352 Android Apps Infected with IconAds Adware

Security researchers at Human Security have uncovered a massive ad fraud operation dubbed IconAds, involving 352 malicious Android apps previously available on the Google Play Store.
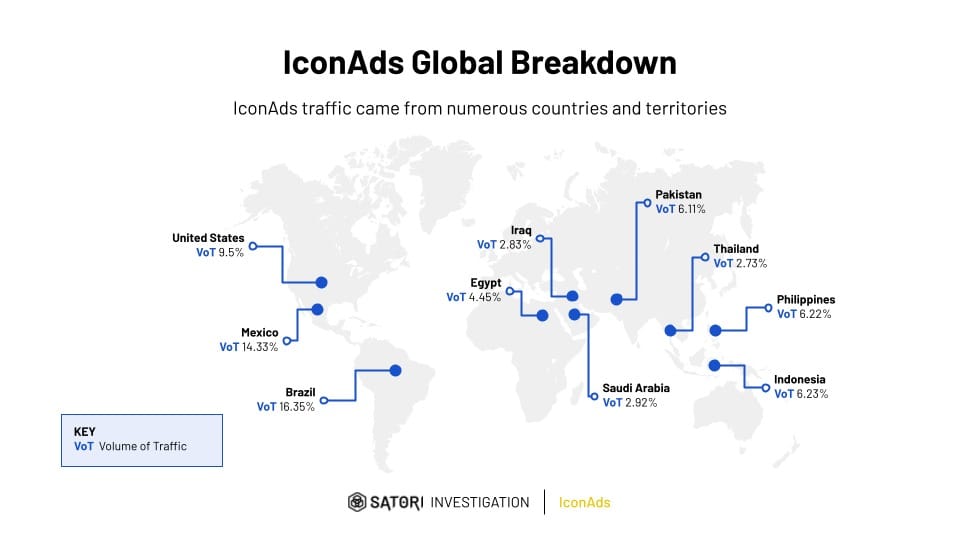
At its peak, the campaign generated over 1.2 billion ad requests per day, primarily targeting users in Brazil, Mexico, and the United States. All known malicious apps have since been removed by Google.
Key Findings
The infected apps used a combination of deceptive tactics to maximize ad revenue while remaining difficult to detect or remove:
- Intrusive out-of-context ads: Displayed ads outside the normal app experience, often interrupting other tasks
- Hidden icons: Removed themselves from the home screen after installation, making uninstallation harder for users
- Play Store impersonation: Some apps masqueraded as Google Play Store or other official apps to gain user trust
How IconAds Operates
Stealth Execution
Once installed, apps used alias components in the Android manifest to appear legitimate during installation—then switched to malicious behavior after launch.
Deceptive Behavior
Some apps redirected users to real apps (like legitimate Google services) to appear functional, while secretly running ad-fraud operations in the background.
Anti-Analysis Techniques
To avoid detection by researchers and automated scanners, IconAds employed multiple evasion methods:
- Play Store verification: Checked if it was installed via Google Play; if not, it disabled malicious functions
- Advanced obfuscation: Code was heavily disguised to prevent reverse engineering or dynamic analysis
A Persistent and Evolving Threat
IconAds is linked to a broader family of Android adware known as HiddenAds and Vapor, active since at least 2019. These variants share common hallmarks:
- Obfuscated network traffic
- Predictable command-and-control (C&C) domain patterns
- Dynamic switching of app icons and names to confuse users and security tools
What’s Next?
Researchers warn that IconAds will likely return in new forms:
- New malicious apps will continue to bypass Play Store defenses
- Future versions may use even more sophisticated obfuscation
- The scale of fraud indicates financial incentive for ongoing development
Recommendations
To protect yourself:
- Avoid sideloading apps—only install from trusted developers
- Regularly check installed apps (Settings → Apps), especially if you see unexpected ads
- Report suspicious apps directly through Google Play Protect
Have you encountered persistent adware or strange pop-ups on your Android device?
Share your experience in the comments below.




