically ban it. However, this is not a permanent solution, as the wallet unblocks once the excessive connections stop.
Tested on Monero, Applicable to Other Cryptocurrencies
Akamai confirms these methods have already been used against Monero (XMR) miners but can be adapted for other cryptocurrencies.
"These techniques demonstrate how defenders can disrupt malicious cryptojacking campaigns without affecting legitimate mining pools," the researchers note. "A legitimate miner can quickly recover by changing their IP or wallet locally. But for a botnet operator, recovery is far harder—they’d need to reconfigure the entire network. In some cases, this defense could completely dismantle less sophisticated botnets."
Key Takeaways:
- Bad Shares force a proxy ban, crashing the botnet.
- Worker flooding gets attacker wallets temporarily banned.
- Legitimate miners can recover easily; botnets struggle.
- Already effective against Monero, adaptable to other coins.




